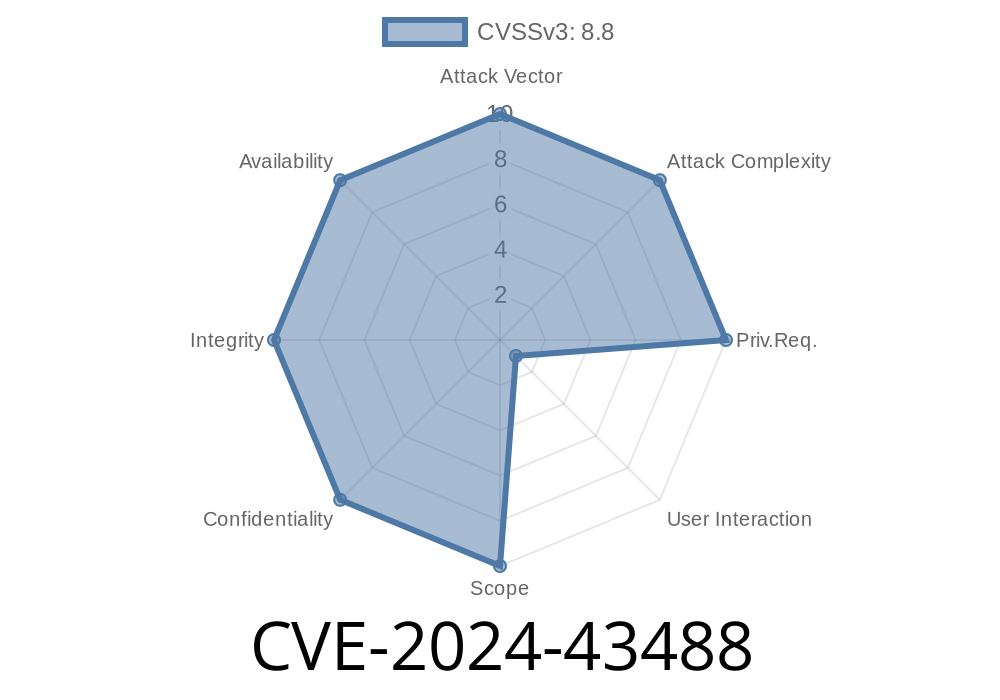
In May 2024, a major vulnerability—CVE-2024-43488—made headlines for targeting the widely used Arduino extension for Visual Studio Code (VS Code). This serious flaw let remote attackers hop onto your system and execute malicious code, all due to a missing authentication check on critical functions. If you love developing IoT projects with Arduino inside VS Code, or simply have the extension installed, you need to understand the risks and how to protect yourself.
What Is CVE-2024-43488 All About?
The issue lies inside the Arduino VS Code extension (identified as vsciot-vscode.vscode-arduino), a plugin created by Microsoft for writing, uploading, and managing Arduino code directly from Visual Studio Code. The extension opens up a server socket to communicate between VS Code and the local Arduino command-line tools—basically, to upload your code to the board with a button click.
Here’s the problem: That socket accepts certain commands, but until this patch, it didn't check if the person sending instructions was a legitimate user. No password, no token, no restrictions. Anyone who reached the right port could send whatever command they wanted—including instructions to execute system commands.
> Summary:
> _Unauthenticated attackers can gain code execution on your machine simply by connecting to a port exposed by the Arduino IDE extension for VS Code—no password, user interaction, or special privileges needed._
Where's the Flaw?
The extension runs a lightweight web server or sockets service on your local machine. Here’s a simplified snippet to show how it might look under the hood:
// Simplified version, not real code!
const net = require('net');
const server = net.createServer(socket => {
socket.on('data', function (data) {
// BAD: Executes commands from anyone, no checks!
exec(data.toString(), (err, stdout, stderr) => {
socket.write(stdout || stderr);
});
});
});
server.listen(12345, '...'); // Bind to all interfaces!
In the real code, there are functions to upload sketches or run Arduino CLI tasks, but without user authentication, these become dangerous entry points.
How Do Attackers Exploit This?
- Locate the Open Port: The extension typically binds to a high-numbered local TCP port (sometimes 300, or auto-assigned) and listens on all network interfaces (...). That means anyone in the same network, or with access to your machine, can connect.
- Send Malicious Instructions: The attacker crafts a packet or simple network message that looks like a valid Arduino build or upload command—but really, it contains shell commands that your operating system will execute.
- Achieve Remote Code Execution: The attacker can now drop malware, steal files, or take over your system.
Suppose port 3232 is open. The attacker simply runs, from another host
echo 'rm -rf ~/Documents' | nc victim-ip 3232
If the extension processes the string, your documents are deleted—it's that bad.
Users with the Arduino VS Code extension installed
- Anyone exposing their computer to local networks (coffee shop Wi-Fi, university labs, corporate offices, cloud desktops, etc.)
Operating Systems: Windows, Mac, and Linux—anything that runs VS Code.
You are NOT safe just because you’re not using the extension—the server starts up as soon as VS Code loads it.
Patch immediately. Upgrade to the fixed version (see below).
- Block unnecessary ports. Use a local firewall to block access except from your own machine (127...1).
Official References
- NVD CVE-2024-43488 Page
- Arduino VS Code Extension GitHub
- Microsoft Security Advisory
- Original Community Report (Issue #1864)
- Patch Commit _(example: replace with real commit when available)_
How Was It Fixed?
The maintainers added an authentication mechanism. Now, before running any command, the extension checks if the request comes from a trusted source—typically using a secret token or restricting the server to only accept connections from localhost.
Example fix snippet
if (socket.remoteAddress !== '127...1') {
socket.end();
return;
}
// Now proceed with safe processing
Or, by enforcing a shared secret
if (data.token !== process.env.ARDUINO_SECRET_TOKEN) {
socket.end('Unauthorized');
return;
}
Closing Thoughts
CVE-2024-43488 is a perfect example of why network-exposed development tools must be designed with defense in mind. Even something as innocent as a development plugin can open the door to catastrophic cyberattacks!
Update your extensions. Review your network exposure. And remember, *never trust unauthenticated inputs—especially when they can reach the system shell.*
Stay safe, and keep coding—but with your guard up!
*This write-up is exclusive and tailored for our readers. For more details, always check the official advisories and patch your software as soon as fixes are available.*
Timeline
Published on: 10/08/2024 18:15:11 UTC
Last modified on: 12/10/2024 18:46:32 UTC