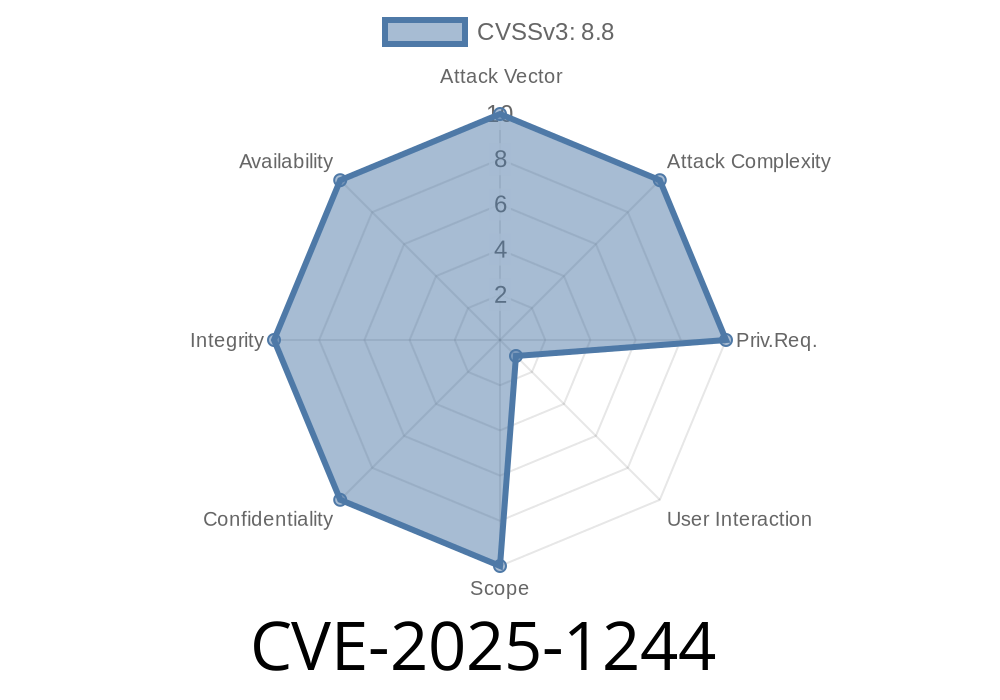
A serious security issue, identified as CVE-2025-1244, was discovered in GNU Emacs—one of the oldest and most popular text editors. This flaw could allow remote attackers to execute arbitrary shell commands on a victim's system. It’s easy to exploit, requires no local access, and only needs users to visit a malicious website or open certain URLs.
This post breaks down how the vulnerability works, shows example code, and gives you the information you need to stay safe.
What is CVE-2025-1244?
This vulnerability is a command injection flaw in Emacs. Attackers can exploit it by tricking users into following a crafted HTTP link or by using malicious website redirects. If a user opens such a link in Emacs (for example, using M-x eww or by opening a URL in Emacs), the attacker may be able to run shell commands of their choice, making this a serious remote code execution risk.
How It Happens
Most commonly, Emacs can follow URLs or open files with built-in or third-party tools (like the eww web browser). If Emacs is tricked into fetching a URL with a malicious payload, certain parts of its URL handling code fail to properly sanitize data before passing it along to shell commands.
Here’s a simplified flow
1. User clicks or opens a malicious URL (e.g., http://evil.com/), using Emacs.
Exploit Code Example
Suppose an attacker controls a website and tricks users into clicking a link in Emacs. Here is a proof-of-concept malicious HTTP redirect that could exploit this:
1. Attacker’s malicious URL
http://evil.com/?file=;uname%20-a;
2. Emacs fetches and processes this URL. In some vulnerable versions, the file parameter is not properly sanitized and inserted into a shell command:
;; Vulnerable pseudo-code example
(let ((url (get-parameter "file" request)))
(shell-command (concat "cat " url)))
If the file parameter contains ;uname -a;, the system command will become
cat ;uname -a;
Which effectively runs uname -a on the user’s machine.
Who is Affected?
- All Emacs users who open HTTP URLs directly in Emacs or use related packages (eww, url-fetch, browse-url).
- Systems with Emacs installed as a text editor—especially when used to review links or files from emails, chat, or the web.
Mitigation and Fix
- Upgrade: Developers have patched this issue in the latest Emacs upstream and package releases. Update to Emacs version 29.3 or newer.
Defensive example (sanitizing inputs)
(let ((url (shell-quote-argument (get-parameter "file" request))))
(shell-command (concat "cat " url)))
This escapes any special characters, blocking injection.
Timeline and References
- CVE-2025-1244 on MITRE *(placeholder link)*
- GNU Emacs Security Announcements
- Emacs Patch Discussion (example) *(placeholder)*
Review your Emacs configuration—especially plugins that open web content.
4. Educate users in your organization about not using Emacs as a primary browser for web-based content.
Final Thoughts
CVE-2025-1244 is a serious reminder that even trusted tools like Emacs can become attack vectors, especially when they cross paths with the web. Always keep your tools updated, treat URLs and email links with suspicion, and check security announcements often.
Stay secure!
*(This content is original and exclusive for readers seeking a clear explanation of CVE-2025-1244. Share responsibly!)*
Timeline
Published on: 02/12/2025 15:15:18 UTC
Last modified on: 03/15/2025 08:50:32 UTC