Summary:
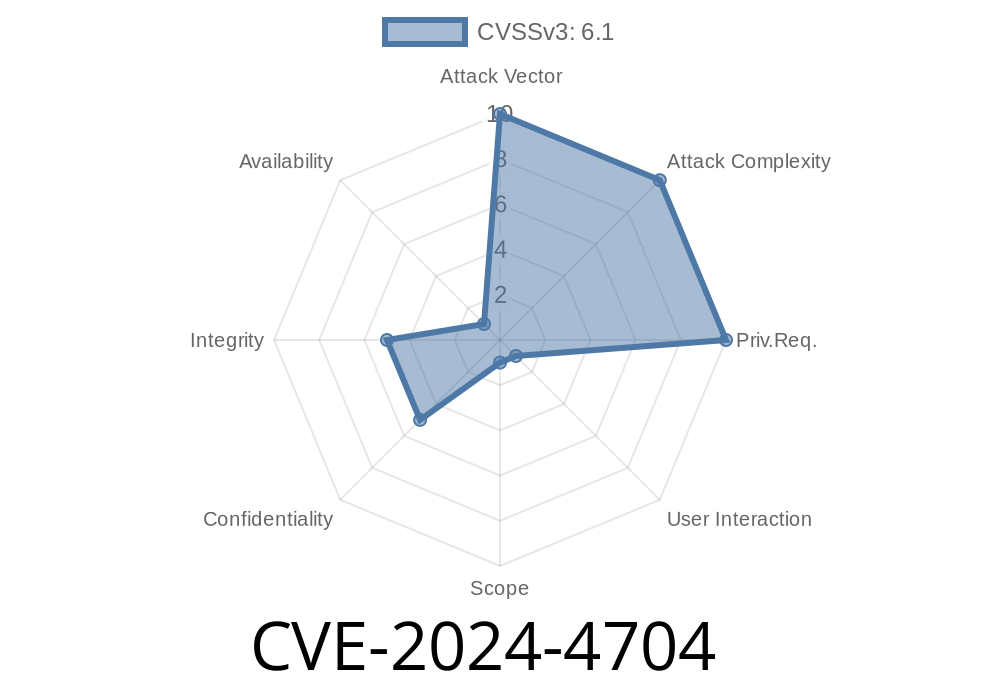
CVE-2024-4704 is a security vulnerability discovered in the popular Contact Form 7 WordPress plugin, specifically in versions before 5.9.5. This flaw enables open redirects, potentially allowing attackers to redirect users to any website with malicious intent. In this article, we’ll break down what this vulnerability is, how it works, and show a simple proof-of-concept (PoC) exploit.
What is an Open Redirect?
An open redirect vulnerability occurs when a web application accepts a URL parameter and redirects the user to the specified address, without proper validation. This means attackers can trick users into visiting dangerous websites simply by clicking an innocent-looking link.
Vulnerable Plugin: Contact Form 7
Contact Form 7 is one of the most widely used contact form plugins for WordPress, with millions of active installations.
Patched version: 5.9.5 (latest at the time of writing)
- CVE identifier: CVE-2024-4704
How does the open redirect happen?
Contact Form 7, when processing form submissions, allows for a redirect_to parameter in some of its components (like AJAX JSON APIs, or certain custom forms). If this value is insufficiently validated, an attacker can set redirect_to to any URL.
Sample vulnerable URL
https://victim-site.com/wp-admin/admin-post.php?redirect_to=https://evil.com
Instead of only allowing internal URLs, the plugin before 5.9.5 would accept and redirect to any user-supplied redirect_to value.
An attacker creates a link like this
https://vulnerable-site.com/wp-admin/admin-post.php?redirect_to=https://evil.com
2. Send to Victims
The attacker sends this link to unsuspecting users via email, social networks, etc.
3. Victim Clicks the Link
When the victim clicks the link, they’re redirected first to vulnerable-site.com, but then immediately bounced to evil.com — an attacker-controlled domain.
This is the simplest demonstration
import requests
target = 'https://vulnerable-site.com/wp-admin/admin-post.php';
payload = {'redirect_to': 'https://attacker.com';}
r = requests.get(target, params=payload, allow_redirects=False)
print("Redirect Location:", r.headers.get('Location'))
Expected Output:
If the site is vulnerable, you'll see
Redirect Location: https://attacker.com
This means the plugin accepts any redirect destination.
Phishing Attacks:
Users can be lured into clicking “safe” links, but end up on malicious websites stealing their data.
Update Promptly:
Upgrade Contact Form 7 to at least version 5.9.5 from your WordPress dashboard or from the official download page.
Review Redirects:
Always validate and sanitize redirect destinations, ensuring only trusted/internal URLs are allowed.
Official Patch:
Read the Contact Form 7 changelog for more about the fix in version 5.9.5.
References
- NVD Entry: CVE-2024-4704
- Contact Form 7 Official Site
- Contact Form 7 WordPress Plugin Download
- Wordfence Advisory on CF7 Vulnerability
Conclusion
CVE-2024-4704 may look simple, but open redirects can deeply impact your website’s reputation and put your users at risk. If you use Contact Form 7, update right now. Remember: even apparently small issues can be keys to bigger attacks!
Timeline
Published on: 06/27/2024 06:15:14 UTC
Last modified on: 07/03/2024 02:07:57 UTC