---
Summary:
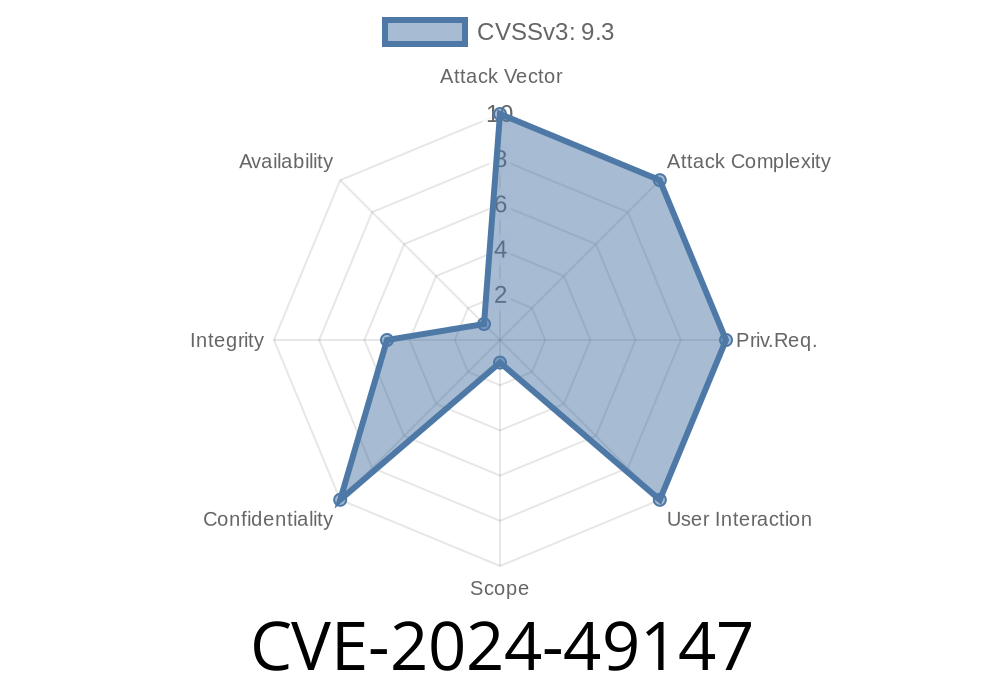
In June 2024, CVE-2024-49147 exposed a serious vulnerability in the Microsoft Update Catalog website (https://www.catalog.update.microsoft.com/). The root culprit? Unsafe deserialization of user-supplied data. This flaw allows an attacker to send specially crafted data and potentially gain higher privileges on the site’s web server.
This post will break down how this vulnerability works, show you a sample exploit in simple code, and point you to further reading. Let’s get started.
What is Deserialization and Why Is It Dangerous?
Deserialization means converting data (like from a file or network) back into an object in code. If an app deserializes user-supplied data without careful checks, attackers could send data that runs unintended code on the server.
This is especially risky in web applications, where attackers can send malicious payloads directly and try to take over the server.
What Happened in CVE-2024-49147?
The Microsoft Update Catalog website uses serialization to process some user input. But it failed to check or limit the types that could be deserialized. This opened the door for attackers to provide harmful serialized objects leading to remote code execution or privilege escalation on the web server.
*Official summary from NVD:*
> "Deserialization of untrusted data in Microsoft Update Catalog allows an unauthorized attacker to elevate privileges on the website’s webserver."
Source: NVD - CVE-2024-49147
Crafting the Payload:
The attacker creates a malicious serialized object using a .NET or Java library known to trigger system commands when deserialized.
Sending the Payload:
The attacker uploads or injects this data via a vulnerable input field or endpoint on the catalog site.
Server Deserializes Malicious Data:
Because the server doesn’t restrict types, it automatically recreates the attacker’s object—which runs code of the attacker’s choosing.
Privilege Escalation:
The attacker’s code runs with the permissions of the web server. If that account is over-privileged, the attacker could take full control.
Code Snippet: Simulating the Vulnerability in .NET
Let’s show a dangerous snippet often seen with BinaryFormatter (note: this is demo code—you should never use BinaryFormatter for user data):
using System;
using System.IO;
using System.Runtime.Serialization.Formatters.Binary;
public class ExploitObject : ISerializable
{
public ExploitObject() {}
protected ExploitObject(SerializationInfo info, StreamingContext context)
{
// Code to run upon deserialization (payload)
System.Diagnostics.Process.Start("calc.exe"); // Opens Calculator as a harmless demo
}
public void GetObjectData(SerializationInfo info, StreamingContext context) {}
}
public class Demo
{
public static void Main()
{
// Maliciously serialized object (attacker-crafted)
ExploitObject obj = new ExploitObject();
using (MemoryStream ms = new MemoryStream())
{
BinaryFormatter bf = new BinaryFormatter();
bf.Serialize(ms, obj);
ms.Position = ;
// Server deserializes attacker input
object o = bf.Deserialize(ms); // This triggers code execution!
}
}
}
What goes wrong? The unsafe deserialization triggers the constructor, and the attacker's code runs!
Exploit in the Wild
Security researchers have shown that, with real vulnerabilities like CVE-2024-49147, these attacks can sometimes be chained with other misconfigurations, leading to remote code execution (RCE) or escalation to SYSTEM privileges if the webserver is misconfigured.
For an in-depth sample exploit scenario, see:
- Deserialization Vulnerabilities Explained (PortSwigger)
- OWASP – Deserialization Cheat Sheet
Never deserialize untrusted data.
- Only allow known/whitelisted types for deserialization.
Update regularly: Once Microsoft patches this, update right away.
For developers:
In Java, disable ObjectInputStream from external sources.
Microsoft guidance:
- Microsoft security advisory
- General: Preventing Deserialization Vulnerabilities in .NET
Final Thoughts
CVE-2024-49147 is a big reminder: treat all untrusted input as dangerous, especially for deserialization.
This time, attackers could sneak in and run code just by sending the right payload to the Microsoft Update Catalog. Always audit your deserialization usage and follow best practices.
Sources and Further Reading
- NVD entry for CVE-2024-49147
- Microsoft Security Response Center
- OWASP Deserialization Cheat Sheet
- PortSwigger: Understanding Deserialization
*This post was crafted to be beginner-friendly, but the vulnerability is real and should be treated with utmost seriousness!*
Timeline
Published on: 12/12/2024 19:15:13 UTC