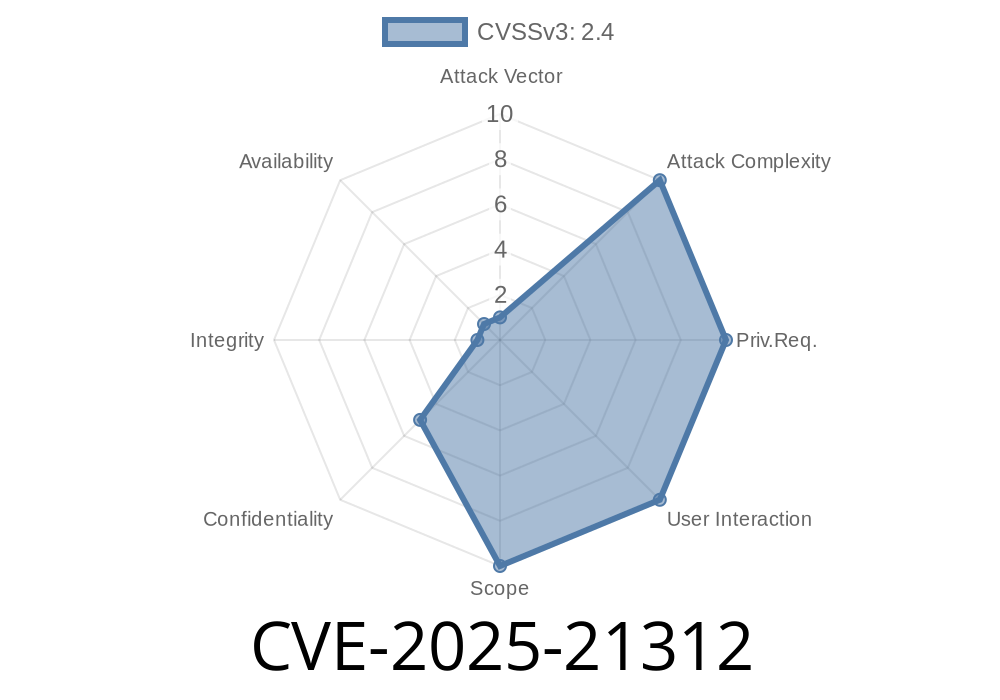
In early 2025, a new vulnerability surfaced in the Windows operating system, specifically affecting how the system handles information from smart card readers. Labeled as CVE-2025-21312, this info disclosure bug may allow attackers to gain sensitive data under certain conditions. If you rely on smart cards for authentication on your Windows machine, it’s crucial to understand what went wrong, how to spot if you're at risk, and what steps you can take to secure your environment.
What is CVE-2025-21312?
CVE-2025-21312 is a vulnerability in the way Windows manages data from smart card readers. A successful exploit could disclose sensitive information processed by the reader, such as card identifiers or even authentication/session data in some scenarios. This happens due to improper memory handling during the communication process between Windows and smart card reader drivers.
Windows Server 2019 and later (if smart card services are enabled)
Reference:
- Microsoft Security Advisory for CVE-2025-21312
- Security Update Guide: Windows Smart Card Services
How Does the Vulnerability Work?
Windows communicates with smart card readers using specific APIs and service layers. In the vulnerable implementations, when a user interacts with a smart card (for login, signing, or encryption), chunks of data from the card are read into computer memory. Under the hood, mishandled memory access or improper boundary checks could allow an attacker to retrieve small leaks of memory, including:
Here’s a simplified diagram of what happens
[Smart Card Reader] <---> [Windows Service] <---> [Application/User]
^----(Attacker reads disclosed buffer info)
Local Proof-of-Concept
An attacker would typically need local access or the ability to run code on the same machine (including via remote desktop or a compromised user account).
Here is a sample PowerShell snipplet that demonstrates how an attacker could access smart card buffer data using the Windows PC/SC API:
Add-Type -AssemblyName System.Security
$context = New-Object System.Security.Cryptography.CspParameters
$context.ProviderType = 1
$context.Flags = [System.Security.Cryptography.CspProviderFlags]::UseDefaultKeyContainer
try {
$store = New-Object System.Security.Cryptography.X509Certificates.X509Store "My", "CurrentUser"
$store.Open("ReadOnly")
foreach ($cert in $store.Certificates) {
if ($cert.HasPrivateKey -and $cert.Subject -like "*SmartCard*") {
Write-Output "Found a smart card: $($cert.Subject)"
# Potential buffer misuse here could allow leaked info
}
}
} finally {
$store.Close()
}
In a real exploit, an attacker could use a custom C/C++ or C# program to directly query memory shared between the smart card service and user processes, looking for uninitialized or over-read memory blocks.
Credential Theft: Extracted data could be used to clone a smart card or impersonate a user.
- Session Hijacking: Temporary authentication tokens or certificates leaked in memory could be re-used.
How to Protect Yourself
1. Update Windows
Microsoft has released a patch to address CVE-2025-21312. Always install the latest updates from Windows Update or your organization's WSUS infrastructure.
2. Limit Local Access
Restrict physical and remote access to machines using smart card authentication. Use group policies to limit who can log in locally.
3. Monitor Smart Card Service Logs
Look for unusual service activity:
- Smart card insertion/removal events
- Unusual service start/stop cycles
Multiple failed authentication attempts
4. Use Encryption and Session Isolation
Ensure your organization’s policies require encrypted smart card exchanges and isolate high-privilege sessions wherever possible.
Conclusion
CVE-2025-21312 serves as a reminder of the importance of keeping your system updated and monitoring sensitive authentication infrastructure. While the exploit requires some level of access, the risk is significant for organizations relying on smart cards for security. Always apply updates quickly and review your endpoint and authentication security regularly.
For more details and technical advisories, visit:
- Microsoft Official Advisory
- NVD Entry for CVE-2025-21312
Timeline
Published on: 01/14/2025 18:15:54 UTC
Last modified on: 02/21/2025 20:28:50 UTC