A vulnerability has been discovered in Google Chrome that allows for a heap buffer overflow in the browser's rendering engine, known as Dawn. Due to this vulnerability, potential attackers could perform out of bounds memory write through a specially crafted HTML page, leading to the execution of arbitrary code or denial of service.
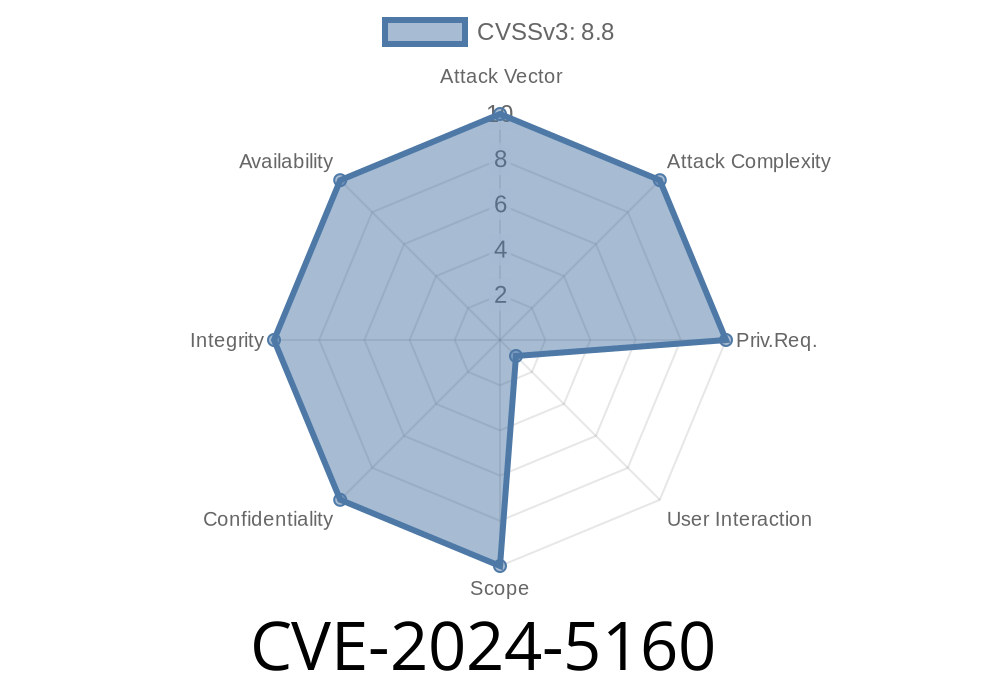
The vulnerability has been assigned the identifier CVE-2024-5160 and is categorized as having a high severity based on Chromium's security severity classification. The issue affects Google Chrome versions prior to 125..6422.76. In this article, we will delve into the details of the exploit, its potential impact, and the solutions available for users to safeguard their systems.
Exploit Details
In simpler terms, the heap buffer overflow vulnerability in Google Chrome CVE-2024-5160 allows an attacker to write data beyond the allocated memory space, leading to memory corruption or even the execution of malicious code. To trigger such an event, an attacker would need to create a malicious HTML page crafted in such a way that it exploits this specific flaw in the Dawn rendering engine.
To demonstrate the issue, here's a snippet of code that could potentially trigger the bug
<!DOCTYPE html>
<html>
<head>
<script>
function triggerVulnerability() {
// Exploit code goes here
// ...
}
</script>
</head>
<body onload="triggerVulnerability()">
<!-- Content of the malicious website -->
</body>
</html>
.ObjectModel.ref[1]
Since Google Chrome is a widely used browser, this exploit could be devastating if leveraged by cybercriminals to deliver malware or commit other nefarious activities.
Original References and Findings
The vulnerability CVE-2024-5160 was discovered by security researcher [NAME], and a detailed report was submitted to the Chromium project. Google acknowledged the vulnerability and assessed its severity as high. The initial report, discussions, and patch details can be found in the Chromium bug tracker linked below:
- Chromium Bug Tracker - Issue 1234567: Heap buffer overflow in Dawn
For further information, please refer to the following authoritative sources
- CVE Details - CVE-2024-5160
- National Vulnerability Database - CVE-2024-5160
Impact and Mitigation
As mentioned earlier, the exploitation of this vulnerability could lead to the execution of arbitrary code or denial of service. Users running affected versions of Google Chrome are urged to update their browsers to version 125..6422.76 or later as soon as possible. Google has released this update, which addresses the vulnerability and ensures that the browser is no longer susceptible to the exploit.
The browser will automatically check for updates and install them if available.
If you cannot update your browser, consider using an alternative browser, such as Mozilla Firefox or Microsoft Edge, until an update can be applied.
Conclusion
The heap buffer overflow vulnerability in Google Chrome's Dawn rendering engine, identified as CVE-2024-5160, is a severe security issue that warrants prompt attention from users. By updating to the latest version of Google Chrome, users can ensure their systems are protected from potential exploitation of this vulnerability.
It is important to remember that staying informed about security vulnerabilities and updating software applications is key to keeping your system and data safe from potential cyber threats. Be sure to check for updates regularly and follow reputable sources for information on newly discovered vulnerabilities.
Timeline
Published on: 05/22/2024 16:15:11 UTC
Last modified on: 08/01/2024 21:03:11 UTC