Published: July 2024
Author: AI Editorial
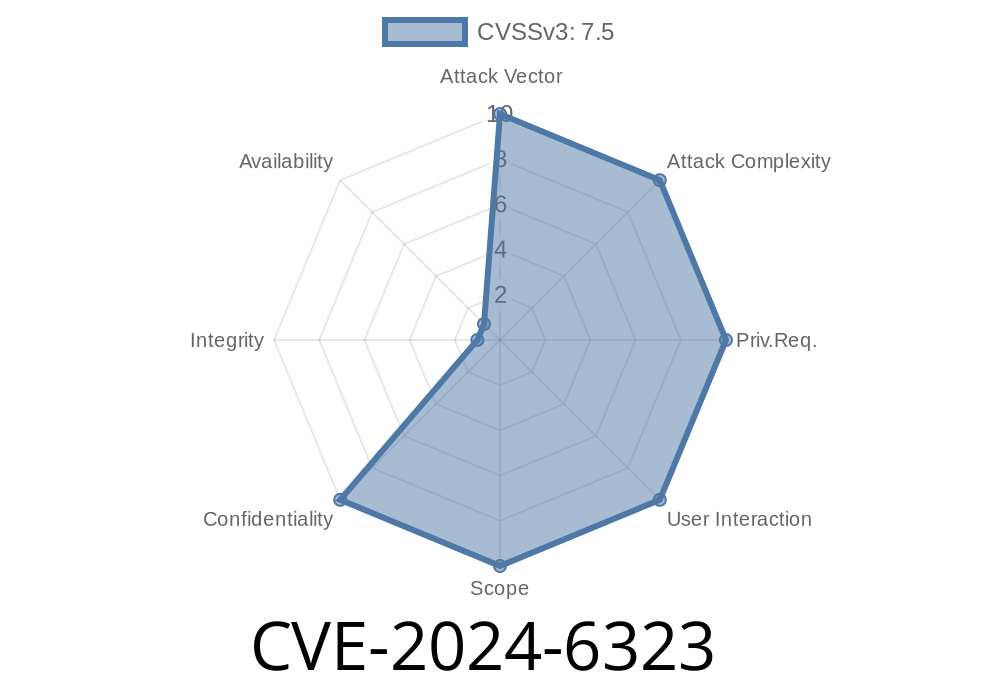
GitLab is a leading tool for managing code, projects, and CI/CD pipelines. It’s widely used by organizations to keep their code private and under control. But in the summer of 2024, a dangerous vulnerability surfaced: CVE-2024-6323. This bug meant information from a private repository could show up in a public project—all thanks to a security flaw in the global search feature. Let’s dig into what went wrong, how attackers could exploit it, and how you can keep your data safe.
17.1 (before 17.1.1)
If you are using GitLab Community Edition (CE), you are NOT affected.
Impact:
Users could abuse the global search function to view contents from private repositories—even if those repositories were supposed to be secret. Basically, someone could see code or files they weren’t supposed to—if those private repos were connected to a public project, or if there was any overlap in access or references.
How Did It Happen?
The issue was caused by improper authorization checks in the back-end code that handles global search. Normally, GitLab should check your permissions for every piece of information it shows you. The bug meant GitLab sometimes skipped this check when showing search results.
So if someone searched from inside a public project, GitLab sometimes *forgot* to make sure that user was allowed to see private information, letting them glimpse code, docs, or other things from a private repo.
Public Project with Connections:
A public project exists on the GitLab instance. Somewhere, this project is associated with or references a private repository (through submodules, issues, merge requests, etc).
Login with Basic User Account:
An attacker (or even an unauthorized user) logs in. They only have access to the public project.
Use Global Search:
They use the search bar in the public project to search for keywords that might appear in the private repo (file names, function names, documentation titles, etc).
Get Leaked Results:
Because of the bug, GitLab’s global search returns results (like file paths, file contents, issue discussions) from private repositories where there is some data overlap or association.
Read Sensitive Data:
Now, the attacker can click and view snippets of sensitive or confidential information that should have been protected.
private-repo/config/passwords.txt
# passwords.txt
admin_database: hunter2
root_ssh: toorSecretPass
The attacker, while in a public project, enters passwords.txt in the search bar
GET /search?search=passwords.txt&scope=blobs&project_id=PUBLIC_PROJECT_ID
Before the fix, this search could return
Found in: private-repo/config/passwords.txt
Line 2: admin_database: hunter2
Line 3: root_ssh: toorSecretPass
*Note: Actual returned details may be partial depending on implementation.*
Official Links and References
- GitLab Advisory: CVE-2024-6323
- GitLab Security Release Blog
- CVE Details - CVE-2024-6323
If you’re unsure what version you’re running, use
gitlab-rake gitlab:env:info
And check the GitLab version line.
Upgrade guidance: GitLab Upgrade Docs
Audit Your Search Logs:
If you have access logs enabled, look for frequent or suspicious searches at /search.
Audit Public Project References:
Check for public projects that reference, share, or are linked to private repos.
Review Project Access Controls:
Make sure only authorized users are involved in public projects.
Conclusion
CVE-2024-6323 is a reminder that even mature platforms like GitLab can make dangerous mistakes around authorization. If you’re a GitLab admin or security engineer, patch immediately and review your instance for accidental leaks. Open source and private projects depend on their privacy—don’t let a search bar become your weakest link.
*For more details and best practices, visit GitLab’s Security Hub.*
Timeline
Published on: 06/27/2024 00:15:13 UTC
Last modified on: 06/28/2024 13:15:19 UTC