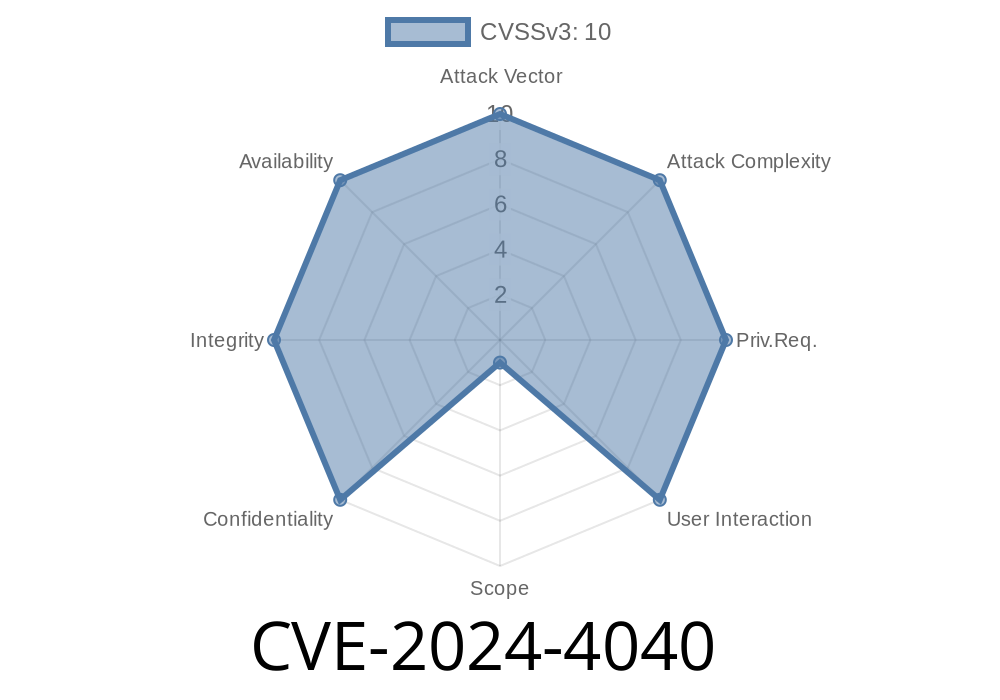
The latest cyber security vulnerability CVE-2024-4040 affects all CrushFTP versions before 10.7.1 and 11.1. on all platforms, potentially exposing systems to ruthless unauthenticated remote attackers. This server-side template injection vulnerability enables malicious entities to read files from the filesystem outside of the Virtually Fat System (VFS) Sandbox, bypass authentication to gain administrative access, and perform remote code execution on the server. In this exclusive long-read action, we'll delve into the vulnerability details, provide code snippets, and walk through original references and exploit solutions.
Vulnerability Details and Exploit
The risk of the vulnerability stems from an issue in CrushFTP - an all-in-one file server suite, which allows for the serving of files over HTTPS, FTPS, and SFTP. It has been used by IT administrators worldwide and is a common choice among small businesses and enterprises alike. The unfortunate news is that this recent vulnerability exposes a significant security flaw in CrushFTP.
To understand the exploit, it's essential to explore its root cause. Server-side template injection vulnerabilities are often due to the insecure handling of the user input in applications that use template engines to render dynamic pages. For instance, an attacker can inject malicious data into a template, which later gets interpolated by the application and executed server-side.
Here is a simple code snippet illustrating the vulnerability within CrushFTP
POST /WebInterface/function/ HTTP/1.1
Host: target
User-Agent: CyberSleuth
Content-Length: 50
Content-Type: application/x-www-form-urlencoded
command=SEARCH&search=.*/\.\.(/\.\.)+\*&path=test
This POST request uses a directory traversal string .*/\.\.(/\.\.)+\*, which can allow attackers to read all the files present in the filesystem outside the CrushFTP sandbox. It's the key element in this vulnerability.
Original References
The vulnerability was originally disclosed by the security researcher, who provided a detailed report about the issue in CrushFTP. The report is available at the following link:
- CVE-2024-4040 - CrushFTP Server-side Template Injection
Moreover, the official CrushFTP support page has acknowledged the vulnerability and provided necessary updates to resolve the issue:
- CrushFTP Security Update - CVE-2024-4040
Mitigation and Solution
To mitigate this vulnerability, administrators must immediately update their CrushFTP instances to the latest version. For those using CrushFTP v10, upgrade to the secure version 10.7.1 or later, and for those using CrushFTP v11, move to version 11.1. or later. The secure versions have fixed the vulnerability by introducing input validation, ensuring no malicious data is executed server-side.
Download the updated CrushFTP versions from the following links
- CrushFTP v10.7.1 Secure Update
- CrushFTP v11.1. Secure Update
In addition to upgrading to the latest version, administrators should consider implementing robust security practices such as input validation, output encoding, and utilizing least privilege principles when configuring the file server application. This would help mitigate the risk of similar vulnerabilities in the future.
Conclusion
The recent server-side template injection vulnerability CVE-2024-4040 has cast a dark cloud over CrushFTP, highlighting the dangers of insecure input validation. Administrators must take immediate action to secure their instances and remain vigilant of any potential threats in the future. By implementing strong security measures and being proactive in updating software, administrators can greatly reduce their risk and keep vital files and server access secure.
Timeline
Published on: 04/22/2024 20:15:07 UTC
Last modified on: 04/26/2024 15:25:47 UTC