---
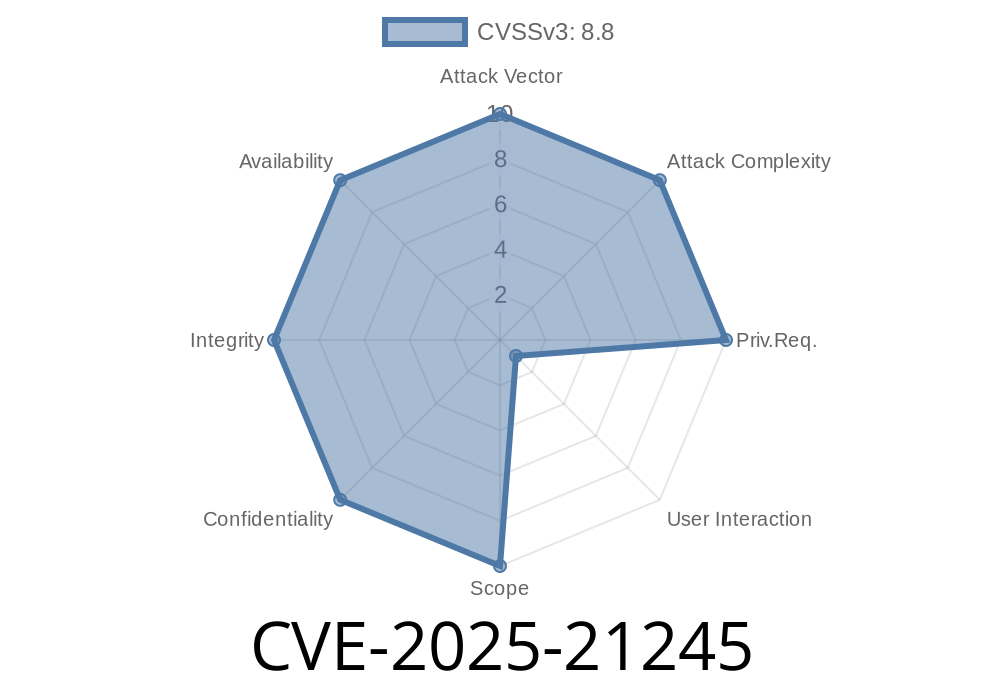
Microsoft has recently disclosed a critical vulnerability, CVE-2025-21245, which affects the Windows Telephony Service (TAPI). This post will break down what the vulnerability is, how it can be exploited, and what you can do to stay safe. We'll also include a simple code snippet showing the core principle behind the exploit (for educational purposes only).
What is the Windows Telephony Service?
The Telephony Application Programming Interface (_TAPI_) in Windows is responsible for handling telephony connections—like dial-up modems, VoIP apps, and remote assistance tools. By design, this service listens for requests and manages calls between hardware and software.
CVE-2025-21245: The Bug in Simple Terms
CVE-2025-21245 is a remote code execution (RCE) vulnerability within TAPI on several supported versions of Windows (including Windows 10, 11, and some Server versions).
An attacker can exploit this weakness by sending a specially crafted request to the telephony service, forcing it to execute malicious code in the context of the SYSTEM account. This gives the attacker full control of your computer.
How Does it Work?
The vulnerability exists because TAPI does not properly validate input (for example, when a remote device or application sends it commands). Attackers can abuse this with a specially crafted network packet or local API call.
Exploit Scenario
Let’s imagine a user is running an exposed telephony service (either on a workstation, remote desktop, or exposed via VPN). An attacker can send a particular malformed message that causes a buffer overflow (i.e., more data than the service can safely process). This overflow can overwrite memory, allowing the attacker to execute arbitrary code.
Exploit Details (Conceptual Code)
This is a simplified Python example of how an attacker might send a crafted request triggering a vulnerability.
Warning: Do not use this code for malicious purposes. It is for educational use only!
Suppose the vulnerable part listens on a local named pipe or TCP port. Here’s what a fake exploit might look like:
import socket
TARGET_IP = '192.168.1.100'
TARGET_PORT = 172 # (example port; TAPI doesn’t usually listen directly, but for demo)
# Build a malicious payload – overlong input to cause buffer overflow
malicious_payload = b"A" * 1024 + b"\x90" * 32 + b"\xcc" * 4 # NOP sled + possible shellcode
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((TARGET_IP, TARGET_PORT))
s.sendall(malicious_payload)
# The crafted payload will crash or hijack the telephony service
print("[*] Sent exploit payload")
Real-world exploits would need valid structure, exploit shellcode, and bypass any modern protections (ASLR, DEP, authentication). In practice, attackers would chain other vulnerabilities or use more advanced code.
Microsoft CVE page:
CVE-2025-21245 - Microsoft Security Update Guide
- Security researcher writeup (when/if available):
Google Project Zero - Windows Telephony Bugs
Telephony API documentation:
Microsoft Docs - TAPI Reference
How To Protect Yourself
- Update Windows: Microsoft has released patches. Run Windows Update and install the latest security fixes (especially dated June 2025 or later).
Restrict network access: Block unnecessary inbound connections to services you do not use.
- Monitor for unusual activity: Look for unexplained telephony service crashes or unknown processes.
Disable Telephony if not needed:
Go to Services (services.msc), find _Telephony_, and disable it if your environment doesn’t need it (test first).
Final Thoughts
CVE-2025-21245 shows how even old, rarely used services like Windows Telephony can put modern systems at risk if left unpatched. Always keep your software up-to-date and review the services running on your machines. The best defense is knowledge and regular maintenance!
References
- Microsoft CVE-2025-21245 Official Page
- TAPI Developer Documentation
Timeline
Published on: 01/14/2025 18:15:41 UTC
Last modified on: 02/21/2025 20:29:11 UTC