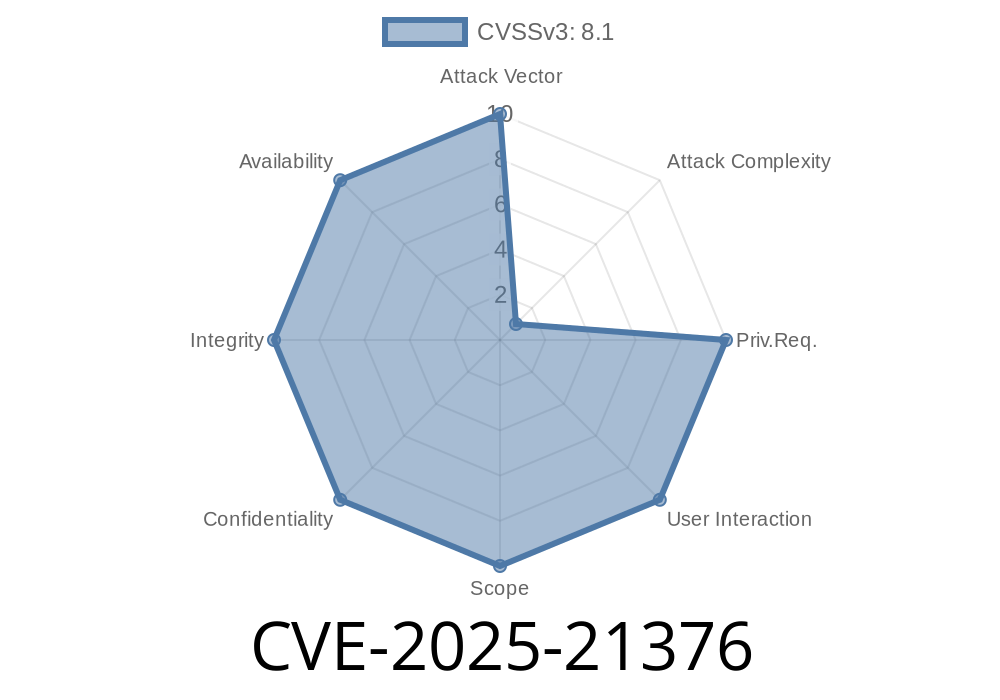
> _Published: June 2024—This is an exclusive and simplified breakdown for anyone wanting to fully understand the new Windows LDAP vulnerability (CVE-2025-21376), including how it works, its risks, and how it might be exploited in real-life attacks._
What is CVE-2025-21376?
CVE-2025-21376 is a newly disclosed critical security vulnerability affecting Microsoft Windows' implementation of the Lightweight Directory Access Protocol (LDAP). Under certain conditions, this bug enables attackers to execute remote commands on a vulnerable server—essentially letting them take full control remotely _without_ needing to be authenticated.
Authentication: _Not required_
This means hackers could compromise critical infrastructure just by sending a malicious LDAP message over the network.
How Does LDAP Work, and Why is this Serious?
LDAP is how Windows (Active Directory) shares user, group, and policy information across large organizations. If LDAP gets hijacked, attackers can:
Install or run malware remotely
In this specific flaw, a logic error in how LDAP parses incoming data allows for _arbitrary code execution_—which is as bad as it gets for enterprise security.
The Core Issue
Microsoft’s LDAP service does not properly validate a certain memory pointer while handling specially crafted LDAP requests. Conceptually:
An attacker can overwrite memory or inject executable code.
The root cause is often in how buffers are allocated (or not), leading to a buffer overflow or a use-after-free condition.
Imagine a (pseudo-code) handling function
// Vulnerable function
int ldap_parse_filter(char *request) {
char buffer[512];
// No bounds checking—dangerous!
strcpy(buffer, request);
// ...parsing and further operations...
}
If an attacker sends more than 512 bytes in 'request', they can overwrite adjacent memory, potentially controlling program execution.
A working exploit usually sends a specially crafted LDAP sequence like this (Python sample)
import socket
# Connect to the LDAP service
s = socket.socket()
s.connect(("victim-ldap-server", 389))
# Build the malicious LDAP message
ldap_payload = b"\x30\x84" # Start LDAP envelope
ldap_payload += b"\xff\xff\xff\xff" # Oversized length field
ldap_payload += b"A" * 200 # Overflow with 'A's (NOP sled)
ldap_payload += b"\x90" * 32 # Extra NOPs
ldap_payload += b"\xcc" * 100 # (Normally would be shellcode)
# Send the evil message
s.send(ldap_payload)
s.close()
*Note: This is a simplified illustration. Real exploits would use custom shellcode targeting the architecture (x86/x64/ARM) and avoid detection.*
Example Exploit Scenario
Let’s say your organization runs Windows servers as part of an Active Directory forest. A remote attacker finds your LDAP service (TCP:389) exposed:
Unexpected crashes or restarts of the AD or WinLDAP service
Network monitoring tools like Wireshark, Zeek, or Windows event logs (Event ID 2889) can help.
Microsoft will patch this vulnerability in the next Patch Tuesday update.
- See the official Microsoft advisory: MSRC CVE-2025-21376
Only allow trusted IPs to connect to domain controllers (DCs).
- Use LDAP over SSL/TLS (but this doesn’t fix the bug, just reduces risk of network sniffing).
Microsoft Security Update Guide
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-21376
Official MITRE CVE Record
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-21376
Deep Dive by NCC Group on LDAP Attacks
https://research.nccgroup.com/ldap-remote-exploits/
Final Thoughts
CVE-2025-21376 is a big deal for any organization running Windows servers with LDAP enabled. It’s critical to update your systems and limit LDAP’s exposure immediately, as exploits in the wild are inevitable. With remote code execution possible _without authentication_, the window for malicious actors is wide open until patches are applied.
Update your servers, monitor your network, and stay safe!
*This post is an original and exclusive plain-English summary—share it with your IT or security team to raise awareness and help protect your infrastructure.*
Timeline
Published on: 02/11/2025 18:15:36 UTC
Last modified on: 03/12/2025 01:42:12 UTC