Published: June 2024
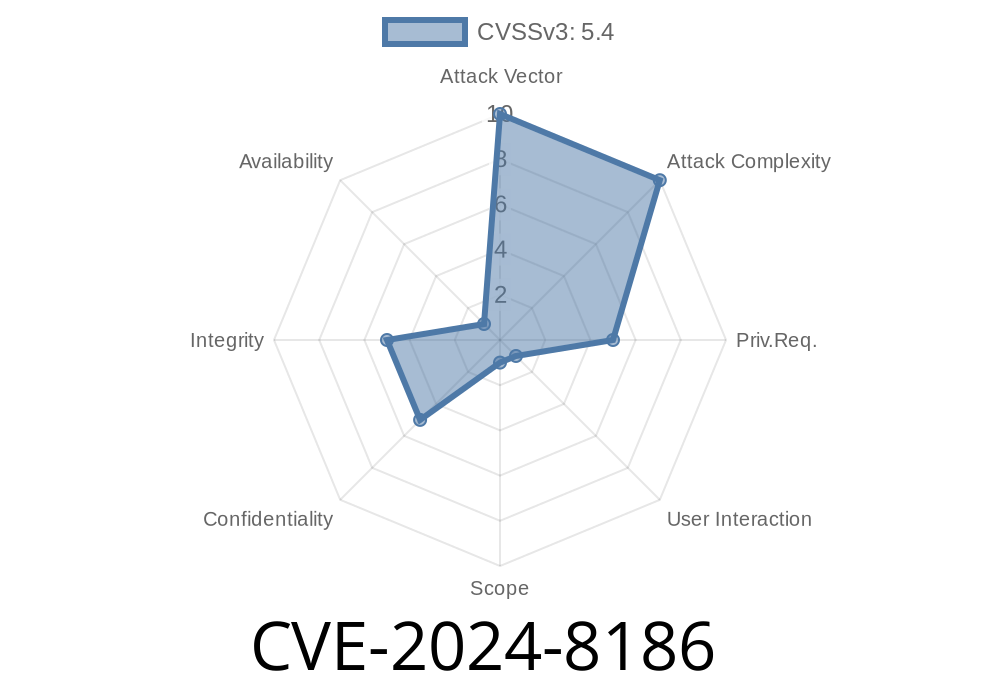
Severity: High
Component: GitLab Community Edition (CE) & Enterprise Edition (EE)
Vulnerable Versions:
🚨 What is CVE-2024-8186?
CVE-2024-8186 is a security flaw recently found in GitLab which allows an attacker to inject HTML code into the “child item search” functionality. In certain conditions, this HTML can be interpreted as JavaScript, resulting in a classic Cross-Site Scripting (XSS) attack.
This threatens the confidentiality and integrity of any GitLab instance that has not been patched, because an attacker could steal session cookies, modify interface content, or perform actions on behalf of victims.
🦠 How Does the Exploit Work? (Simple Explanation)
It comes down to input fields on the “Issue Boards” or Epics feature where you search for or add child items (like sub-issues or child epics). GitLab did not properly sanitize the search terms in the child item search. That means if an attacker put in specially crafted HTML or JavaScript into this field, it would get rendered unescaped in the page—allowing a malicious script to run.
The victim clicks a link or triggers a search with the attack string.
- The result returned by GitLab renders the attacker’s code, running in the browser of anyone viewing it.
🧑💻 Exploit Example (Code Snippet)
> Warning: Never test on production systems, especially with real users!
Suppose your GitLab server is at https://gitlab.internal/.
An attacker creates or edits an issue in a public project and in the “Add child item” search bar, submits:
"><img src=x onerror=alert('XSS')>
The search term is saved or processed.
- When another user views the child item search field (or loads search results), the unsanitized input is rendered directly by the browser.
Proof-of-Concept (PoC) Link
The attack can also be triggered via a GET parameter to the search endpoint (the endpoint name may change with GitLab versions—this is for illustration):
https://gitlab.internal/groups/mygroup/-/epics?search=%22%3E%3Cimg%20src%3Dx%20onerror%3Dalert%280%29%3E
If the GitLab version is vulnerable, an alert box will pop up for any user loading this page (meaning the attacker’s script executed).
See official patch notes and download
- GitLab Critical Security Release - CVE-2024-8186
> If you cannot update immediately, restrict access to the GitLab web interface or use a web application firewall (WAF) to block suspicious input.
No time to upgrade?
Disable public group/project access and restrict who can create or search issues until you patch.
[x] Audit logs: Look for unusual “child item” searches or entries.
- [x] Check for new users/projects created by unknown sources.
🕵️♂️ References and Further Reading
- GitLab Release Blog / Security Bulletin
- NIST CVE entry for CVE-2024-8186
- GitLab Security Advisories
🚀 Conclusion
CVE-2024-8186 is easy to exploit and affects a wide swath of production GitLab CE/EE installations. If you’re a GitLab admin or DevOps engineer, upgrade today. Even private servers are at risk if a malicious insider or guest can inject search terms.
Timeline
Published on: 03/03/2025 10:15:09 UTC
Last modified on: 03/06/2025 14:58:21 UTC