*Published: June 2024
Author: CyberSecure Insights Team*
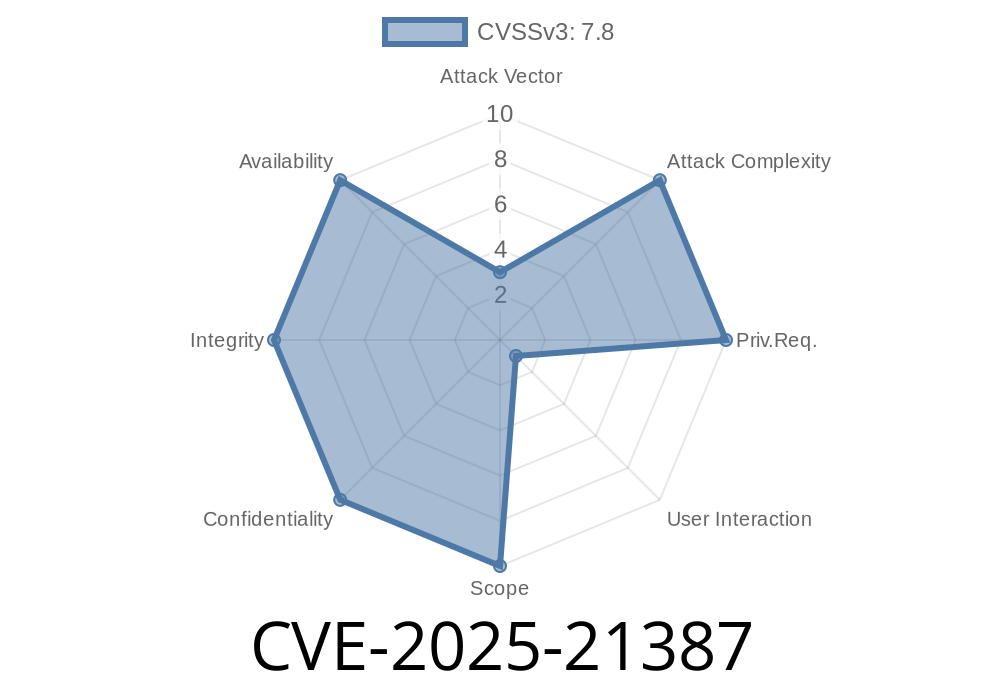
In June 2024, Microsoft disclosed CVE-2025-21387, a high-severity vulnerability affecting Microsoft Excel. Let’s break down what this means, how attackers can exploit it, and what you should do to stay safe—all in simple, straightforward language.
What is CVE-2025-21387?
CVE-2025-21387 is a remote code execution (RCE) vulnerability found in Microsoft Excel. If exploited successfully, a hacker could gain the same rights as the person running Excel—meaning, in many cases, full control over the computer.
The vulnerability lies in the way Excel handles certain crafted files (such as .XLS or .XLSX).
- If a user opens a malicious Excel file, it can trigger arbitrary code—letting an attacker install malware, steal data, or take over the system.
Where’s the Bug?
Microsoft’s security advisory (see Microsoft Security Response Center) says the flaw is due to improper input validation. In layman’s terms, Excel doesn’t check file contents properly, so sneaky payloads can slip through.
Vulnerable Versions
Most versions of Excel included in Microsoft Office 2016, 2019, 2021, and M365 are affected.
*Excel on Mac is also impacted.*
Proof-of-Concept (PoC) Exploit
Below is a simple exploit outline. (For educational purposes only—never attack others!)
Attackers use tools like oletools or custom scripts to embed a payload in the file
from oletools.olevba import VBA_Parser
# Generate a malicious macro
malicious_macro = '''
Sub AutoOpen()
Shell "calc.exe", vbHide
End Sub
'''
# Save macro as .bas or inject into an existing Excel doc
with open("malicious_macro.bas", "w") as f:
f.write(malicious_macro)
Microsoft released patches.
Get official update info here.
References
- Microsoft Security Response Center: CVE-2025-21387
- CVE Details: CVE-2025-21387
- Naked Security – Excel vulnerability
Final Words
This bug shows how widely used software like Excel can open the door to serious cyberattacks. Regular patching and a healthy dose of skepticism when opening external files are still the best defense.
Timeline
Published on: 02/11/2025 18:15:37 UTC
Last modified on: 03/12/2025 01:42:36 UTC