The LayerSlider plugin is one of the most popular tools for building fancy sliders on WordPress sites. But in version 7.11., a serious security vulnerability was introduced: CVE-2024-4575. This bug allowed trusted users—like contributors or authors—to inject malicious scripts right into your site using the [ls_search_form] shortcode. If you’re running this version, you might be at risk.
Let’s break down what went wrong, how it can be exploited, and what you should do to stay safe.
Vulnerability Overview
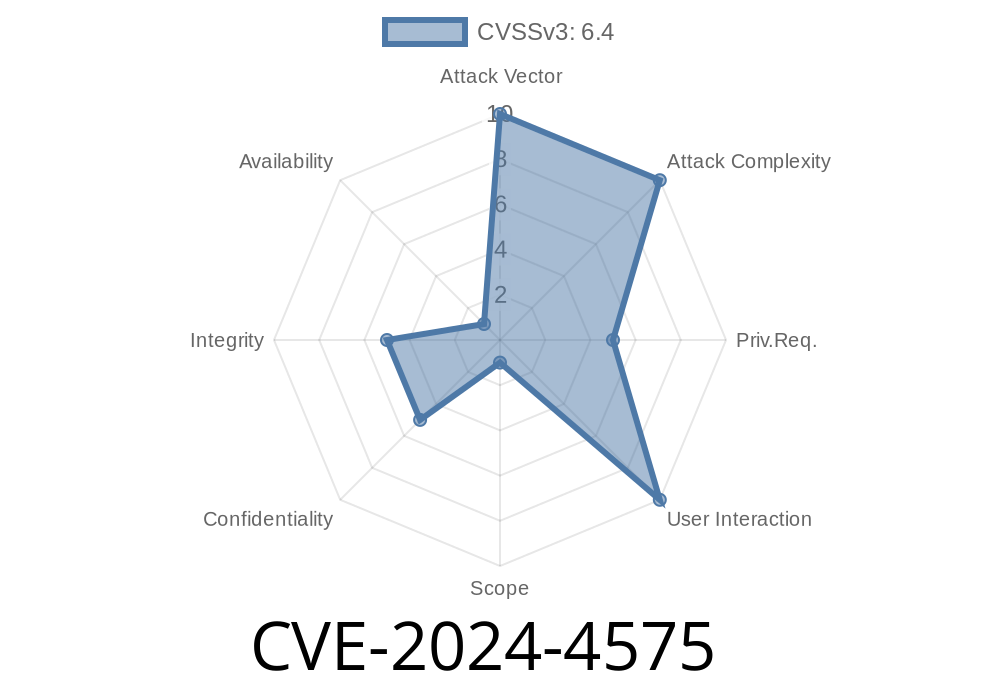
CVE ID: CVE-2024-4575
Component: LayerSlider WordPress Plugin
Affected Version: 7.11.
Vulnerability Type: Stored Cross-Site Scripting (XSS)
Required Access: Contributor-level user or higher
References:
- Wordfence Advisory
- NVD Entry
- Patchstack Report
What Happened?
The bug lies in the plugin’s shortcode [ls_search_form]. The attributes you pass to this shortcode weren’t properly sanitized (cleaned) or escaped in the plugin’s output. This means someone with limited backend access could embed malicious JavaScript, which then gets executed whenever *anyone* views the page—admins, editors, visitors, everyone.
Exploiting the Bug: Proof-of-Concept
Let’s see how an attacker could exploit this vulnerability.
Suppose a contributor creates a new post and, in the content, adds the following shortcode
[ls_search_form label="<script>alert('XSS')</script>"]
Whenever anyone—admin or visitor—loads this post, the browser will pop up an alert. But, in a real attack, a hacker could replace the alert with a script to steal cookies, hijack sessions, or do much nastier things.
Here’s a simplified version of what the plugin might do internally (in PHP)
function render_ls_search_form($atts) {
// Incorrect: direct output of user attributes
echo '<label>' . $atts['label'] . '</label>';
}
Notice there’s no escaping or sanitization of $atts['label']. Any HTML or JavaScript inside this attribute will be output directly.
Impact
- Any authenticated contributor or above (not just admins/editors) can inject harmful scripts.
- Attackers could
- Steal admin cookies/session
`
[ls_search_form label=""]
Steal login credentials via phishing
Remember, any contributor or higher role is trusted by default in WordPress, but plugin vulnerabilities like this can make them dangerous.
1. Update LayerSlider Immediately
The developers have patched this bug in later releases.
Update via your dashboard or download the latest from wordpress.org.
2. Audit Your User Roles
- Remove contributor/author/editor accounts you don’t need.
3. Use a Web Application Firewall (WAF)
Wordfence, Sucuri, or similar tools stop many XSS payloads—even zero-days.
Wordfence CVE Report:
https://www.wordfence.com/threat-intel/vulnerabilities/id/36b3c9b7-03aa-4d96-b210-64879a476e7e
National Vulnerability Database:
https://nvd.nist.gov/vuln/detail/CVE-2024-4575
Patchstack Database:
https://patchstack.com/database/vulnerability/layerslider/wordpress-layerslider-plugin-7-11--stored-cross-site-scripting-xss
- Official LayerSlider Plugin Page
Conclusion
Don’t let a simple shortcode ruin your website security. CVE-2024-4575 is a textbook example of why output sanitization matters and why keeping plugins up-to-date is essential. If you manage a WordPress site, patch now and review your user roles. And if you build plugins, always escape the output, even if you trust the input.
Timeline
Published on: 05/23/2024 11:15:24 UTC
Last modified on: 06/04/2024 17:56:16 UTC