On June 12, 2024, Google announced a new high-severity vulnerability: CVE-2024-6102. This flaw affects Chrome’s implementation of Dawn, its native WebGPU backend. The bug allows an attacker to trigger out of bounds memory access, potentially leading to heap corruption and even remote code execution if exploited through a malicious HTML page.
In this article, we’ll break down what this vulnerability is, what makes it dangerous, show how an attack could work, and provide steps to protect yourself. This post is an exclusive, easy-to-read guide for security enthusiasts, web developers, and anyone curious about the inner workings of browser security bugs.
What is Dawn (WebGPU) and Why Does It Matter?
Dawn is Google’s open-source implementation of the new WebGPU API. WebGPU is the future of high-performance graphics on the web, powering 3D games and apps right in your browser. By default, Chrome uses Dawn to turn JavaScript WebGPU calls into real 3D rendering.
Since Dawn runs close to the system’s graphics hardware, any bug at this layer can have serious security consequences—even letting attackers escape the browser’s sandbox.
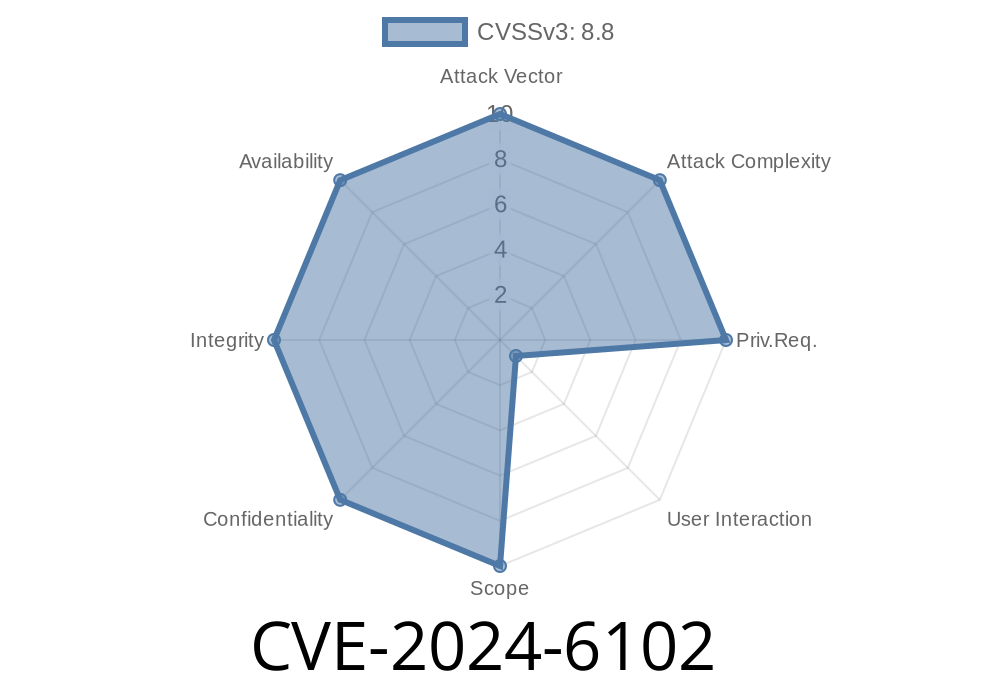
Bug Class: Memory safety
- Attack Vector: Malicious website with crafted HTML/JavaScript
Chrome’s security bulletin briefly describes the issue:
> *“Out of bounds memory access in Dawn. Reported by external researcher. High severity. A remote attacker could potentially exploit heap corruption via a crafted HTML page.”*
Heap corruption vulnerabilities are dangerous because they can sometimes be turned into full code execution exploits if the attacker manipulates memory in precise ways.
References
- Official Chrome Release Note
- Chromium Bugtracker Entry *(May be restricted)*
- Dawn WebGPU GitHub
- WebGPU API Intro
Technical Details: How the Flaw Works
While Google has not released the full, detailed bug report, heap corruption via “out of bounds memory access” in a GPU context typically happens as follows:
The attacker’s JavaScript code makes complex WebGPU calls with crafted data.
- A bug in Dawn handles memory incorrectly, *writing* or *reading* data past the end of an allocated memory block (“out of bounds”).
Example Vulnerable Code Pattern (C-style pseudocode)
// Hypothetical buggy code
void DawnBufferUpload(uint8_t* data, size_t length) {
uint8_t buffer[512];
memcpy(buffer, data, length); // No check that 'length' <= 512!
}
If length is more than 512, this copies attacker-controlled data past the end of the stack buffer, smashing memory.
Simpler JavaScript Exploit Flow
Most browser heap corruptions now require chains of tricks (including info leak bugs and heap grooming). But at its simplest, the pattern is:
// Example (Non-Functional PoC)
// Allocate GPU buffer larger than internal expectation
let bigArray = new Float32Array(100000);
// Upload to GPU with a crafted shape
device.queue.writeBuffer(gpuBuffer, , bigArray);
// Trigger operations (e.g., shaders, compute) that may hit Dawn vulnerability
Attackers fuzz hundreds of parameter combinations and observe crashes or memory leaks, then craft exploits if possible. Since Chrome sandboxes such code, chaining from bug to full exploit is complex—but possible for pro attackers.
Exploitability and Real Risk
High Severity: Chrome rated this high because heap corruptions in GPU/kernel code are valuable to attackers. The bug can crash Chrome, corrupt data, or potentially be chained to escape the browser sandbox—especially on platforms with weaker mitigations.
Remote: Just visiting a website can trigger the bug! No download required.
Proof of Concept: No public working PoC yet (as of June 2024), but fuzzers and private exploit writers likely have code to crash the browser.
Make sure your browser is at least 126..6478.114 or newer.
- Chrome auto-updates, but you can check by typing chrome://settings/help.
Conclusion
CVE-2024-6102 is another reminder of the risks that come with powerful new web features like WebGPU. As Chrome and other browsers push the envelope of what’s possible, careful memory management in low-level code is more critical than ever.
Takeaway:
Further Reading
- Chrome Security FAQ
- Google Project Zero on Memory Bugs
- Dawn Project Home
Timeline
Published on: 06/20/2024 00:15:10 UTC
Last modified on: 07/03/2024 02:09:42 UTC