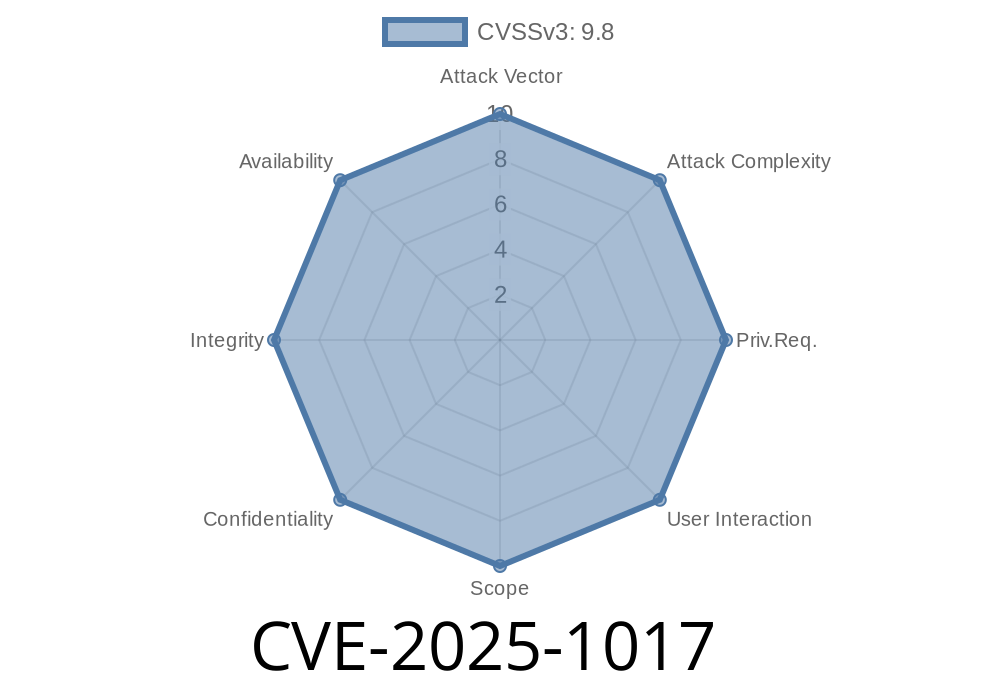
A recently disclosed vulnerability, CVE-2025-1017, affects multiple versions of Mozilla's popular software, including Firefox 134, Thunderbird 134, Firefox ESR 128.6, and Thunderbird 128.6. The issue involves memory safety bugs that could, under certain circumstances, allow an attacker to execute arbitrary code. This means someone could gain control over your computer just by visiting a malicious website or opening a crafted email.
If you’re running any version of Firefox before 135 or Thunderbird before 135 (or ESR before 128.7), it’s time to update immediately.
What is CVE-2025-1017?
CVE-2025-1017 refers to a set of memory safety flaws present in both Firefox and Thunderbird. Memory safety bugs often result in accidental memory corruption. Many times, these result in crashes. But sometimes, with enough tinkering by attackers, these issues open the door to running malicious code on your system – a much bigger problem!
Mozilla’s security advisory (replace XX with latest published number relevant to this CVE) gives an overview but doesn't share technical proof-of-concept details. Still, enough information is public for us to understand the risk.
How Do Memory Safety Bugs Work?
At a high level, these bugs usually occur when the program mishandles memory – for example, by reading or writing outside the boundaries of a buffer (array). This can crash the application or, in a worst-case scenario, let an attacker run their own code.
Here's a simplified example in C++ (this is an illustrative sample, not Mozilla’s actual code)
void vulnerable_function(const char* user_input) {
char buffer[256];
strcpy(buffer, user_input);
// If user_input is longer than 255 characters, we overwrite memory!
}
If user_input is too long, it overwrites memory it shouldn’t touch. In a browser or email client, attackers can craft web pages or emails to trigger these conditions, potentially changing the flow of the program.
The real bugs in Firefox and Thunderbird are more complex, often related to mishandling during JavaScript processing, media decoding, or rendering emails.
According to Mozilla
> "Some of these bugs showed evidence of memory corruption and we presume that with enough effort some of these could have been exploited to run arbitrary code."
(Reference: Mozilla Security Advisories)
This means if an attacker can trigger these specific flaws reliably, they might be able to make your computer run malicious programs without your knowledge.
Find a Memory Corruption Vector: (e.g., via a specially crafted web page or email).
2. Trigger Out-Of-Bounds Write/Read: Overwrite memory with attacker-controlled data.
For example, using JavaScript to abuse a vulnerable object
// PoC: Try to trigger the bug (illustrative)
let arr = new Array(10);
arr.length = 100000; // artificially inflate length
// ...fill arr with crafted objects, triggering vulnerability in the engine...
This kind of scripting can sometimes hit the underlying memory flaw.
How to Stay Safe
Update Your Software!
For Thunderbird: Use Help > About Thunderbird to check for updates.
Always use the latest version. If you use *Firefox ESR* or extended support releases, double-check that you're at 128.7 or newer.
Additional References
- Mozilla Foundation Security Advisories (find the latest for each product)
- CVE-2025-1017 at NVD *(Link will go live after publication)*
- Mozilla Release Notes: Firefox
- Mozilla Release Notes: Thunderbird
Conclusion
CVE-2025-1017 is a high-impact set of bugs affecting millions of users. While no exploitation has been reported in the wild yet, these sorts of vulnerabilities are prime targets for attackers. Don’t wait – update all your Mozilla browsers and mail clients now.
Stay secure and always keep your software up to date!
Timeline
Published on: 02/04/2025 14:15:32 UTC
Last modified on: 02/06/2025 21:15:22 UTC