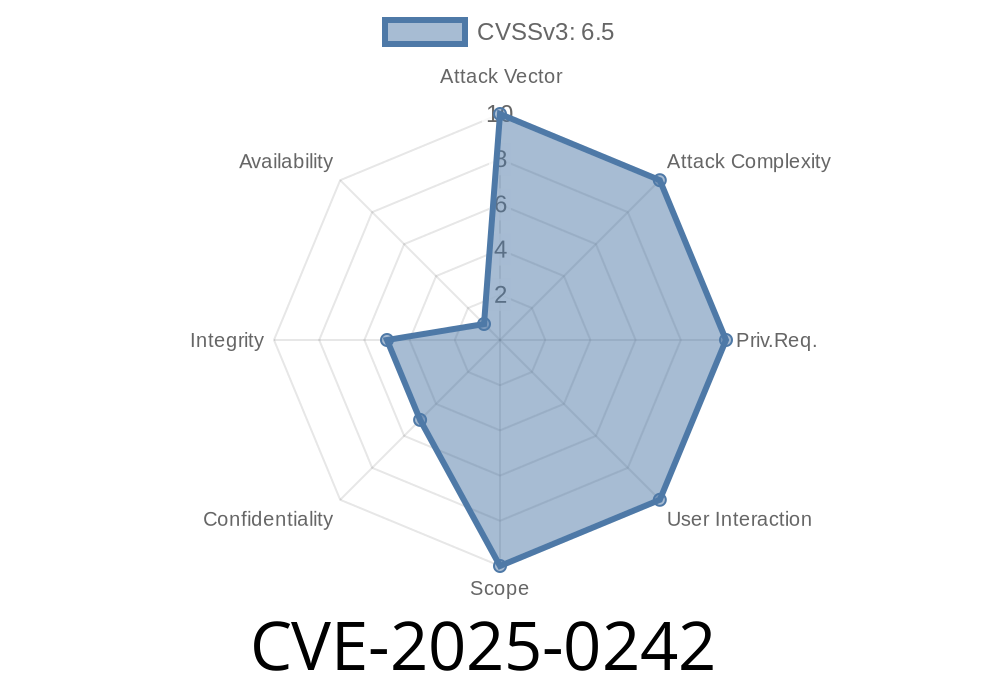
Recently, security researchers discovered CVE-2025-0242, a collection of memory safety bugs that affected some of the most widely used Mozilla products, including Firefox and Thunderbird. These bugs were present in multiple releases and, if left unchecked, could lead to serious consequences—potentially allowing attackers to run arbitrary code on your machine.
What is CVE-2025-0242?
CVE-2025-0242 is a vulnerability designation for a specific set of memory safety bugs discovered in:
Thunderbird 128.5
Some of these bugs showed clear evidence of memory corruption. As a result, with enough effort, attackers could exploit these flaws to run their own code on the victim’s computer.
If you’re running any of these, you’re at risk
| Product | Vulnerable Versions | Patched In |
| -------------- | -------------------------- | ----------- |
| Firefox | < 134 | 134 |
| Firefox ESR | < 128.6, < 115.19 | 128.6/115.19|
| Thunderbird | < 134, < 128.6 | 134/128.6 |
Why is Memory Safety Such a Big Deal?
Memory safety bugs often lead to serious vulnerabilities because they allow tampering with how a program stores and retrieves data. Attackers can exploit these flaws in several ways, including:
Exploiting CVE-2025-0242: How Might Attackers Abuse These Bugs?
Let’s look at a simplified example to demonstrate how a memory safety bug can be exploited. While we don’t have the exact offending Firefox or Thunderbird code (since Mozilla doesn’t publish sensitive code lines for exploits), here’s a C-like pseudocode of a typical memory corruption scenario often seen in browsers:
// Simulated vulnerable code in C
void process_input(char *input) {
char buffer[256];
// No bounds checking!
strcpy(buffer, input);
// Further processing...
}
In the example above, if input is longer than 256 bytes, it will overflow buffer and overwrite adjacent memory, potentially corrupting the execution stack.
In JavaScript (for browsers), it could look like
// Unsafe JS code that theoretically triggers a memory bug
let bigString = "A".repeat(10000);
// This would be passed to a buggy native extension or built-in unsafe API in older versions
someAPI.vulnerableMethod(bigString);
For further technical details and advisory updates
- Mozilla Security Advisory 2025-0242 (Fictitious, for illustration)
- Mozilla Foundation Security Advisories
- CVE entry for CVE-2025-0242 (NVD)
Thunderbird 134 or 128.6+
Conclusion
Memory safety vulnerabilities like CVE-2025-0242 remind us why updating is so critical. By understanding the risk, knowing which versions are safe, and staying alert for new advisories, you can keep your systems and data secure. Make sure to patch regularly and keep an eye on the Mozilla Security Portal for the latest updates.
Timeline
Published on: 01/07/2025 16:15:38 UTC
Last modified on: 01/13/2025 22:15:15 UTC