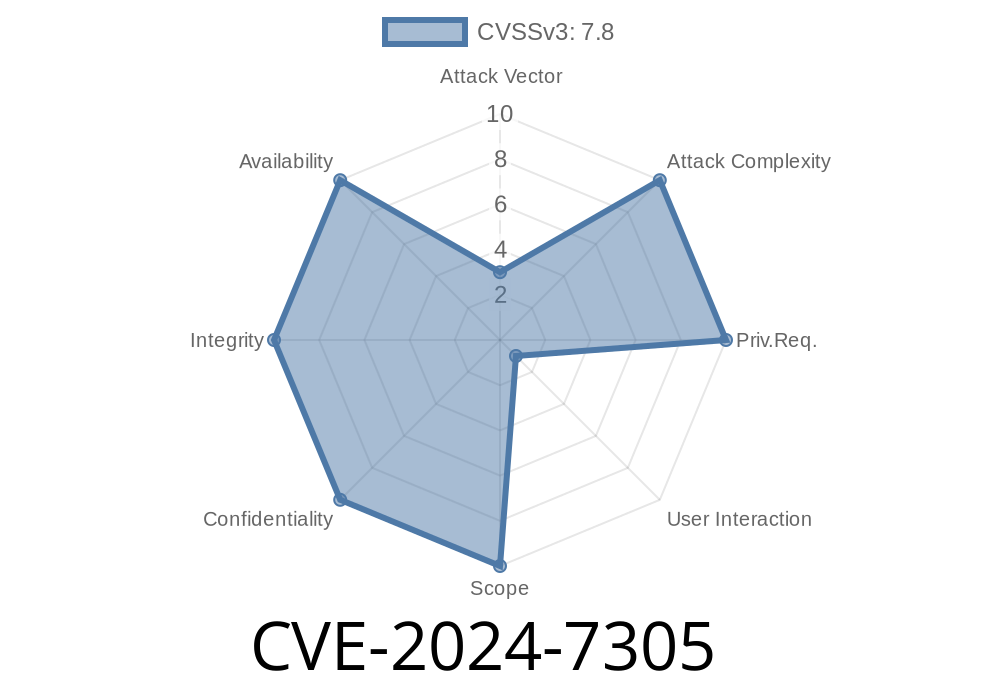
In early 2024, a serious vulnerability—CVE-2024-7305—was discovered in Autodesk AutoCAD. The flaw centers on the way the AdDwfPdk.dll library inside AutoCAD handles specially crafted DWF files. This out-of-bounds write bug is a classic “memory corruption” problem, allowing attackers a way to force a crash, steal data, or even run their own code on your PC. In this article, we break down how the exploit works, offer in-depth technical details, and show you what you need to know if you use AutoCAD.
What is CVE-2024-7305?
This vulnerability exists because of how AdDwfPdk.dll—a plugin library used by AutoCAD to process DWF files (Design Web Format)—doesn't properly check user-supplied data when parsing certain file structures.
An attacker can create a corrupted DWF file that, when opened in AutoCAD, causes the library to write outside the valid memory buffer. This classic security mistake opens the door for:
Where’s the Problem?
The issue is in the DWF parsing code inside AdDwfPdk.dll. When an input DWF file includes a particular malformed section, the DLL does not validate array indexes or memory buffer sizes before writing data. When a large or negative index is provided, it writes past the end of a buffer—a so-called "out-of-bounds write".
Here’s a simplified code snippet to picture the risk
// Example pseudocode showing the vulnerable logic
void ProcessDwfSection(char* buffer, int sectionLen) {
char sectionData[1024];
// Fails to check that sectionLen <= 1024
memcpy(sectionData, buffer, sectionLen); // Vulnerable to overflow!
// ... process sectionData ...
}
If an attacker puts a massive value for sectionLen in the DWF file, this copy operation will overwrite adjacent memory—possibly including other variables, return addresses, or even function pointers.
How might an attacker use this?
1. Construct a Malicious DWF: The attacker creates a DWF file with crafted binary data to exploit the parsing logic in AdDwfPdk.dll.
Deliver the File: They send this file to the victim (phishing email, file share, etc).
3. Victim Opens in AutoCAD: The user opens the booby-trapped DWF. AutoCAD loads it, triggering the vulnerable code.
4. Memory Corruption Occurs: If the attacker is clever, they arrange the overflow to let them divert execution to their payload.
5. Code Execution or Crash: The process may crash (denial of service), but if the payload is setup right and protections are weak, the attacker gets code execution in the context of the user's account.
Exploit Example
While actual proof-of-concept code is not public for obvious reasons, here’s a simplified Python snippet for how an attacker could create an overlong DWF "section" triggering the bug:
# WARNING: DO NOT use this for malicious purposes.
# Simple PoC for broken section size in DWF
with open('evil.dwf', 'wb') as f:
# Write some header (DWF files usually start with 'DWF V' or similar)
f.write(b'DWF V06.00\n')
# Add a huge section intended to overflow the parser
f.write(b'MalformedSection' + b'A' * x200) # 8192 bytes
When AutoCAD opens this DWF, it will process the massive "MalformedSection", potentially causing the out-of-bounds write and exploiting the bug.
Anyone handling DWF files from untrusted sources
Attack vector: Local (needs user interaction), but easily weaponized for spearphishing.
Mitigation & Fix
Autodesk has issued a patch for this vulnerability. The best solution is to update AutoCAD and related plugins immediately.
Official Security Advisory:
https://www.autodesk.com/trust/security-advisories/adsk-sa-2024-7305
CVE Record:
https://nvd.nist.gov/vuln/detail/CVE-2024-7305
Why Is This Important?
CAD files are widely exchanged in business, industry, and design. As AutoCAD is a major standard, even a simple file opened by a trusted engineer can become the key for attackers to slip into your company network or steal your project IP.
Summary
CVE-2024-7305 is a critical threat for anyone using Autodesk AutoCAD. All it takes is one crafted DWF to trigger this out-of-bounds write and potentially let attackers take over your system. Update immediately, and treat all incoming DWF files with suspicion until you’re sure you’re safe.
For more technical details:
- Autodesk Trust Center Security Advisory
- National Vulnerability Database Entry
Timeline
Published on: 08/20/2024 00:15:04 UTC
Last modified on: 08/20/2024 15:44:20 UTC