---
Introduction
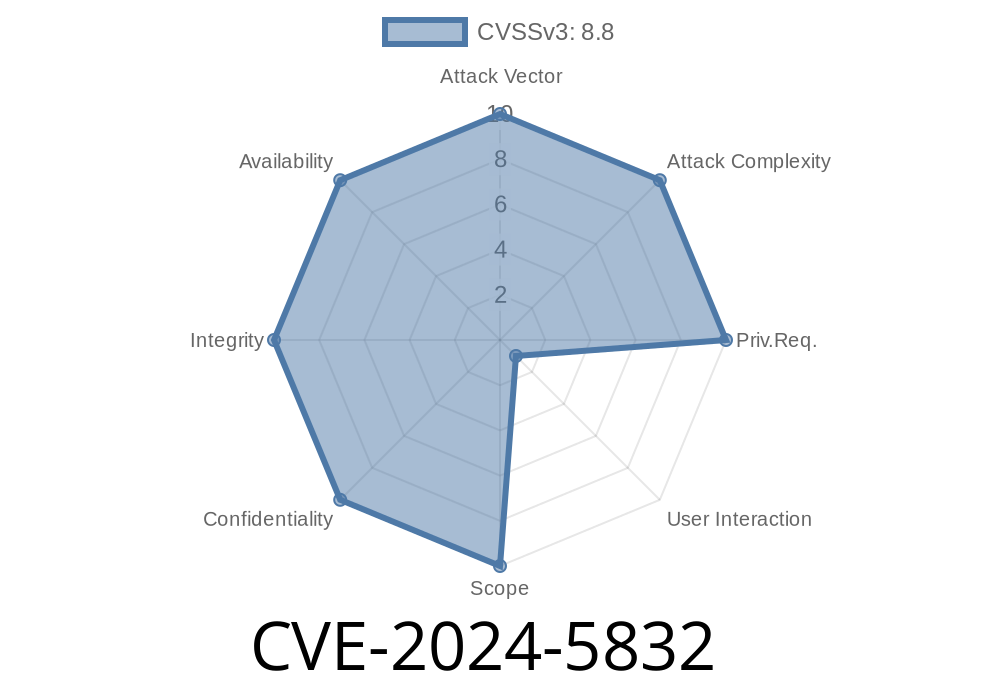
In June 2024, Google announced a high-severity security vulnerability tracked as CVE-2024-5832, impacting the Dawn graphics abstraction library within Google Chrome—prior to version 126..6478.54. This bug could allow a remote attacker to exploit heap corruption simply by luring users to a crafted web page. In this post, we break down what happened, how attackers could leverage it, and how you can stay safe.
What Is “Use-After-Free” and Why Does It Matter?
A use-after-free (UAF) occurs when a program continues to use memory after it’s been freed. This can lead to all sorts of unpredictable behavior, including crashes and, worst of all, giving hackers control over the system. In browser security, these are very dangerous because often attackers can trigger them just by getting you to visit a malicious website.
About CVE-2024-5832
CVE-2024-5832 specifically concerns a logical error in the Dawn component of Chromium, which is Chrome’s open-source project. Dawn is a modern graphics layer designed to keep Chrome’s rendering smooth and secure. However, an oversight in memory handling made it possible to use already-freed memory.
References
- Chromium Issue Tracker: 344624628 (Login needed to view details)
- Chrome Release Blog: Stable Channel Update for Desktop
- NVD Details: CVE-2024-5832
Technical Explanation (Simple Terms)
When Chrome processes a web page that uses advanced graphics (like <canvas> or WebGPU), it uses the Dawn library. Normally, when the browser is done using a piece of memory, it marks it "free" for later use. But, in this bug, Chrome could be tricked into using a piece of memory after it was already freed—possibly because of a race condition or poorly handled clean-up logic.
Here’s a simplified code scenario to illustrate
// Pseudocode, not exact Chromium source
class Command {
public:
virtual void Execute();
};
void ProcessGraphicCommands() {
Command* cmd = new Command();
// ... use cmd
delete cmd; // Memory is freed
// UAF Bug: We accidentally use 'cmd' again
cmd->Execute(); // Ooops! This is use-after-free
}
In real life, attackers would write a webpage with JavaScript that naturally (or forcibly) puts Chrome into this buggy state.
How Could Attackers Exploit This?
1. Craft a malicious HTML page that triggers the vulnerable code path in Dawn—often with WebGL, WebGPU, or canvas-based JavaScript code.
Trick a user into visiting the crafted page (malicious ad, phishing email, social engineering).
3. When Chrome processes the page, the UAF gets triggered, potentially giving the attacker control over the browser's memory.
Example Exploit Snippet
The Chrome team doesn’t disclose complete exploit code for security, but below is an *illustrative* JavaScript that pokes at graphics library bugs:
// WARNING: For education only. Never try exploits on machines you don’t own.
let context = canvas.getContext('webgl2');
function sprayHeap() {
let arr = [];
for (let i = ; i < 10000; i++) {
arr.push(new Float32Array(100));
}
return arr;
}
function triggerUAF() {
let arr = sprayHeap();
// Simulate deallocation bug by allocating + releasing a lot
for (let i = ; i < arr.length; ++i) {
arr[i] = null;
}
// Complex WebGL calls here can hit the vulnerable Dawn code...
}
triggerUAF();
*Note: This is not a weaponized exploit, only a demonstration of the technique exploiters might use.*
Download and install the latest version if you’re out of date.
2. Enable Automatic Updates: Make sure Chrome is set to update automatically, especially on devices that handle sensitive info.
3. Be Skeptical About Suspicious Links/Emails: Since web pages can trigger this, don’t click links from unknown or untrusted sources.
4. Enterprise Admins: If you manage Chrome in your company, push updates urgently and consider enabling site isolation and other mitigations.
Patch Released: Chrome 126..6478.54 on June 12th, 2024
- Public Disclosure: Via Chrome Release Blog
Conclusion
CVE-2024-5832 is a potent reminder that even well-designed software like Chrome can have serious flaws. With browsers under constant attack, keeping your software updated is the best defense. Tell your friends, family, and coworkers to patch Chrome immediately.
Stay safe and stay updated!
*Feel free to share this post with attribution. For deeper reading, refer to:*
- NVD Entry for CVE-2024-5832
- Chrome Release Notes
- CVE Record
Timeline
Published on: 06/11/2024 21:15:54 UTC
Last modified on: 07/03/2024 02:09:18 UTC