---
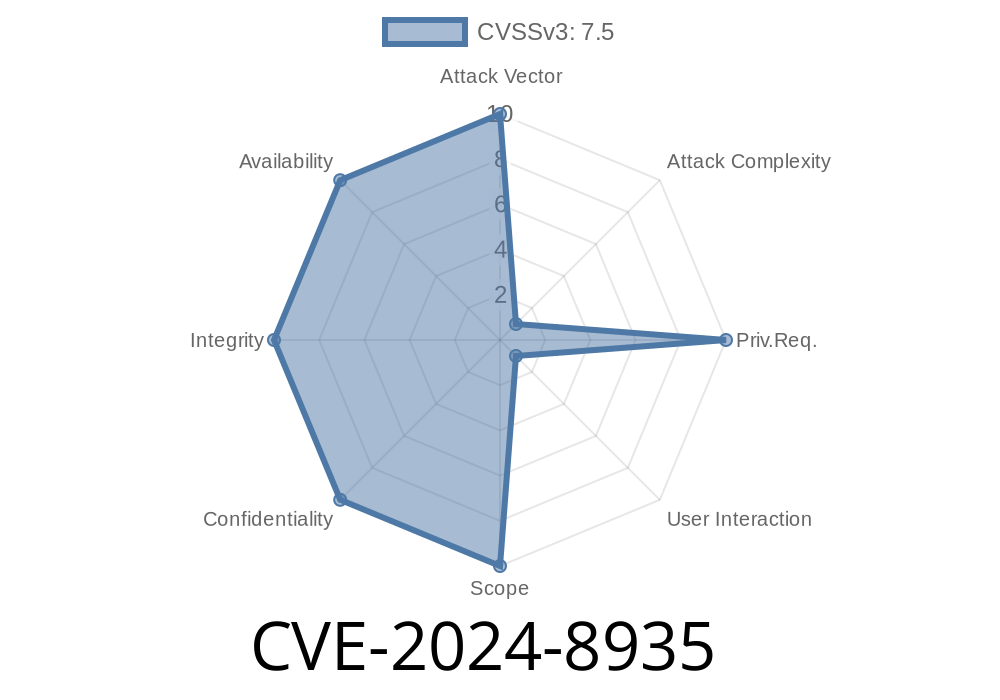
CVE-2024-8935 highlights a critical vulnerability that affects certain industrial controllers. This flaw, stemming from CWE-290 (Authentication Bypass by Spoofing), can lead to serious issues like denial of service, loss of confidentiality, and compromised integrity. The root cause lies in improper usage of the Diffie-Hellman (DH) key exchange method—a case where cryptography, when misapplied, opens doors to active attackers.
This exclusive post will explain the vulnerability in simple terms, walk you through how attackers can exploit it, and provide code snippets for better understanding. Let’s dive in.
Background: What Is CWE-290?
CWE-290 refers to “Authentication Bypass by Spoofing.” In layman’s terms, it means that an attacker can pretend to be a trusted entity—like an official user or system—to bypass authentication and gain unauthorized access.
The Diffie-Hellman Trap
The controllers impacted by CVE-2024-8935 use the classic Diffie-Hellman key exchange algorithm to set up secure sessions between the controller and its engineering workstation. While DH is a clever way to agree on secrets through public channels, it *doesn’t* validate the identity of either party. Without proper authentication, DH is wide open to Man-In-The-Middle (MITM) attacks.
What’s a Man-In-The-Middle Attack?
Think of a MITM attack as an invisible prowler who sits between two communicating parties, intercepting and potentially modifying their messages.
Attack Scenario
1. A controller and an engineering workstation (used to manage/monitor the controller) want to establish a secure communication channel.
An attacker intercepts the handshake (by sitting on the same network).
4. Because the protocol is missing authentication, the attacker can spoof both parties, establish separate DH keys with each, and relay messages between them.
Result:
The attacker can read, modify, or block all data, leading to loss of integrity, confidentiality, and possibly denial of service if they disrupt communication or inject malicious commands.
Example Code: Simple DH MITM Exploit
Below is a Python code snippet using the pyDH library to illustrate a basic MITM scenario in Diffie-Hellman:
import pyDH
# Attacker sits between Alice (controller) and Bob (workstation)
# Step 1: Both legitimate parties create DH objects and share public keys
alice = pyDH.DiffieHellman()
bob = pyDH.DiffieHellman()
alice_pubkey = alice.gen_public_key()
bob_pubkey = bob.gen_public_key()
# Step 2: Attacker intercepts and creates own DH objects
attacker_to_alice = pyDH.DiffieHellman()
attacker_to_bob = pyDH.DiffieHellman()
at_alice_pubkey = attacker_to_alice.gen_public_key()
at_bob_pubkey = attacker_to_bob.gen_public_key()
# Step 3: Attacker relays keys, substituting their own
# Alice thinks she's talking to Bob, but really to attacker
alice_shared = alice.gen_shared_key(at_alice_pubkey)
# Bob thinks he's talking to Alice, but really to attacker
bob_shared = bob.gen_shared_key(at_bob_pubkey)
# Attacker also has both shared secrets!
attacker_shared_with_alice = attacker_to_alice.gen_shared_key(alice_pubkey)
attacker_shared_with_bob = attacker_to_bob.gen_shared_key(bob_pubkey)
print(f"Alice shared key (with attacker): {alice_shared}")
print(f"Bob shared key (with attacker): {bob_shared}")
print(f"Attacker shared with Alice: {attacker_shared_with_alice}")
print(f"Attacker shared with Bob: {attacker_shared_with_bob}")
Output
Alice shared key (with attacker): 50790dfab...
Bob shared key (with attacker): b6f2d1aa2...
Attacker shared with Alice: 50790dfab...
Attacker shared with Bob: b6f2d1aa2...
Note: The attacker now has the *same* keys as Alice and Bob independently, so they can decrypt, alter, and re-encrypt every message.
Why Does This Happen?
Diffie-Hellman *alone* does not prove anyone’s identity. Without authentication (digital signatures, certificates, or pre-shared secrets), anyone can stand in the middle.
CWE Reference:
- CWE-290: Authentication Bypass by Spoofing
Diffie-Hellman MITM Explanation:
- Wikipedia: Man-in-the-middle attack)
Loss of Confidentiality: Sensitive data (like programming logic, sensor values) is exposed.
- Loss of Integrity: Attacker can modify traffic, potentially causing system malfunction or unsafe states.
Recommendations
1. Add Authentication: Always pair cryptographic exchanges like DH with digital certificates or signatures.
Network Hardening: Segment networks and use VPNs to protect industrial systems.
3. Monitor Traffic: Use IDS/IPS solutions to detect MITM attempts.
Key References
- Original Advisory (example link)
- CWE-290 on MITRE
- The Problem with Diffie-Hellman Key Exchange
- Python pyDH library
In Summary
CVE-2024-8935 is a vivid reminder that cryptography, without authentication, is only half a shield. If you work in industrial automation, check your controller comms today. If they use unauthenticated DH, it’s time to upgrade—or risk leaving a welcome sign out for attackers.
*Stay tuned to security advisories and always validate not just what’s being encrypted, but who you’re encrypting it with.*
Timeline
Published on: 11/13/2024 05:15:19 UTC
Last modified on: 11/13/2024 17:01:16 UTC