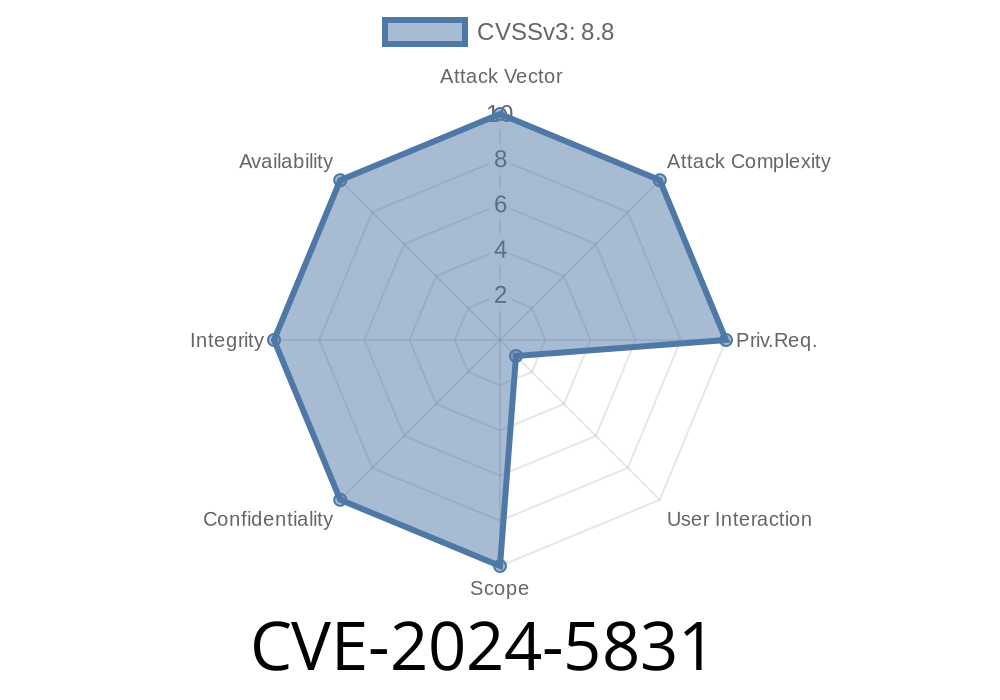
CVE-2024-5831 is a high severity "use-after-free" vulnerability lurking in Google's Chrome browser, specifically in the Dawn backend (which handles WebGPU). This bug is present in Chrome versions prior to 126..6478.54. If exploited, a remote attacker could trick Chrome into heap corruption, potentially allowing code execution or a browser crash—all via a crafted HTML page.
Chromium Security Severity: High
CVE Description: Use after free in Dawn in Google Chrome prior to 126..6478.54 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
2. How Does the Vulnerability Work?
"Use-after-free" is a memory bug where a program (here, Chrome) continues to use a part of memory after that memory has been released (freed). This can lead to crashes, unexpected behavior, or, worst of all, giving an attacker enough control to run their own code.
In this case, the vulnerability sits within Dawn, the backend component in Chromium that handles the WebGPU API. When a web page sends carefully structured GPU commands (for example, creating and deleting certain graphics objects in a twisted order), Chrome may end up trying to access memory that’s already been freed. An attacker can leverage this to corrupt the heap and possibly run the code of their choice.
Likely impacts other Chromium-based browsers (Edge, Brave, Opera) if not patched
If you're running an older version, upgrade immediately!
Gain arbitrary code execution or crash the browser
No user interaction beyond just opening the page is typically required.
Let’s see a simplified, educational example of what a malicious snippet might look like
// Not an actual exploit, for education only!
async function triggerUAF() {
// Get access to GPUDevice
const adapter = await navigator.gpu.requestAdapter();
const device = await adapter.requestDevice();
// Create a GPU resource
let buffer = device.createBuffer({
size: 1024,
usage: GPUBufferUsage.COPY_SRC,
mappedAtCreation: true
});
// "Free" the resource by destroying it
buffer.destroy();
// Rapidly trigger GC/freeing, then try to use the buffer again
// (simulate use-after-free; real exploit would be more complex)
// For demonstration, this is simplified:
try {
let result = buffer.getMappedRange(); // illegal use after free
console.log(result);
} catch (e) {
console.error("Error: use-after-free triggered", e);
}
}
triggerUAF();
In reality, an attacker would replace the "console.log" and error handling with heap spraying or code execution routines.
Advise users not to open untrusted web links.
Go to chrome://settings/help to check your version and update.
7. References
- Chromium Security Release Notes for 126..6478.54
- CVE-2024-5831 NVD Entry
- Chromium WebGPU (Dawn) source
- Official Google Chrome Blog
Conclusion
CVE-2024-5831 is a serious threat if left unpatched. The "use-after-free" bug in Chromium's Dawn backend opens the door for remote code execution attacks using a crafted HTML page. If you haven’t updated Chrome lately, now’s the right time!
Timeline
Published on: 06/11/2024 21:15:54 UTC
Last modified on: 07/03/2024 02:09:17 UTC