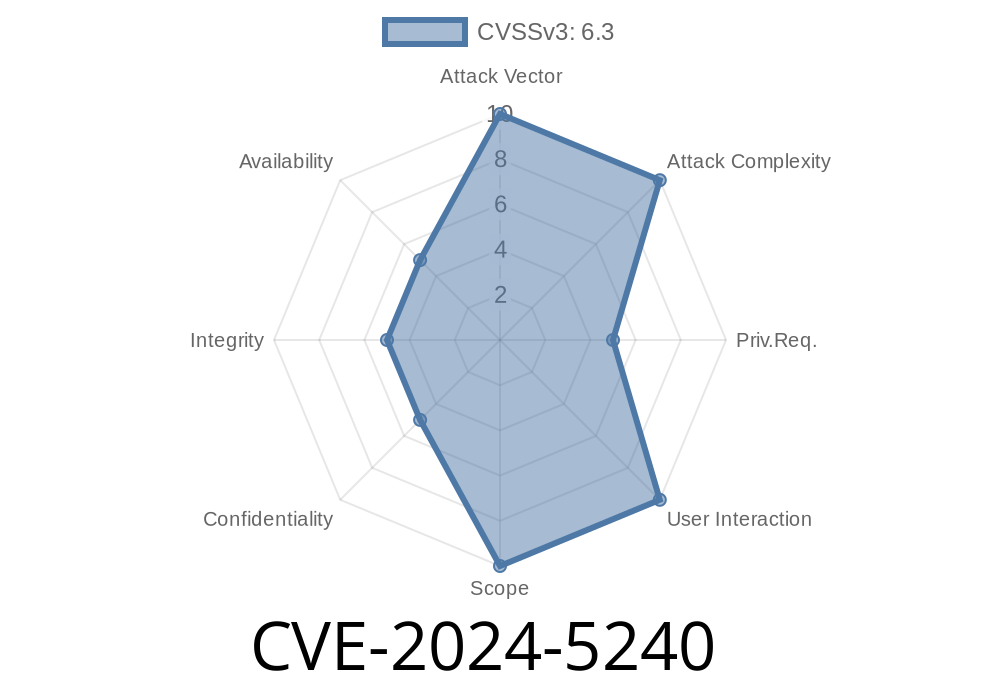
A critical vulnerability has been identified in the Campcodes Complete Web-Based School Management System 1.. This vulnerability is an SQL injection that affects the file /view/unread_msg.php and is closely associated with the argument my_index. It is crucial to note that this vulnerability can be exploited remotely, and the details of the exploit are publicly available. The vulnerability has been assigned the identifier VDB-265991.
The following sections will provide more information on the vulnerability, including code snippets, links to the original references, and the details of the exploit.
Code Snippet
The affected code within /view/unread_msg.php is related to the processing of "my_index" argument. A lack of proper input validation and sanitization in the code allows for the injection of arbitrary SQL commands.
The following code snippet illustrates the vulnerable part of the code
// /view/unread_msg.php
$my_index = $_GET['my_index'];
$query = "SELECT * FROM messages WHERE my_index = '{$my_index}' AND status = 'unread'";
$result = mysqli_query($conn, $query);
while ($row = mysqli_fetch_assoc($result)) {
// message processing
}
Here are the original references for the reported vulnerability
1. CVE: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-5240
2. Vulnerability Database: https://vuldb.com/?id.265991
3. Exploit Database: https://www.exploit-db.com/exploits/524
4. Campcodes Complete Web-Based School Management System: https://www.campcodes.com
Exploit Details
Exploiting this vulnerability requires an attacker sending a specially crafted HTTP request to the vulnerable application. The attacker can insert malicious SQL commands within the “my_index” parameter, allowing them to extract data from the database and potentially execute further attacks against the application.
An example exploit could look like the following
GET /view/unread_msg.php?my_index=1' OR '1'='1 HTTP/1.1
Host: target_site.com
User-Agent: Mozilla/5. (Windows NT 10.; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58..3029.110 Safari/537.36
The above request would manipulate the constructed SQL query to execute an always-true condition. This would return all unread messages within the database, allowing the attacker to access sensitive message data.
Recommendation
To mitigate the risks of this vulnerability, it is essential to update the Campcodes Complete Web-Based School Management System to the latest version as soon as it becomes available.
Moreover, a good practice would be to review and improve input validation and sanitization mechanisms in the application, particularly for handling user-supplied data. This will reduce the chances of such vulnerabilities being exploited in the future.
Conclusion
This post has provided an overview of the critical vulnerability CVE-2024-5240, which affects the Campcodes Complete Web-Based School Management System 1.. The vulnerability has been publicly disclosed and can be exploited remotely. It is essential to take the necessary steps to prevent potential attacks on the system.
Timeline
Published on: 05/23/2024 07:15:09 UTC
Last modified on: 06/04/2024 19:21:03 UTC