Google Chrome is one of the world’s most popular web browsers. Its fast JavaScript engine, V8, makes the web experience smooth and powerful. But sometimes, even the strongest engines have weak spots. On May 29, 2024, Google confirmed a high-severity issue (CVE-2024-5274) that made millions of Chrome users vulnerable — and it’s all about type confusion in the V8 engine.
In this article, I’ll walk you through the basics of the vulnerability, show you how the bug could be abused, and share how to stay safe online. No security degree required!
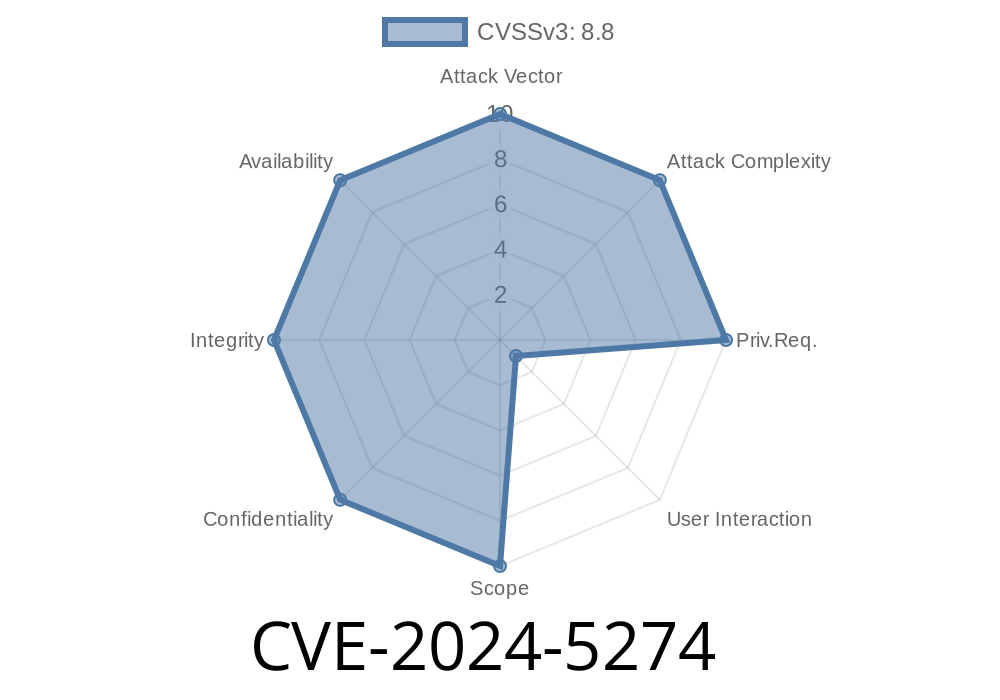
What is CVE-2024-5274?
CVE-2024-5274 is an identifier for a security flaw in Google Chrome’s JavaScript engine, V8, which allowed remote attackers to run code on your computer just by visiting a malicious web page. Chrome versions before 125..6422.112 are affected.
Short explanation:
The V8 engine got confused about what kind of data it was handling ("type confusion"), so attackers could make it view one type as another. This let them break memory boundaries and run custom code inside Chrome’s "sandbox"—not full system access, but still dangerous.
Original references
- Google Chrome Stable Channel Update - May 29, 2024
- Chromium Issue 335989746 (private bugtracker)
- MITRE CVE Database Entry
The Story: How Type Confusion Works
JavaScript is a loosely typed language. Internally, V8 keeps track of the "type" of its variables (number, object, string, etc.), so it can store and fetch data efficiently. If V8 gets confused about a type, it might read or write to memory in unsafe ways—a recipe for exploitation.
Imagine This
let arr = [1.1, 2.2, 3.3]; // Float array
let obj = [{}, {}, {}]; // Object array
// If a bug lets us treat arr as obj, BAM!
// We can trick V8 into giving us object pointers in a float array.
If attackers can trigger V8 to treat one type of array as another, they can read and write memory addresses instead of just values. This gives them a foothold to hijack code execution.
Proof-of-Concept: How an Exploit Could Work
Security researchers sometimes publish "proof of concept" code—simplified snippets to show how an attack could happen. Here's a *theoretical* example (not the actual attack, but close):
function triggerTypeConfusion() {
let arr = [1.1, 2.2, 3.3];
let fakeObj = { fake: 123 };
// Vulnerable code causes V8 to think arr is an object array.
arr[] = fakeObj;
// Now attacker can trick the engine into accessing memory as an object,
// potentially leaking pointers or crafting memory to inject code.
console.log(arr[]);
}
triggerTypeConfusion();
In the real attack, the malicious web page would have code similar to this, but more advanced. No user action needed—just visiting the page is enough.
What does this mean?
If an attacker can mess with V8’s memory using type confusion, they can insert and execute their own machine code (shellcode). The process is limited to Chrome’s restriction ("sandbox"), but it’s a powerful stepping stone.
Exploitation in the Real World
Google awarded a security researcher $20,000 for discovering this bug. Attackers could use exploit kits or malicious ads—without even needing to trick users with downloads or popups.
Stay Safe: How to Protect Yourself
- Update Chrome NOW: Go to chrome://settings/help — you should see Version 125..6422.112 or newer.
Enable auto-updates: Let Chrome update in the background.
- Be careful with third-party browsers based on Chromium (Brave, Edge, Opera, etc): They use the same engine.
Takeaways
- CVE-2024-5274 is a high-severity flaw that could let hackers run code on your computer just by loading a page.
Further Reading
- Google Chrome Release Notes
- Chrome Security Blog
- What is Type Confusion? (Imperva)
Timeline
Published on: 05/28/2024 15:15:10 UTC
Last modified on: 05/29/2024 01:00:04 UTC