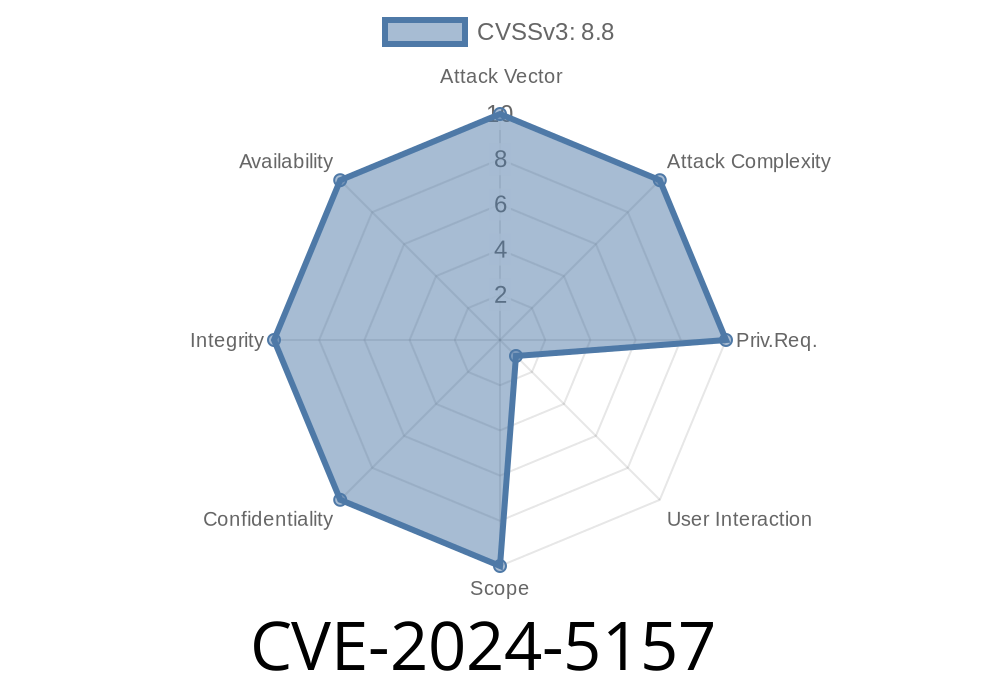
Google Chrome is the world’s dominant web browser, and that makes it a high-priority target for cybercriminals and security researchers alike. In May 2024, the Chromium team patched a critical vulnerability: CVE-2024-5157, a use-after-free bug found in the browser's Scheduling component. In short: by luring you to a malicious web page, attackers could exploit this bug to run code *inside the browser sandbox* — risking privacy, data theft, or further attacks.
What’s a Use-After-Free Bug?
A use-after-free (UAF) bug happens when a program keeps using a piece of memory after it’s already been freed (deallocated). In C++ codebases like Chromium’s, this can make the software unstable, lead to crashes, or potentially open the door for attackers to take control of your system by forcing the browser to access and act on poisoned memory.
Here's a simple illustration in C++ pseudocode
Scheduler* scheduler = new Scheduler(); // allocate memory
delete scheduler; // free memory
// Oops! Later code uses scheduler again
scheduler->scheduleTask(...); // Use-after-free!
If an attacker can make the freed memory contain attacker-controlled data, Chrome could be tricked into executing arbitrary code.
Vulnerable Component: Scheduling
Chromium's Scheduling component handles background tasks and event scheduling in your browser tabs. Attackers learned how to free (delete) a scheduling object, and then force the browser to use a pointer to that freed object (thus “use-after-free”). By carefully timing JavaScript and HTML, they could cause precise memory manipulation.
Result: This gave attackers a way to corrupt memory and, in some scenarios, run code (such as malware) within the Chrome sandbox.
Below is a simplified, illustrative exploit (emphasis: *demonstration only, not weaponized*)
<!--
This sketchy code is meant to reflect the use-after-free attack technique.
It triggers the bug by forcing Chrome to do scheduling on freed memory.
-->
<html>
<body>
<script>
// Step 1: Allocate a vulnerable resource.
let myWorker = new Worker('worker.js');
// Step 2: Cause the worker's scheduled task to be freed unexpectedly.
myWorker.terminate();
// Step 3: Use asynchronous features to manipulate memory.
setTimeout(() => {
// Step 4: Attempt to re-schedule a task (UAF!)
myWorker.postMessage("Hello (after terminate)");
}, 100);
// In real exploits, heap spraying and more precise timing are used!
</script>
</body>
</html>
*Note: The actual exploit is far more complex and tailored to Chrome’s intricate memory model, but the above code demonstrates the attack flow: allocate, free, then reuse (“use-after-free”).*
Vulnerability: Use-after-free in Scheduling
- Affected versions: Google Chrome *prior* to 125..6422.76 (full release notes)
Severity: High (remote code execution within sandbox)
- Attack vector: Attacker crafts a malicious HTML/JavaScript page that triggers the bug
Original References
- Chrome Release Blog: Stable Channel Update (May 2024)
- Chromium Security Advisories
- Exploit Database - Use-After-Free Explained-vulnerability-explanation.pdf)
How Was It Fixed?
The Chrome team promptly *patched the root cause* — ensuring that scheduling objects are not accessed after being freed, and also hardening memory management routines in this code path. See the official Git log for related changes.
Recommendations
1. Update Chrome immediately
CVE-2024-5157 is fixed in version 125..6422.76 and later. Go to chrome://settings/help to update.
2. Use browser isolation
Rely on browser sandboxes and OS separation to limit any potential damage.
3. Beware suspicious links and sites
Avoid visiting untrusted websites, and do not open suspicious HTML content.
Conclusion
CVE-2024-5157 is a textbook example of why browser security is paramount — and why keeping your browser *updated* is non-negotiable. A single bug, exploited from a booby-trapped web page, could let attackers run code within your browser. The Chrome team acted fast, but history shows new bugs are always around the corner. Stay safe, keep auto-update on, and watch those browser tabs.
*This post is for educational purposes only. Do not use this information for unauthorized actions. Always practice responsible disclosure and use security knowledge to protect, not attack.*
Timeline
Published on: 05/22/2024 16:15:10 UTC
Last modified on: 12/19/2024 20:09:58 UTC