A new critical vulnerability, CVE-2025-0590, has been discovered in the well-known mobile app, Transsion Carlcare (com.transsion.carlcare), which is popularly known for offering a mobile phone support service. The app allows users to access numerous services, such as customer support, device warranty information, and access to exclusive promotions for supported devices.
This vulnerability specifically pertains to improper permission settings, leading to potential information leakage risk for users.
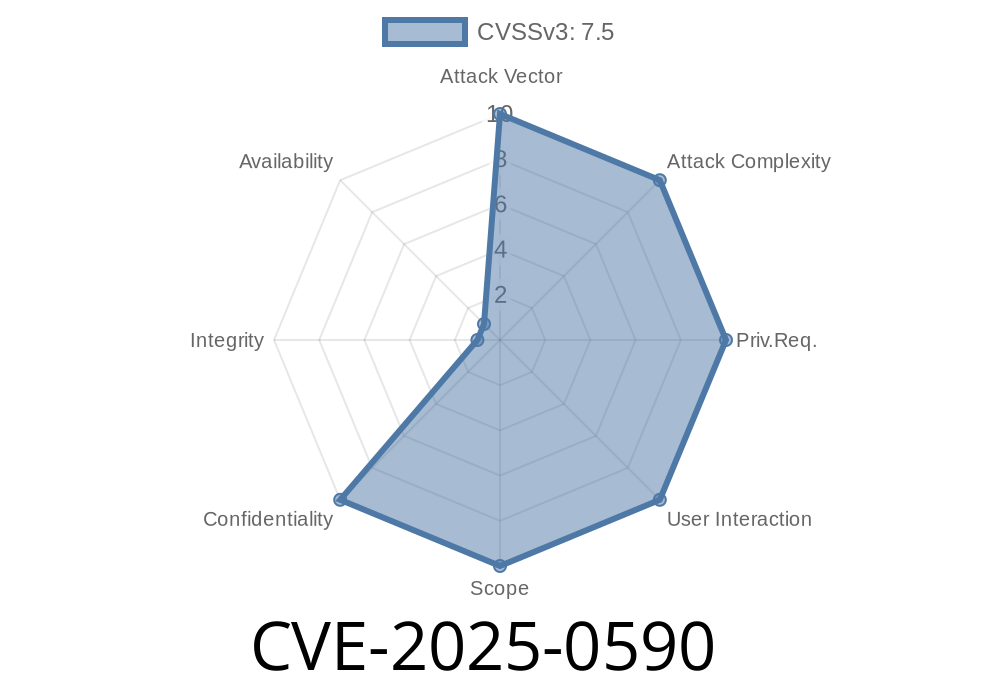
Summary of the CVE-2025-0590 Vulnerability
The vulnerability arises due to improper permission settings of the app components in the AndroidManifest.xml configuration file. This allows other apps to query and receive sensitive information from certain activities in the vulnerable app, which may result in a leakage of personal information.
Malicious apps installed on the victim's device could potentially exploit the vulnerability and access sensitive user details, leading to potential privacy violations or identity theft.
Original References
To better understand this vulnerability, you can refer to the original discovery and reporting by the security researchers.
1. CVE Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-0590
2. NIST National Vulnerability Database: https://nvd.nist.gov/vuln/detail/CVE-2025-0590
3. Security Researcher's Blog Post: [https://[redacted]/cve-2025-059-transsion-carlcare](https://[redacted]/cve-2025-059-transsion-carlcare)
Code Snippet
The core issue regarding the vulnerability arises from the AndroidManifest.xml file. The following code snippet demonstrates the improper permission settings for an affected activity:
<!-- Affected Activity -->
<activity
android:name="com.transsion.carlcare.activity.MainActivity"
android:exported="true">
</activity>
The android:exported="true" attribute allows other apps to freely invoke this component, and consequently gain access to sensitive user data.
Exploit Details
To exploit this vulnerability, a malicious app can be installed on the user's device. Once executed, a rogue app can create an intent to query and receive information from the vulnerable component and obtain sensitive data by using the following code snippet:
// Exploit Code
Intent intent = new Intent();
intent.setComponent(new ComponentName("com.transsion.carlcare", "com.transsion.carlcare.activity.MainActivity"));
startActivityForResult(intent, REQUEST_CODE);
This code snippet essentially sends an intent to the Carlcare Main Activity and returns the result as "startActivityForResult". The sensitive data returned from the vulnerable component can then be captured by the rogue app, potentially leading to information leakage.
Conclusion
CVE-2025-0590 is a severe vulnerability in the Transsion Carlcare mobile app, which leaves users of supported devices at great risk of information leakage. Users are strongly advised to update to the latest version of the app, which addresses this vulnerability.
Developers should take note of the proper permission settings for components in the AndroidManifest.xml configuration file. Component exposure should be set to "false" by default and, if necessary, protected using additional security measures like custom permission settings or the use of digital signatures for authenticated access.
Timeline
Published on: 01/20/2025 07:17:10 UTC
Last modified on: 03/24/2025 18:15:22 UTC