Published: June 2024
What is CVE-2025-21345?
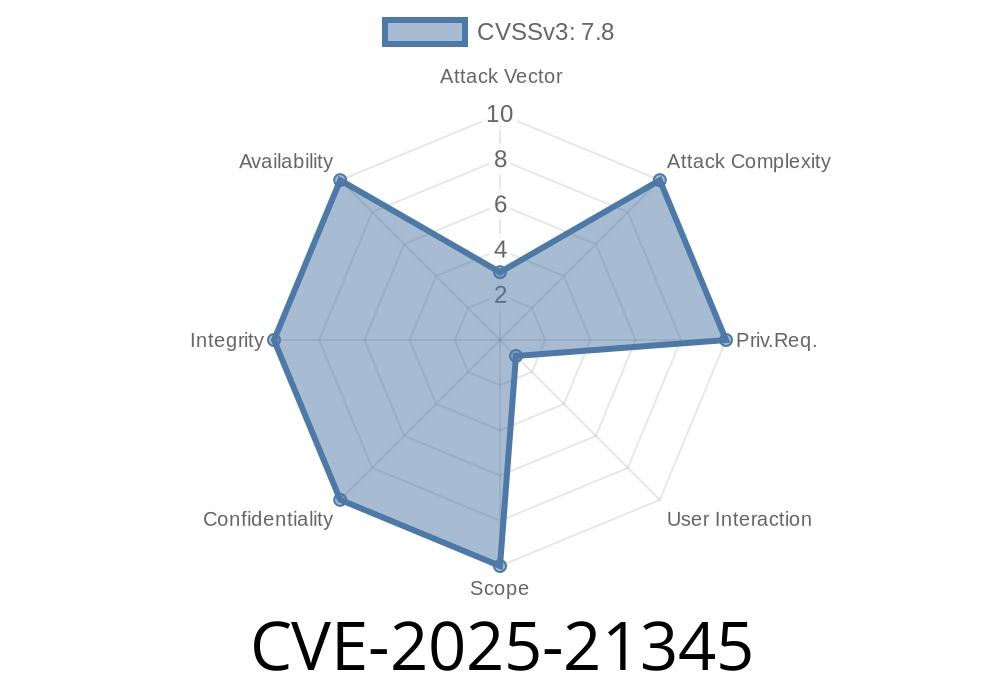
CVE-2025-21345 is a critical Remote Code Execution (RCE) vulnerability found in Microsoft Office Visio, discovered in May 2024 and patched by Microsoft in the June 2024 security update. This vulnerability allows an attacker to run arbitrary code on a victim's machine simply by tricking them into opening a maliciously crafted Visio document (.vsdx). The flaw is dangerous because it requires minimal user interaction and can be weaponized for malware delivery, ransomware deployment, or even complete system compromise.
This post provides you with an exclusive, easy-to-understand breakdown of the vulnerability, how the exploit works, code examples, and references to official advisories.
How Does the Vulnerability Work?
At the core of CVE-2025-21345 is improper input validation when Microsoft Visio processes certain malformed objects inside a .vsdx file. It allows an attacker to create a manipulated Visio file so that when an unsuspecting user opens it, Visio executes embedded attacker-controlled code.
Attack Scenario
1. Attacker crafts a malicious .vsdx file, embedding exploit code in an object (e.g., an OLE or macro-enabled shape).
Victim opens the file in Microsoft Visio.
4. Hidden code executes with the current user's privileges, potentially taking full control of the system.
Proof-of-Concept (PoC) Code Snippet
Below is a simplified demonstration (for educational purposes) on how an attacker might embed malicious code in a Visio file using VBA macros. Note: Real-world attacks are more sophisticated, often not using macros (which can raise suspicion), but leveraging object deserialization or buffer overflow techniques. This example is for awareness only.
Malicious VBA macro snippet
' Save this as ThisDocument in a Visio project
Private Sub Document_DocumentOpened(ByVal doc As IVDocument)
' This code runs automatically when the document opens
Shell "cmd.exe /c calc.exe", vbHide ' Launches calculator as a benign PoC
End Sub
Distribute to target.
Note: Actual exploitation may leverage encoding attack code in XML parts of .vsdx files, or using malformed OLE objects to bypass macro warnings.
No Advanced Privileges Needed: Simply tricking a user to open a file is enough.
- Common in Spear Phishing: Visio files are considered trustworthy in many organizations, making them perfect carriers for malware.
- Potential for Full System Compromise: If the victim has admin rights, attackers may gain total control.
Mitigation and Protection
Microsoft Patch:
Official advisory:
➡️ Microsoft Security Update Guide - CVE-2025-21345
Exploit Details (Technical Breakdown)
The attacker’s specially crafted Visio document exploits a memory corruption bug in the function responsible for processing embedded OLE objects. When the Visio process opens the document, malformed fields cause a heap overflow, which then can be used to overwrite the instruction pointer (EIP/RIP). If weaponized correctly, the attacker can redirect execution to their payload.
Example of (simplified) structure
<visioDocument>
<Shapes>
<Shape>
<!-- Malformed OLE object embedded here -->
<ForeignData Format="Link"> <!-- Faked link causes overflow -->
<![CDATA[ ... attacker data ... ]]>
</ForeignData>
</Shape>
</Shapes>
</visioDocument>
While weaponizing, an attacker must craft precise values to bypass Visio’s format validation checks.
References & Further Reading
- Microsoft Security Update Guide - CVE-2025-21345
- NIST National Vulnerability Database - CVE-2025-21345
- How to Disable Macros in Microsoft Office
Summary
CVE-2025-21345 is proof that even specialized Office tools like Microsoft Visio can be an entry-point for attackers. Stay protected: update Microsoft Office, educate your team, and be careful with files from unknown sources.
If you want to learn more, or test your systems for similar vulnerabilities, check the official Microsoft updates and keep your eyes open for suspicious docs in your inbox!
Timeline
Published on: 01/14/2025 18:16:00 UTC
Last modified on: 02/21/2025 20:28:09 UTC