In May 2024, the security community confirmed a new threat targeting one of the world’s most used office tools: Microsoft Excel. This critical vulnerability, labeled as CVE-2024-49026, allows attackers to achieve Remote Code Execution (RCE) by exploiting how Excel improperly handles certain file content. In this post, we’ll explain the vulnerability in plain English, walk through a code example, and look at the potential impact—with reference links so you can dig deeper.
What Is CVE-2024-49026?
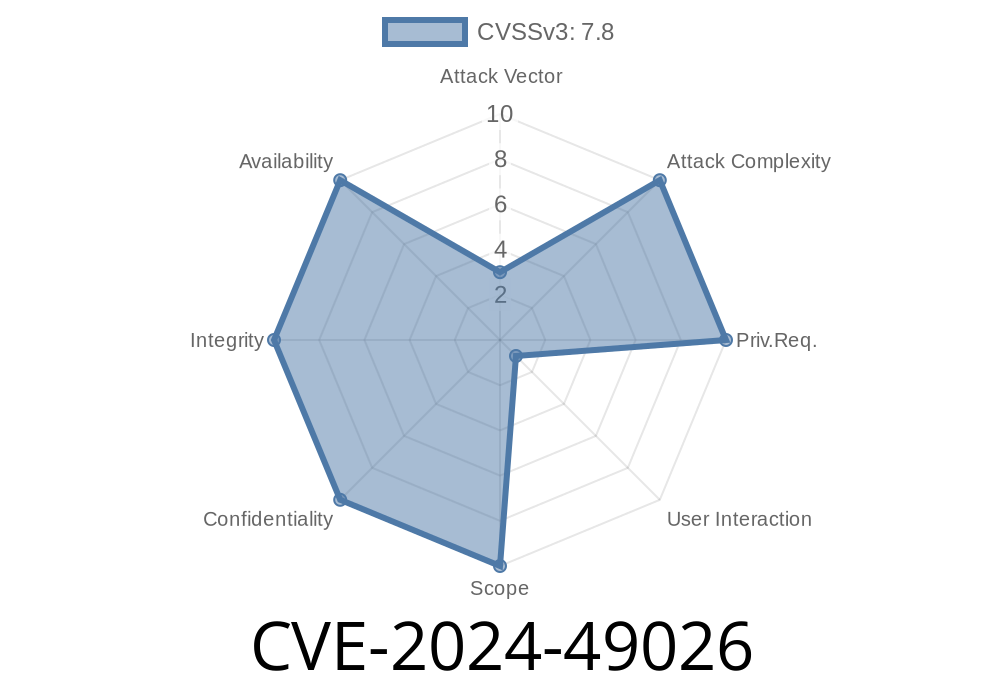
CVE-2024-49026 is a security hole in Microsoft Excel that lets an attacker run malicious code just by getting a user to open a specially crafted Excel file (.xlsx, .xlsm, etc.). If an attacker succeeds, they can potentially take control of the victim’s computer—with the victim’s permissions.
Severity: High
Attack Vector: Email, download links, or shared files
Systems Affected: Supported and possibly some legacy versions of Microsoft Excel on Windows
How Does the Exploit Work?
At its core, Excel fails to properly validate or restrict certain embedded content in files. For example, an attacker could use a macro, malicious OLE object, or ActiveX control embedded in an Excel document to trigger code execution.
Attacker creates a dangerous Excel file with hidden code.
2. Victim opens the file. Excel either auto-runs the payload or tricks the user into clicking “Enable Content”.
3. Payload runs and executes malicious commands—like downloading malware or opening a reverse shell.
Simple Exploit Scenario
Below is a snippet that demonstrates how a macro could exploit this flaw, causing Windows Calculator (a benign example) to open. (In real attacks, it could drop ransomware or spyware.)
' Save as Module1 in a malicious Excel workbook (.xlsm)
Sub Auto_Open()
Shell "cmd.exe /c calc.exe", vbHide
End Sub
When this macro is triggered (possibly automatically on opening), it runs arbitrary code—in this case, launching Calculator for proof-of-concept.
Weaponization in the Wild
More organized attackers could wrap the payload with obfuscation, download payloads from the internet, or steal data. Since Excel files are often shared and trusted, many users ignore warnings or enable macros, making this avenue particularly dangerous.
An attacker could send an email
> Subject: "Urgent: Q2 Budget Review"
>
> Body:
> Please review attached spreadsheet ASAP—management is waiting.
>
> Attachment: Q2-Budget.xlsx (malicious macro inside)
Opening and enabling content could silently compromise the entire system.
Mitigations
Microsoft’s official guidance:
As of May 2024, Microsoft released patches for supported Excel versions. Update your copy of Office immediately.
More info:
- Microsoft Security Update Guide — CVE-2024-49026
References & More Information
- CVE Details page for CVE-2024-49026
- Microsoft Advisory – CVE-2024-49026
- Sophos Exploit Report on Recent Office Vulnerabilities
- How to Disable Macros by Default
Summing Up
CVE-2024-49026 is a wakeup call for anyone who uses Microsoft Excel, especially in business environments. Exploiting this vulnerability, attackers can run whatever code they want on your computer with just a simple email and attachment—no advanced hacking skills required. The best defense is to patch your software, avoid enabling macros, and train all users to think twice before opening attachments.
Stay alert. Update often. Share this knowledge to keep your network safe.
*This guide is exclusive content based on currently available public information. For technical details and the latest updates, always refer to Microsoft and official CVE sources.*
Timeline
Published on: 11/12/2024 18:15:42 UTC
Last modified on: 12/13/2024 00:50:15 UTC