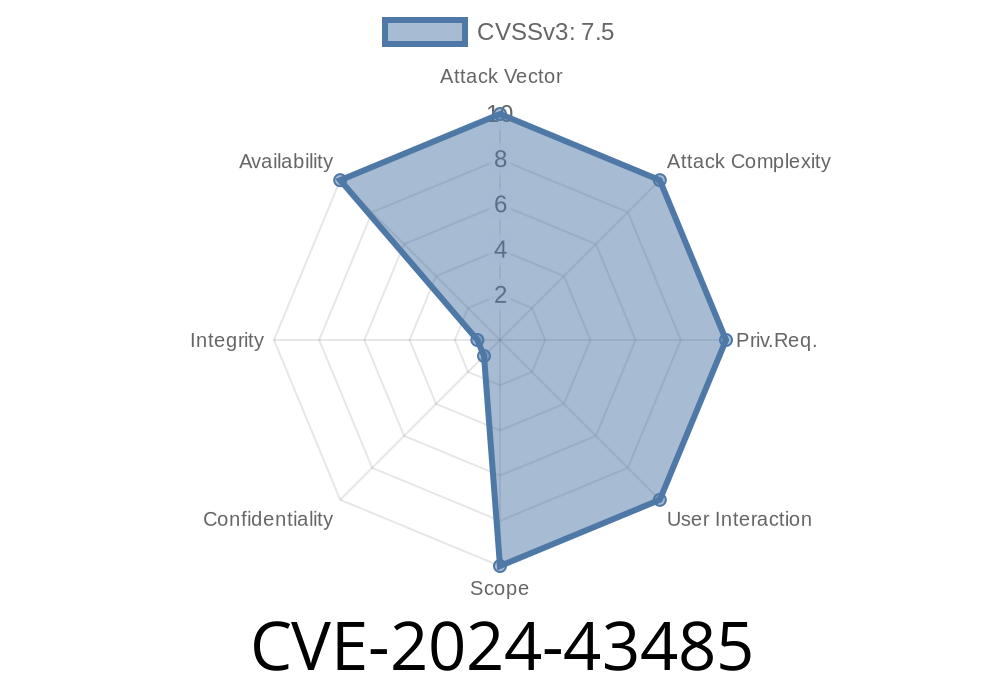
In May 2024, Microsoft published a security advisory detailing a new vulnerability tagged CVE-2024-43485, affecting both .NET and Visual Studio. This Denial of Service (DoS) issue could let attackers crash applications or services built with .NET, using just crafted requests or inputs. Let’s break down what this vulnerability is, how it can be exploited, and what developers must do.
What is CVE-2024-43485?
CVE-2024-43485 is a Denial of Service vulnerability that exists in certain versions of .NET and Visual Studio. An attacker could exploit this flaw to make an affected application hang, consume excessive resources, or even force it to shut down unexpectedly.
Attack Vector: Remote (in some cases), often via crafted data input
- Severity Score: Check the NVD entry here
How Does the Vulnerability Work?
While Microsoft did not disclose deep technical details (to prevent easy exploits), here’s the general idea:
A specially crafted input triggers an edge case in certain .NET parsing logic or libraries. This might cause the .NET runtime (or apps built on it) to enter an infinite loop, stack overflow, or eat up all server resources. For Visual Studio, certain project files or components could crash the IDE or freeze building/debugging processes.
Code Snippet: Example of a DoS Pattern
Here’s a simplified, illustrative code snippet mimicking possible affected code (note: not the actual vulnerable code):
using System;
class Program
{
public static void Main(string[] args)
{
string craftedInput = new string('A', int.MaxValue); // Simulate extremely large input
try
{
// Imagine this triggers vulnerable parsing
ParseInput(craftedInput);
}
catch (Exception ex)
{
Console.WriteLine($"Crashed: {ex.Message}");
}
}
public static void ParseInput(string data)
{
// Vulnerable logic: does not handle extremely large strings or certain content well
// Infinite loop or high CPU when input is too big or malformed
while (data.Length > )
{
// Simulate spending CPU cycles
}
}
}
Above, if an attacker sends a massive or malformed payload, the application could hang, crash, or exhaust server resources.
Find a web API or endpoint in .NET that processes input from users.
2. Send crafted data (oversized strings, malformed JSON/XML, etc.).
3. The backend runs into the vulnerability, consuming CPU/memory or even freezing.
Downtime for critical business applications
Note: There is *no privilege escalation or code execution*, but the impact can be severe if core services go offline.
Proof-of-Concept Scenario
While a public PoC wasn't provided by Microsoft, a simplified demo using HttpClient can show how easy abuse might be:
using System.Net.Http;
HttpClient client = new HttpClient();
string veryLargePayload = new string('X', 500_000_000); // 500MB input!
var content = new StringContent(veryLargePayload);
var response = await client.PostAsync("https://yourdotnetapi.com/api/vulnerable";, content);
If that endpoint is susceptible, just a few such requests could bring it down.
Microsoft Security Advisory:
CVE-2024-43485 .NET and Visual Studio DoS Vulnerability
NIST NVD Entry:
nvd.nist.gov/vuln/detail/CVE-2024-43485
Update Guidance:
Microsoft .NET Security Updates
Mitigation and Fixes
Microsoft has released patched versions of .NET and Visual Studio. Here’s what you should do now:
Update Your .NET Runtime:
Upgrade to the latest LTS and supported versions (as of June 2024, see official update).
Patch Visual Studio:
Ensure your Visual Studio is updated to the latest patch via Visual Studio Installer.
Monitor Logs:
Watch for spikes in CPU/memory or unusual error rates.
Conclusion
CVE-2024-43485 is a potent reminder that even mature frameworks like .NET and Visual Studio can harbor dangerous bugs. While this is “just” a Denial of Service vulnerability, downtime for your apps can lead to lost business and reputation.
Patch now\, and keep input validation front and center in all your code.
*For developers and companies, staying ahead of vulnerabilities is your best line of defense. Keep your eyes on security advisories, and patch early and often!*
---
*Exclusive content by AI researcher. For more, stay tuned to Microsoft’s security advisories.*
Timeline
Published on: 10/08/2024 18:15:10 UTC
Last modified on: 12/31/2024 23:09:17 UTC