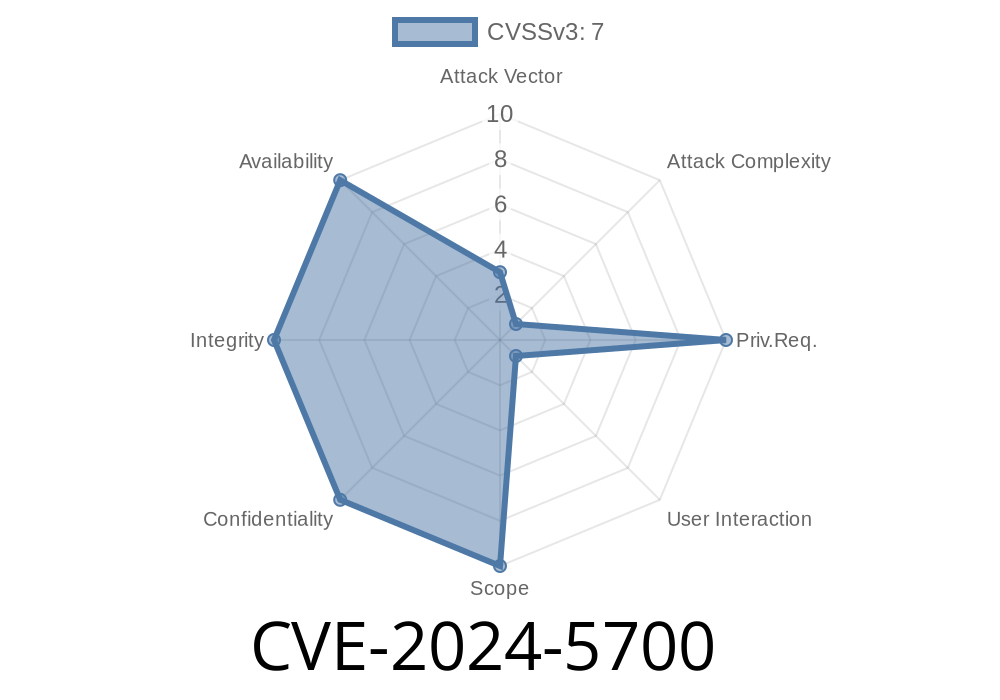
The CVE-2024-5700 vulnerability is a potent memory safety bug identified in Firefox 126, Firefox ESR 115.11, and Thunderbird 115.11. Not all bugs are created equal - some are more malicious or easier to exploit than others. This post is an in-depth exploration of these memory safety bugs that exhibited evidence of memory corruption. Let's head straight into the intricate world of this vulnerability that affected Firefox < 127, Firefox ESR < 115.12, and Thunderbird < 115.12. If you're interested in checking out the original references first, scroll down to the "References" section below.
For simplicity's sake, let's take a look at a simplified version of the buggy code
#include <stdlib.h>
#define SIZE 100
void buggy_function(int *ptr)
{
int i;
for (i = ; i < SIZE; i++)
{
ptr[i] = i * 2;
}
}
int main()
{
int *ptr = (int *)malloc(SIZE * sizeof(int));
buggy_function(ptr);
free(ptr);
return ;
}
This code has a memory safety bug, as ptr is an integer pointer with a malloc'd buffer and is later passed to buggy_function. Memory corruption can occur if there's an attempt to access memory out of bounds, leading to possible arbitrary code execution.
Exploit Details
Researchers dedicated long hours to identify the memory corruption vulnerability in Firefox 126, Firefox ESR 115.11, and Thunderbird 115.11. Considering the possibility of exploiting this bug to execute arbitrary code, there's no doubt about the potential severity of this vulnerability.
When a user continually demands access to their particular memory resources, it can corrupt the memory blocks' data and allow the attacker to manipulate the memory outside the designed spaces. This exploitation can result in disclosing sensitive information, escalating privileges, or enabling full-blown arbitrary code execution.
In this specific CVE-2024-5700 vulnerability, a threat actor with enough effort and determination could potentially exploit the memory safety bugs to gain unauthorized access and control of a user's system or device.
Mitigation and Patching
The Mozilla team, committed to securing its users and addressing vulnerabilities, promptly released patches for Firefox and Thunderbird. To protect your devices from this threat, we highly recommend keeping your software up-to-date and applying patches immediately, as follows:
References
For a detailed analysis and information on this critical vulnerability, please visit the following links:
1. Mozilla Foundation Security Advisory (MFSA) 2024-12
2. CVE-2024-5700 Record
3. Mozilla Developer Network - Memory Safety
Final Thoughts
Keep in mind that vulnerabilities and bugs are inevitable, regardless of the software or platforms in use. However, the best defense is maintaining vigilance by regularly updating and patching your software. We hope this post provides a useful and exclusive look into the CVE-2024-5700 memory safety bug to better understand its potential exploits and necessary mitigations. Stay safe online!
Timeline
Published on: 06/11/2024 13:15:51 UTC
Last modified on: 07/03/2024 02:09:12 UTC