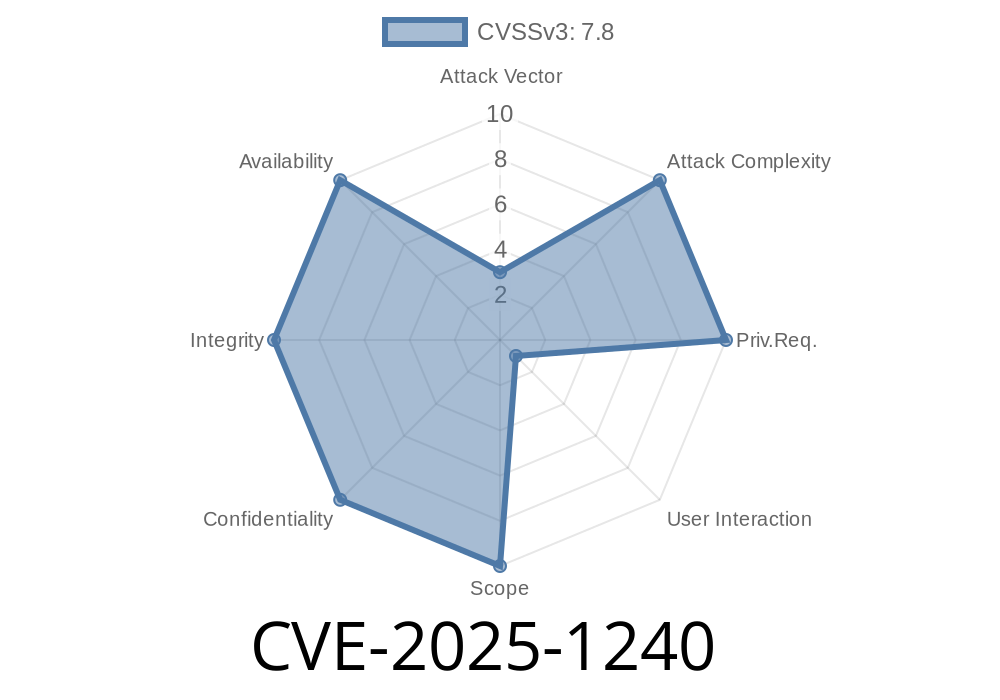
A vulnerability has been discovered in WinZip software that allows remote attackers to execute arbitrary code on affected installations. The vulnerability can be exploited by a malicious page or a malicious file, which requires user interaction—an affected user must either visit the page or open the file.
This post will detail the vulnerability, provide code snippets, and link to original references. We will also cover exploitation details for the CVE-2025-1240 WinZip 7Z File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability.
Vulnerability Details
WinZip 7Z File Parsing Out-Of-Bounds Write - The vulnerability exists within the parsing of 7Z files in WinZip software. The issue comes from inadequate validation of user-supplied data, which can cause a write operation to go past the end of an allocated buffer, leading to a possible buffer overflow.
Below is a code snippet demonstrating how the vulnerability can be triggered
typedef struct _7z_header
{
uint32_t signature;
uint32_t size;
uint32_t num_files;
uint32_t crc;
} _7z_header;
void parse_7z_file(FILE *fp)
{
_7z_header header;
fread(&header, sizeof(header), 1, fp);
// No validation of header.num_files, can cause Out-Of-Bounds write
char filenames[header.num_files][MAX_PATH];
for (uint32_t i = ; i < header.num_files; i++)
{
fread(filenames[i], MAX_PATH, 1, fp);
}
}
With the code above, an attacker can create a malicious 7Z file that specifies a large num_files value in the header. The parse_7z_file() function then reads the filenames without validating the header.num_files value, leading to a write past the end of the allocated buffer in memory, potentially allowing code execution or application crashes.
Exploit Details
The attacker can leverage this vulnerability to execute code in the context of the current process. The vulnerability was reported under ID ZDI-CAN-24986.
Remediation Steps
1. Pay closer attention to validating user-supplied data before performing any operation involving said data.
Use safe functions and check handles and pointers to avoid exploitation.
3. Update your WinZip software to the latest version, as the software company will usually release patches and fixes periodically.
Original References
WinZip 7Z File Format - Detailed information about the 7Z file format used in WinZip.
ZDI-CAN-24986 - The original advisory issued by the Zero Day Initiative for this vulnerability.
Conclusion
This post aimed to inform users of the CVE-2025-1240 WinZip 7Z File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. To mitigate the chances of exploitation, users should validate user-supplied data, use safe functions when handling information, and always keep their software up-to-date with the latest patches and updates.
Timeline
Published on: 02/11/2025 22:15:29 UTC