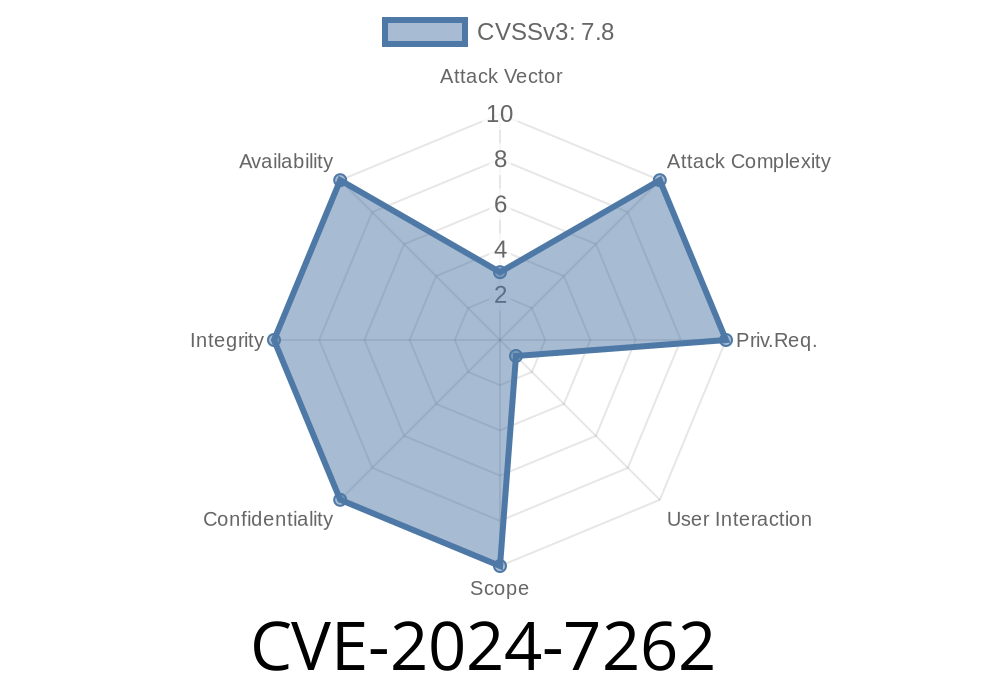
Kingsoft WPS Office is one of the most popular office suites in the world, especially in China. Recently, a significant security vulnerability (CVE-2024-7262) has been uncovered. Attackers can exploit this bug to run any Windows library they want by simply tricking someone into opening a malicious spreadsheet. This post covers the details of the bug, the scope of affected versions, references, and gives a peek at real-world exploitation – all explained in straightforward language.
What is CVE-2024-7262?
CVE-2024-7262 describes an improper path validation flaw in a component of WPS Office called promecefpluginhost.exe. Affected versions range from 12.2..13110 up to but not including 12.2..16412 on Windows.
Normally, when WPS Office needs to load an extension or plugin, it should only load files from trusted locations. Instead, this vulnerability allows a carefully crafted file – typically a spreadsheet – to make WPS Office load any DLL (Windows Dynamic-Link Library) that an attacker controls. Once that DLL is loaded, the attacker can run any code they want on your computer.
How Does the Exploit Work?
An attacker prepares a spreadsheet file (for example, an .xls or .xlsx) that embeds or references a malicious DLL. Due to the lack of proper checks in promecefpluginhost.exe, when the victim opens the file, WPS Office loads the attacker's DLL — no warning, no prompt needed.
`cpp
// malicious_dll.cpp
return TRUE;
}
`
cl /LD malicious_dll.cpp
Craft The Weaponized Spreadsheet
The spreadsheet exploits the path validation flaw by referencing the DLL using a relative path, or sometimes embedding it in a zipped format so that when extracted (even temporarily), promecefpluginhost.exe picks up the malicious DLL automatically.
Lure the Victim
The attacker sends the spreadsheet via email, shared cloud drive, or messaging app. Because the attack is a one-click exploit, the victim only needs to open the spreadsheet file using a vulnerable version of WPS Office.
Attack Demonstration
Suppose the malicious DLL is named ucrtbase.dll (to match a commonly-loaded library). The attacker zips both the DLL and the weaponized spreadsheet together, or places them in the same folder.
Here’s a sample folder structure
/attack-folder
|- report.xlsx
|- ucrtbase.dll <-- Malicious DLL
When the user opens report.xlsx, promecefpluginhost.exe will search for ucrtbase.dll (because the spreadsheet requests it or has a macro reference), finds it in the current directory, and loads it without verifying its legitimacy.
Real-World Impact
This attack was found being used “in the wild,” meaning bad actors are already using it to compromise real users. Because the exploit works with a simple spreadsheet, many users won’t be suspicious — especially if the document appears important or urgent.
Victims don’t have to enable macros or lower any security settings; just opening the file with an affected version is enough.
Affected Versions
Vulnerable:
WPS Office 12.2..13110 up to but not including 12.2..16412 (on Windows)
Not Vulnerable:
WPS Office 12.2..16412 and later
- Official update announcement
Official Patch
Kingsoft released a fix in version 12.2..16412.
- Download latest version: https://www.wps.com/download/
References
- NVD: CVE-2024-7262
- WPS Office Changelog
- Kingsoft Security Bulletin
Conclusion
CVE-2024-7262 is a critical vulnerability affecting many Windows users of WPS Office who haven’t yet updated. The exploit is simple, dangerous, and already out in the wild, weaponized in the form of everyday-looking spreadsheets. Always double-check your WPS Office version, keep software up to date, and be careful with attachments — especially before opening that next spreadsheet!
If you enjoyed this exclusive breakdown, let your IT team or coworkers know to update WPS Office ASAP!
Timeline
Published on: 08/15/2024 15:15:22 UTC
Last modified on: 09/05/2024 13:30:33 UTC