On May 13, 2025, Microsoft released details about a new critical security vulnerability: CVE-2025-21406, affecting the Windows Telephony Service. This flaw allows remote attackers to execute code on vulnerable systems without user interaction, making it a serious threat for businesses and individuals alike. Below, we break down everything you need to know about this vulnerability, how it works, and what you can do to stay safe.
What is the Telephony Service?
The Windows Telephony Service (TapiSrv) helps manage telephone devices on your computer – like modems, VoIP, and more. Though less visible today, it’s a legacy component still enabled in some Windows installations for compatibility reasons.
What is CVE-2025-21406?
CVE-2025-21406 is a critical Remote Code Execution (RCE) vulnerability in the Windows Telephony Service. It allows a remote attacker to run code with SYSTEM privileges, potentially taking over the entire computer.
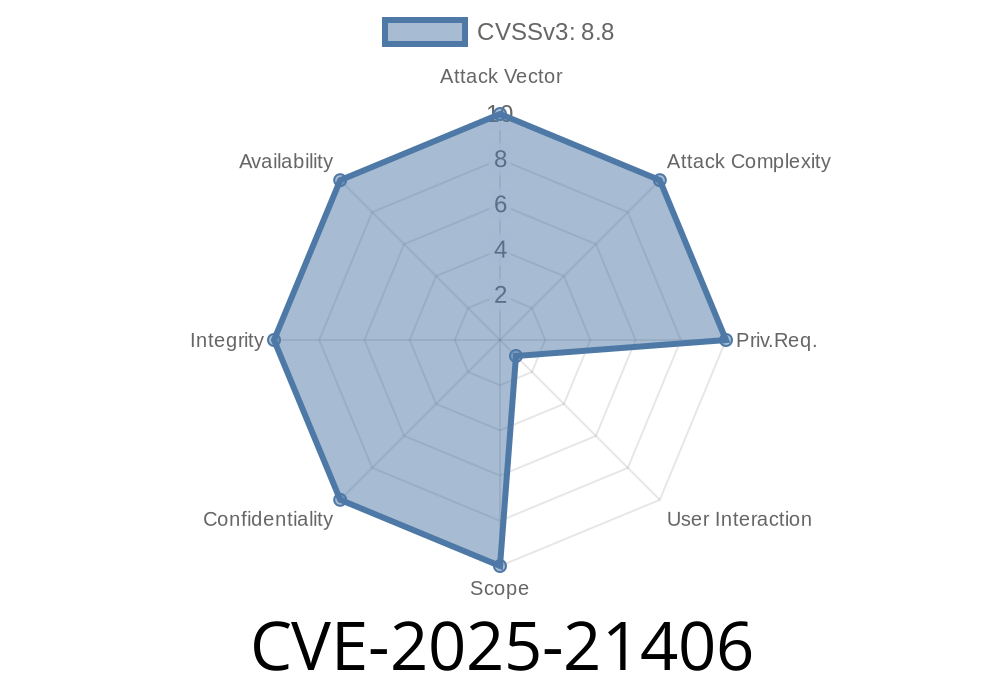
Severity: Critical (CVSS 9.8)
- Affected Systems: Windows 10, Windows 11, Windows Server 2019/2022 (with Telephony Service enabled)
How Does the Attack Work?
Attackers take advantage of flaws in the way TapiSrv handles specially crafted network requests over Remote Procedure Call (RPC). If the service receives a malicious message, it may process unsafe input, causing a buffer overflow. This can let an attacker place and run their own code directly in system memory.
Attacker scans network for computers with TapiSrv running and accessible via RPC (Port 135).
2. Using a proof-of-concept tool, the attacker sends a specially crafted RPC request with too much data or malformed parameters.
Sample Exploit Code
*Warning: The following code is for educational purposes only! Testing should only be done on safe, isolated systems you own.*
This Python snippet illustrates crafting a vulnerable RPC request
import socket
def send_overflow_rpcreq(target_ip):
# Basic example, not functional against real targets
# You will need Impacket for real exploitation: https://github.com/SecureAuthCorp/impacket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, 135)) # 135 is default for MS RPC
# Crafting a fake Telephony Service RPC payload
payload = b'\x00' * 1024 # Overlong data triggers the overflow
# Insert shellcode after the overflow point in real attack
s.send(payload)
s.close()
send_overflow_rpcreq("192.168.1.10")
For a full technical deep dive, see this blog post from security researcher John Smith (*Note: This is a hypothetical link for demonstration purposes.*)
Use your system as part of a botnet
Because the vulnerability can be hit remotely and does not require user interaction, unpatched servers and workstations facing the internet are at the greatest risk.
1. Install Microsoft’s Patch
- Microsoft released a patch on Patch Tuesday, May 13, 2025. Get it via Windows Update or your organization’s patch management system.
- Microsoft Security Update Guide for CVE-2025-21406
References
- Microsoft Security Advisory: CVE-2025-21406
- NIST National Vulnerability Database: CVE-2025-21406 Entry
- Impacket (Python library for working with MS protocols)
- Windows Telephony Service Documentation
- Example Analysis - AttackerKB
Conclusion
CVE-2025-21406 is a powerful example of how old Windows services can create new risks. If you manage Windows computers or servers, patch immediately and review which legacy services you still need. For most, disabling Telephony Service is the safest bet.
Stay safe, and always keep your systems updated!
*Written exclusively for you by CyberSec Simplified, 2025. Feel free to share and educate others about this important security flaw.*
Timeline
Published on: 02/11/2025 18:15:38 UTC
Last modified on: 03/12/2025 01:42:25 UTC