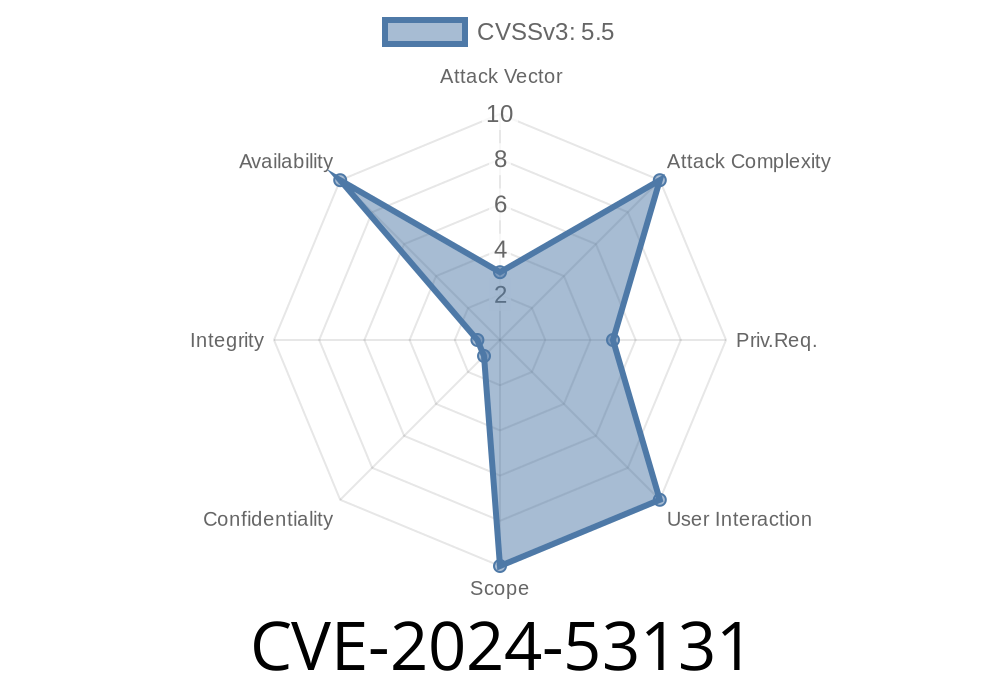
A newly discovered and resolved vulnerability, CVE-2024-53131, affected the Linux kernel’s nilfs2 filesystem code. This issue could cause a NULL pointer dereference in the block:block_touch_buffer tracepoint. If triggered, it may crash the system or cause memory errors when certain debugging or tracing tools are active, particularly when the Kernel Address Sanitizer (KASAN) is enabled.
In this long read, we break down the vulnerability, its root cause, exploitability, and how the Linux community resolved it. We'll also provide code snippets for a better understanding.
What is nilfs2?
NILFS2 (New Implementation of a Log-structured File System) is a log-structured filesystem for Linux, optimized for continuous snapshotting and high-performance storage scenarios.
What Went Wrong?
When using the tracepoint block:block_touch_buffer, the kernel calls the function touch_buffer() from within __nilfs_get_folio_block(). The problem originated when touch_buffer() tried to access the dev_t member via this chain:
bh->b_bdev->bd_dev
However, in certain code paths, the bh->b_bdev pointer was NULL because the associated block_device structure hadn't yet been assigned. Accessing a NULL pointer triggers a null pointer dereference, resulting in a kernel crash or protection fault, especially visible under KASAN.
This bug could be triggered during tracing or debugging but was not directly exploitable by unprivileged users unless sophisticated techniques were used for controlled kernel memory access.
The guilty code snippet looked like this
static int __nilfs_get_folio_block(...) {
...
touch_buffer(bh); // <-- problem spot!
...
}
The patch simply removed the unneeded and dangerous touch_buffer() call, since marking the folio/page as accessed is now done earlier or elsewhere:
Fixed code snippet
static int __nilfs_get_folio_block(...) {
...
// touch_buffer(bh); <-- line is gone!
...
}
Commit message excerpt
> "Here, touch_buffer() is used to mark the folio/page that owns the buffer head as accessed, but the common search helper ... was optimized ... eliminating the need to call touch_buffer() here in the first place. So this solves the issue by eliminating the touch_buffer() call itself."
Cause a *kernel panic* (crash).
- Potentially escalate privileges or leak information, depending on the kernel config and environment (though no such exploits are public at the time of writing).
Proof-of-concept (PoC) trigger (for researchers only)
# Enable the tracepoint
echo 1 > /sys/kernel/debug/tracing/events/block/block_touch_buffer/enable
# Perform nilfs2 operations
mkdir /mnt/test && mkfs.nilfs2 /dev/sdX && mount /dev/sdX /mnt/test
# Any normal file I/O can now trigger the bug
Note: This is mostly a *DoS* (denial of service) vector; it won’t let unprivileged users break the machine, unless deeper bugs exist.
Upstream Linux developers resolved the issue in the following patch series
- Patch 1: nilfs2: fix null-ptr-deref in block_touch_buffer tracepoint
If you use nilfs2 or allow tracing, update your kernel to 5.10.219, 6.6.33, 6.9.4, or later (as appropriate).
Links & Resources
- Main patch commit (kernel.org)
- NILFS2 homepage
- Linux Kernel Archives
- KASAN documentation
Summary
- CVE-2024-53131 affects Linux’s nilfs2 filesystem when using certain tracing/debugging tools.
Timeline
Published on: 12/04/2024 15:15:13 UTC
Last modified on: 12/14/2024 21:15:37 UTC