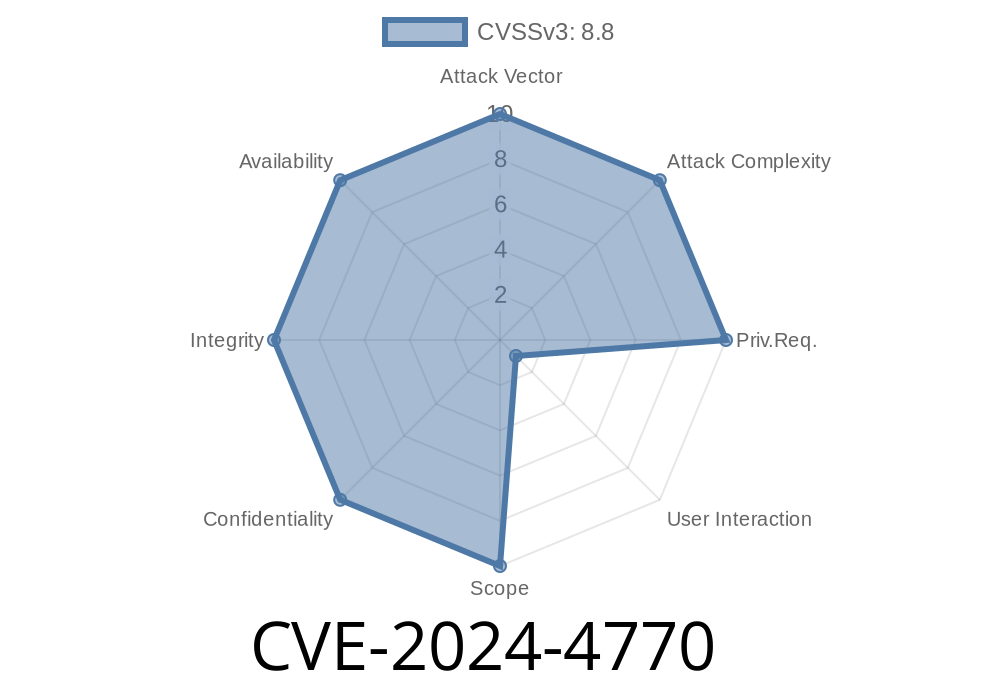
Mozilla has recently disclosed a critical vulnerability (CVE-2024-4770) affecting Firefox versions earlier than 126, Firefox ESR versions earlier than 115.11, and Thunderbird versions earlier than 115.11. The vulnerability occurs when specific font styles are used while saving a webpage to a PDF, potentially leading to a use-after-free crash. In this post, we will explore the details of the flaw, share some code snippets to demonstrate the issue, and offer insights into the exploit.
Vulnerability Details
A use-after-free vulnerability occurs when an application references memory after it has been freed, leading to an application crash, information leakage or even arbitrary code execution.
In the case of CVE-2024-4770, the issue arises while handling certain font styles across different versions of Firefox and Thunderbird. During the rendering process, the affected Mozilla software does not handle object lifetimes correctly, leading to a use-after-free condition while saving a page to a PDF.
It's been found that certain kinds of fonts might trigger an object being mistakenly freed while still in use, risking the integrity and stability of the software in question. Attackers could exploit this flaw to gain remote access to a victim's machine, execute arbitrary code, or cause the target application to crash.
Here's a sample code snippet that demonstrates how the vulnerability might manifest itself
// Load a webpage with a custom font in Firefox or Thunderbird
}
Sample text using the Vulnerable Font
In this example, the 'VulnerableFont' is a custom font that triggers the use-after-free issue while being processed. When a user attempts to save this webpage as a PDF in Firefox or Thunderbird, it leads to a crash or arbitrary code execution.
Mozilla: Mozilla Foundation Security Advisory 2024-08
Link: https://www.mozilla.org/en-US/security/advisories/mfsa2024-08/
CVE-2024-4770 - National Vulnerability Database (NVD)
Link: https://nvd.nist.gov/vuln/detail/CVE-2024-4770
Exploit Details
Currently, there is no public exploit available for this vulnerability. However, considering the impact of a successful exploit, it is crucial for users and administrators to apply security updates that address this vulnerability in affected versions of Firefox and Thunderbird.
Mitigation and Solution
Mozilla has released updated versions of Firefox, Firefox ESR, and Thunderbird to address this critical vulnerability. Users are advised to apply these updates as soon as possible:
Thunderbird: Update to version 115.11 or later
Additionally, users can consider employing safe browsing practices and using security software to protect their devices from potential threats.
Conclusion
CVE-2024-4770 is a critical vulnerability affecting Firefox, Firefox ESR, and Thunderbird that can lead to potentially severe consequences when saving a webpage to PDF using certain font styles. To protect yourself against security risks associated with this flaw, ensure that you are using the most recent versions of the affected software and follow best practices for online safety.
Timeline
Published on: 05/14/2024 18:15:14 UTC
Last modified on: 08/01/2024 20:47:41 UTC