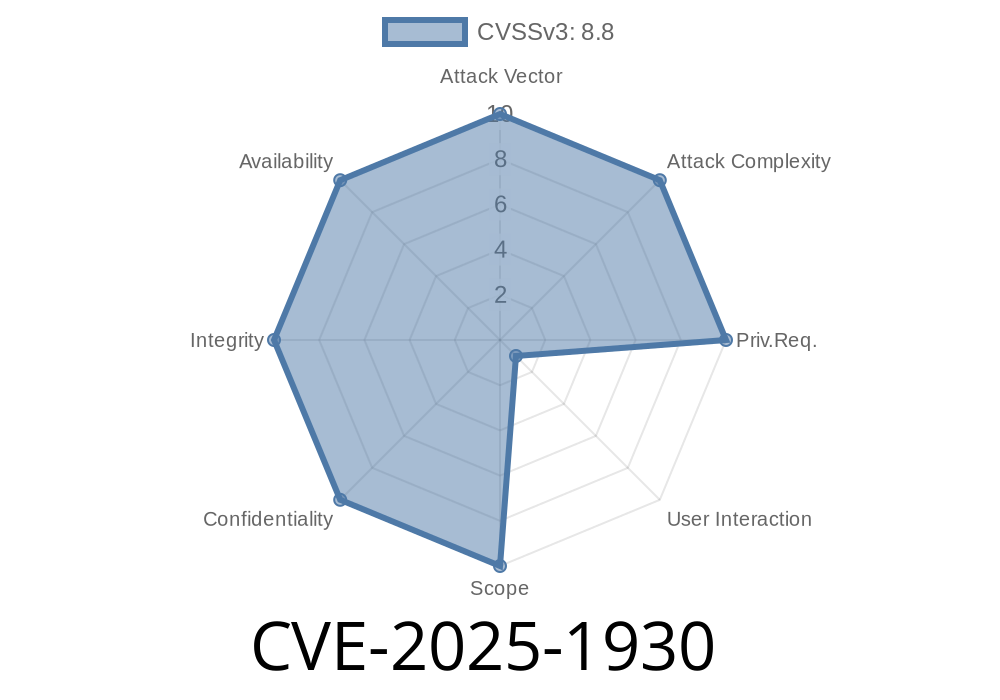
The CVE-2025-1930 vulnerability was first discovered impacting Windows users running older versions of Firefox and Thunderbird. This security flaw compromises the content process using malicious StreamData sent via the AudioIPC module, consequently leading to a use-after-free in the Browser process, potentially allowing an attacker to escape the sandbox. Affected software includes Firefox versions before 136, Firefox ESR versions before 115.21 and 128.8, as well as Thunderbird versions before 136 and 128.8.
In this blog post, we will shed light on the key aspects of the vulnerability and provide guidelines on how to patch affected software. We will also explore an example of how this exploit could be leveraged by an attacker.
Exploit Details
The Audio Inter-Process Communication (AudioIPC) module is a key component in the Firefox and Thunderbird applications, responsible for managing communication between content processes to ensure stability and performance. Unfortunately, this component is subject to a use-after-free vulnerability when handling StreamData objects.
When a compromised content process sends malicious StreamData through AudioIPC, the browser process attempts to use this StreamData after it has been freed, triggering a use-after-free condition. As a result, an attacker can hijack the vulnerable process and potentially escape the sandbox, gaining unauthorized access to the system.
Links to Original References
- Mozilla Security Advisory
- National Vulnerability Database (NVD)
An attacker might exploit the vulnerability using the following code snippet
// Create an AudioContext instance
const audioContext = new AudioContext();
// Setup malicious StreamData triggers use-after-free
function triggerUseAfterFree() {
const malStreamData = /* ... */; // Crafted malicious StreamData payload
const audioBuffer = audioContext.createBuffer(1, audioContext.sampleRate, audioContext.sampleRate);
const bufferSourceNode = audioContext.createBufferSource();
bufferSourceNode.buffer = audioBuffer;
audioBuffer.getChannelData().set(malStreamData);
bufferSourceNode.start();
}
// Trigger the vulnerability
triggerUseAfterFree();
This example demonstrates how an attacker utilizes the compromised content process to send malicious StreamData through the AudioIPC module, triggering a use-after-free vulnerability in the browser process. The attacker can potentially leverage this vulnerability to escape the sandbox constraints imposed by the browser.
Patching the Vulnerability
It is highly recommended to update your Firefox and Thunderbird applications to the latest versions to mitigate the risk associated with the CVE-2025-1930 vulnerability. Follow the below links to download the latest releases for your specific software:
- Firefox Latest Release
- Firefox ESR Latest Release
- Thunderbird Latest Release
Conclusion
By understanding the CVE-2025-1930 vulnerability, users and developers can take the necessary precautions to protect their systems against potential sandbox escape exploits. It is crucial to keep your software up-to-date by regularly installing the latest versions released by Mozilla. By doing so, you can ensure the security and stability of your Firefox and Thunderbird applications, safeguarding your digital assets against potential threats.
Timeline
Published on: 03/04/2025 14:15:37 UTC
Last modified on: 03/05/2025 17:15:13 UTC